A threat actor compromised Ethereum’s mailing list provider and sent to over 35,000 addresses a phishing email with a link to a malicious site running a crypto drainer.
Ethereum disclosed the incident in a blog post this week and said that it had no material impact on users.
Attack details
The attack occurred on the night of June 23 when an email was sent from the address ‘[email protected]’ to 35,794 addresses.
Ethereum says that the threat actor used a combination of their own email address list and an additional 3,759 exported from the platform’s blog mailing list. However, only 81 of the exported addresses were previously unknown to the attacker.
The message lured recipients to the malicious website with an announcement of a collaboration with Lido DAO and invited them to take advantage of a 6.8% annual percentage yield (APY) on staked Ethereum.
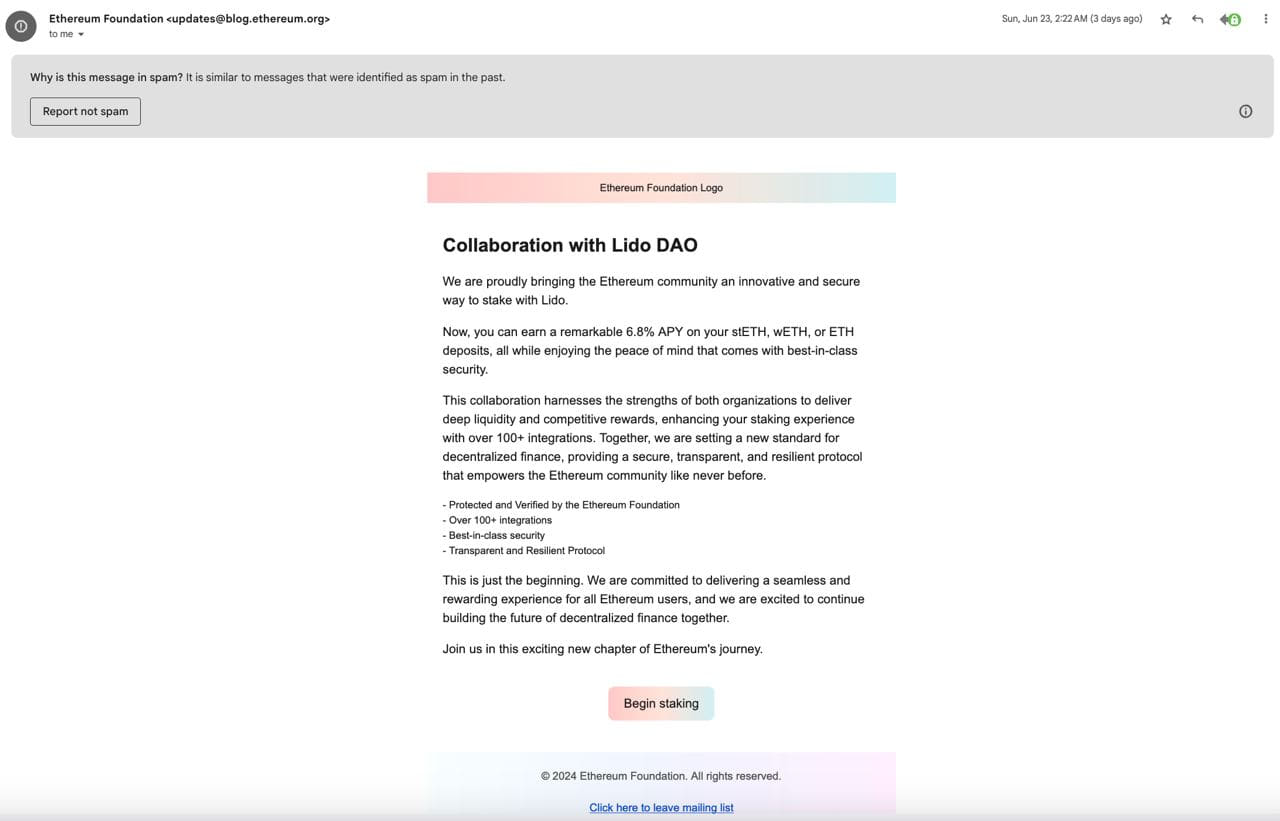
Source: Etheretum
Clicking on the embedded ‘Begin staking’ button to get the promised investment returns took people to a fake but professionally crafted website made to appear as part of the promotion.
If users connected their wallets on that site and signed the requested transaction, a crypto drainer would empty their wallets, sending all amounts to the attacker.
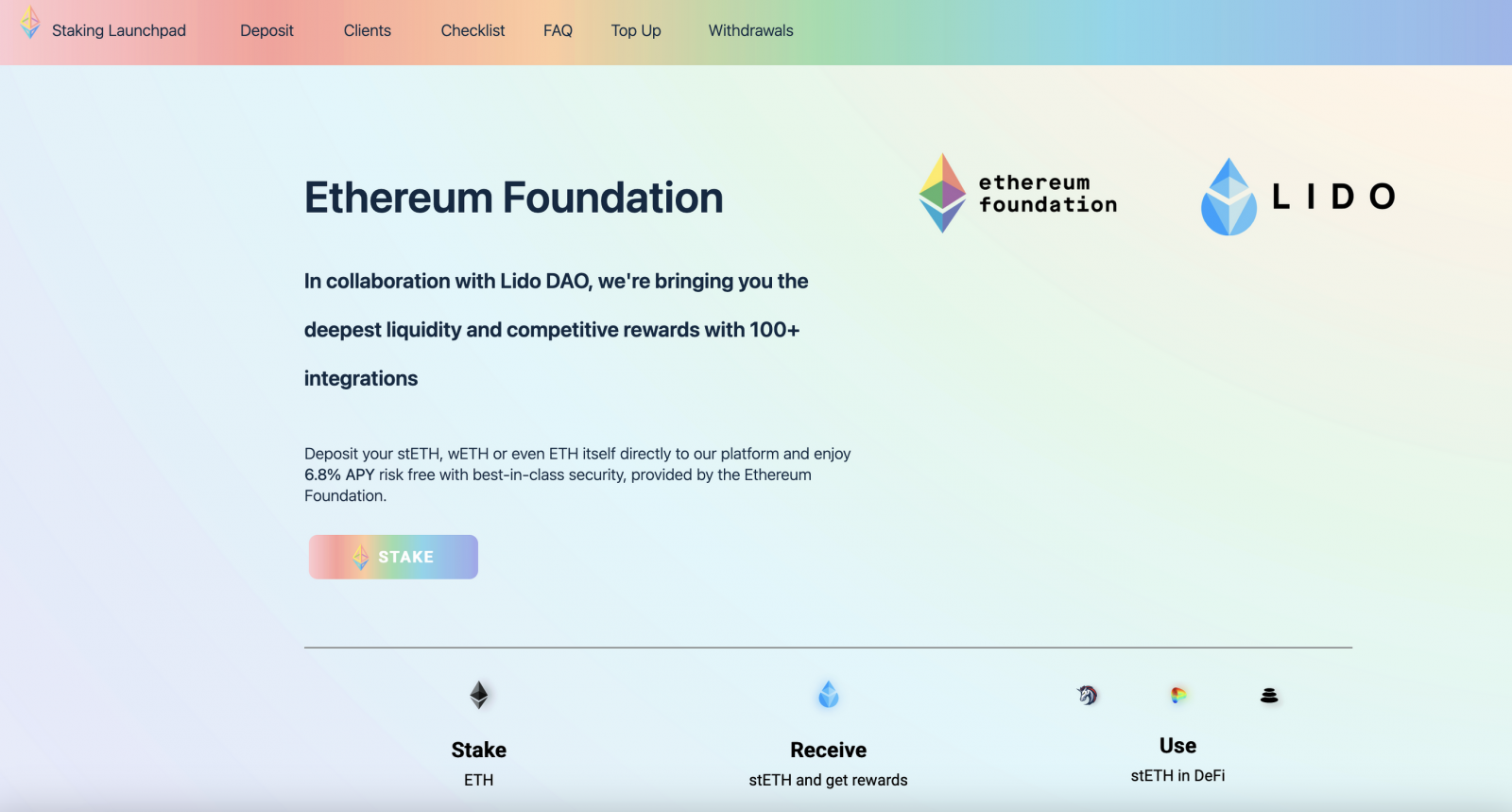
Source: Ethereum
Ethereum’s response
Ethereum says that its internal security team launched an investigation as soon as possible to identify the attacker, understand the attack’s purpose, determine the timeline, and identify the affected parties.
The attacker was quickly blocked from sending more emails and Ethereum took to Twitter to notify the community about the malicious emails, warning everyone not to click the link.
Ethereum also submitted the malicious link to various blocklists, which led to it being blocked by most Web3 wallet providers and Cloudflare.
On-chain transaction analysis showed that none of the email recipients fell for the trap during the campaign.
Ethereum concludes by saying it has taken additional measures and is migrating some email services to other providers to prevent such an incident from happening again.
