In a previous blog, we saw criminals distribute malware via malicious ads for Google Authenticator. This time, brazen malvertisers went as far as impersonating Google’s entire product line and redirecting victims to a fake Google home page.
Clearly not afraid of poking the bear, they even used and abused yet another Google product, Looker Studio, to lock up the browser of Windows and Mac users alike.
We describe how they were able to achieve this, relying almost exclusively on stolen or free accounts and leveraging Google’s APIs to create rotating malicious URLs for the browser lock.
All malicious activities described in this blog have been reported to Google. Malwarebytes customers were proactively protected against this attack via the Malwarebytes Browser Guard extension.
Malvertising {keyword:google)
The following image is a collage of malicious ads that all came from Google searches each consisting of two keywords: google {product}. They all tie back to the same advertiser, which we believe may be unaware that their account was compromised. In fact, we previously saw that same advertiser in two other unrelated incidents at the end of June 2024 for Brave (malware download) and Tonkeeper (phishing).
While brand impersonation is commonly done via tracking templates, in this instance the fraudsters relied on keyword insertion to do the work for them. This is particularly useful when targeting a single company and its entire portfolio. Notice how all the ads follow the same pattern with a display URL showing lookerstudio.google.com (a Google product also later abused in this scheme).
Shortly after we reported this initial wave of ads, we saw the same scammers (the final URL after clicking on the ad is also going to lookerstudio.google.com) register a new advertiser account. In this case, despite their identity not having been verified yet, their ad still showed up for a standard “google maps” search. This time, the ad’s display URL mirrors the product (maps.google.com):
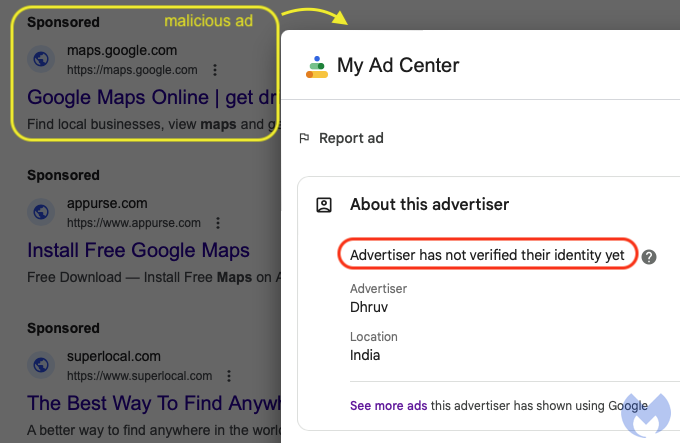
Fake Google Search page via Looker Studio
Originally intended as a tool to convert data into dashboards, the scammers are misusing Looker Studio to display a dynamically generated image instead. The image is stretched across the screen to give the illusion that you are at the Google home page, ready to make a new search.
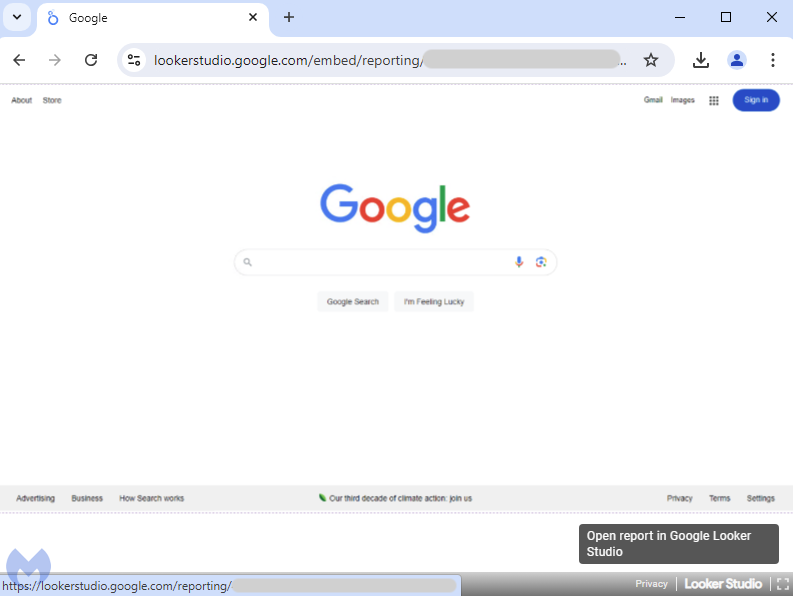
Opening Developer Tools in Chrome, we can see that the “Google search page” is indeed just one large image:

What’s interesting is how this image is used as a lure that requires some user interaction to trigger an action. Leveraging the Looker Studio API, the scammers are embedding a hidden hyperlink that will be launched as a new tab when a victims clicks on the image:

Tech support scam
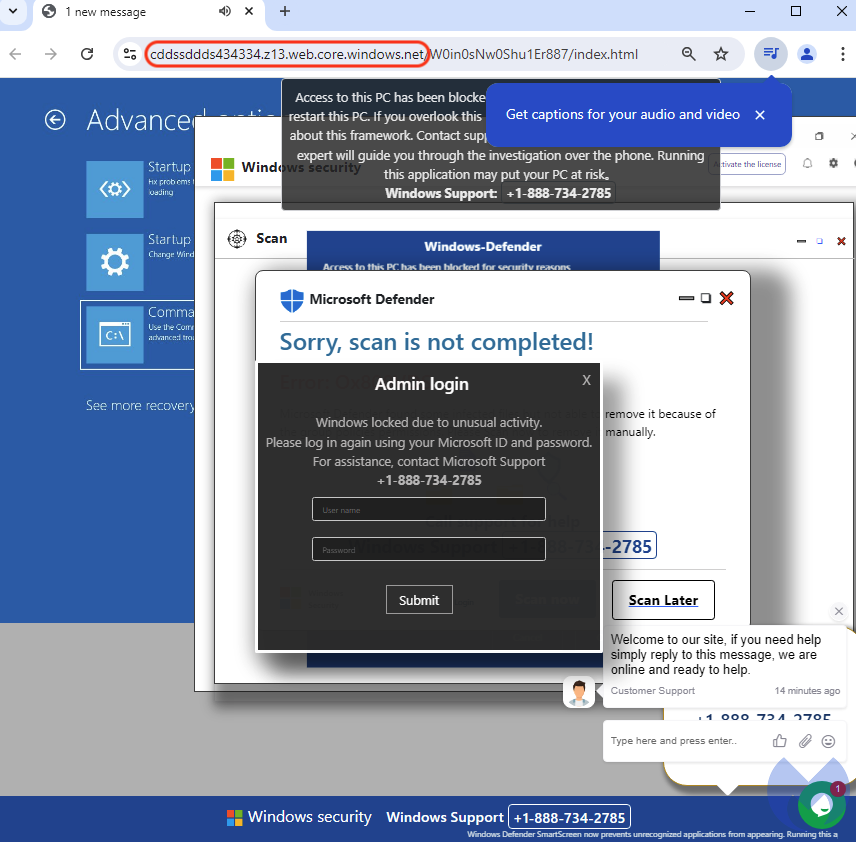
The embedded linkUrl cddssddds434334[.]z13[.]web[.]core[.]windows[.]net redirects to a fake Microsoft or Apple alert page that will attempt to hijack the browser by going in full screen mode and play a recording. These fake alerts are the most common way innocent people fall victims to tech support scams. In such a situation, many people will assume there is something wrong their computer and will follow the instructions they are given on screen.
Calling the phone number for assistance will kickstart a conversation with a call center often located overseas. Fake Microsoft or Apple representatives will persuade victims to buy gift cards or log into their bank account to pay for the ‘repairs’.

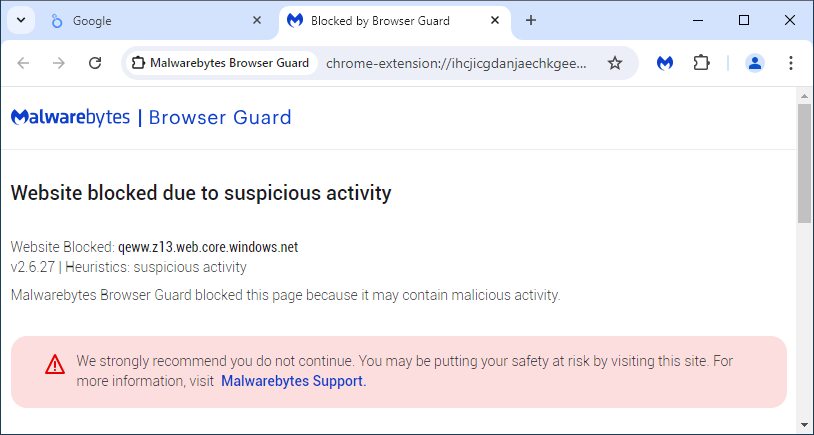
The scam URL is part of web[.]core[.]windows[.]net which belongs to Microsoft Azure and is commonly abused by scammers. In this particular instance, the Looker Studio API provides a new malicious URL (rotated at regular intervals) to make any blocking via conventional means futile.
Conclusion
As we saw in this blog, malicious ads can be combined with a number of tricks to evade detection from Google and defenders in general. Dynamic keyword insertion can be abused to target a larger audience related to the same topic, which in this case was Google’s products.
Finally, it’s worth noting that in this particular scheme, all web resources used from start to finish are provided by cloud providers, often free of charge. That means more flexibility for the criminals while increasing difficulty to block.
As we were investigating this campaign, we checked that Malwarebytes customers were protected. Despite the malicious URLs being hosted on Microsoft Azure and rotating regularly, Malwarebytes Browser Guard was already blocking this attack thanks to its heuristics engine.
Indicators of Compromise
Google advertiser accounts
08141293921851408385
Dhruv
06037672575822200833
Looker Studio URLs
lookerstudio[.]google[.]com/embed/reporting/fa7aca93-cabd-47bf-bae3-cb5e299c8884/
lookerstudio[.]google[.]com/embed/reporting/42b6f86d-2a06-4b38-9f94-808a75572bb8/
lookerstudio[.]google[.]com/embed/reporting/fbd88a24-af73-4c76-94dc-5c55345e291d/
