Hackers over the past six months have relied increasingly more on the browser-in-the-browser (BitB) method to trick users into providing Facebook account credentials.
The BitB phishing technique was developed by security researcher mr.d0x in 2022. Cybercriminals later adopted it in attacks targeting various online services, including Facebook and Steam.
Trellix researchers monitoring malicious activity say that threat actors steal Facebook accounts to spread scams, harvest personal data, or commit identity fraud. With more than three billion active users, the social network is still a prime target for fraudsters.

In a BitB attack, users who visit attacker-controlled webpages are presented with a fake browser pop-up containing a login form.
The pop-up is implemented using an iframe that imitates the authentication interface of legitimate platforms and can be customized with a window title and URL that make the deception more difficult to detect.
According to Trellix, recent phishing campaigns targeting Facebook users impersonate law firms claiming copyright infringement, threatening imminent account suspension, or Meta security notifications about unauthorized logins.
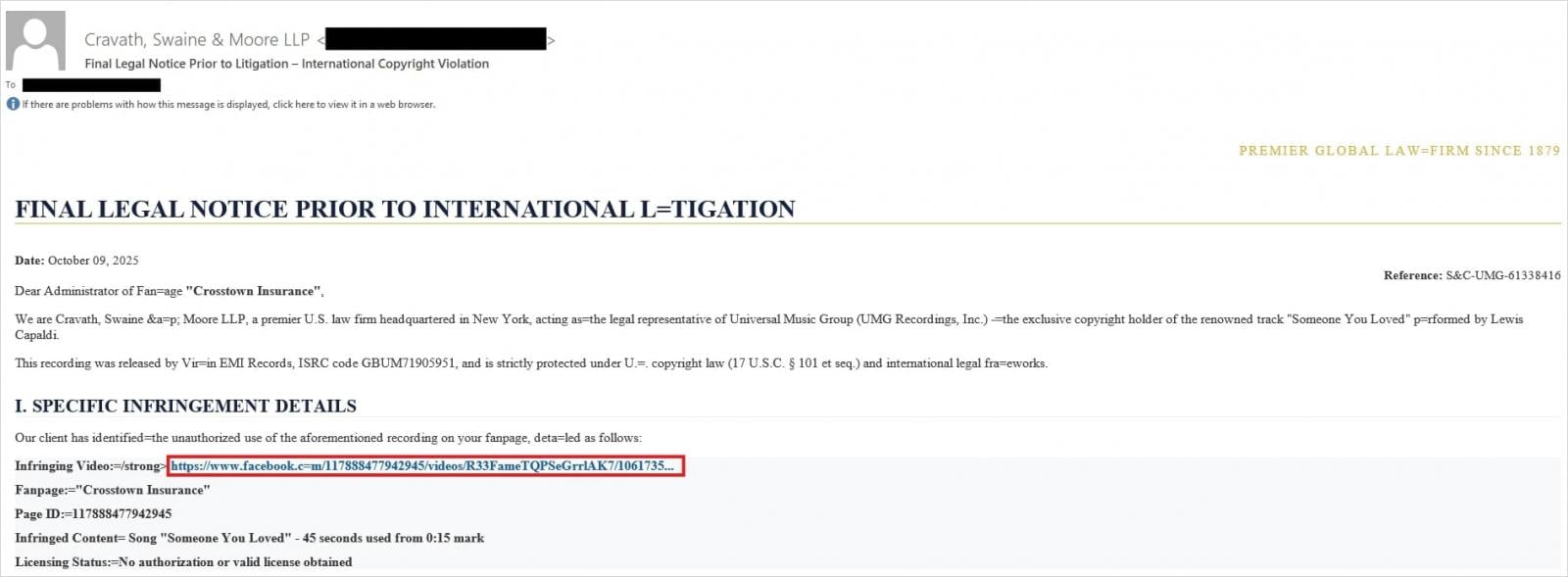
Source: Trellix
To avoid detection and to increase the sense of legitimacy, cybercriminals added shortened URLs and fake Meta CAPTCHA pages.
In the final stage of the attack, victims are prompted to log in by entering their Facebook credentials in a fake pop-up window.
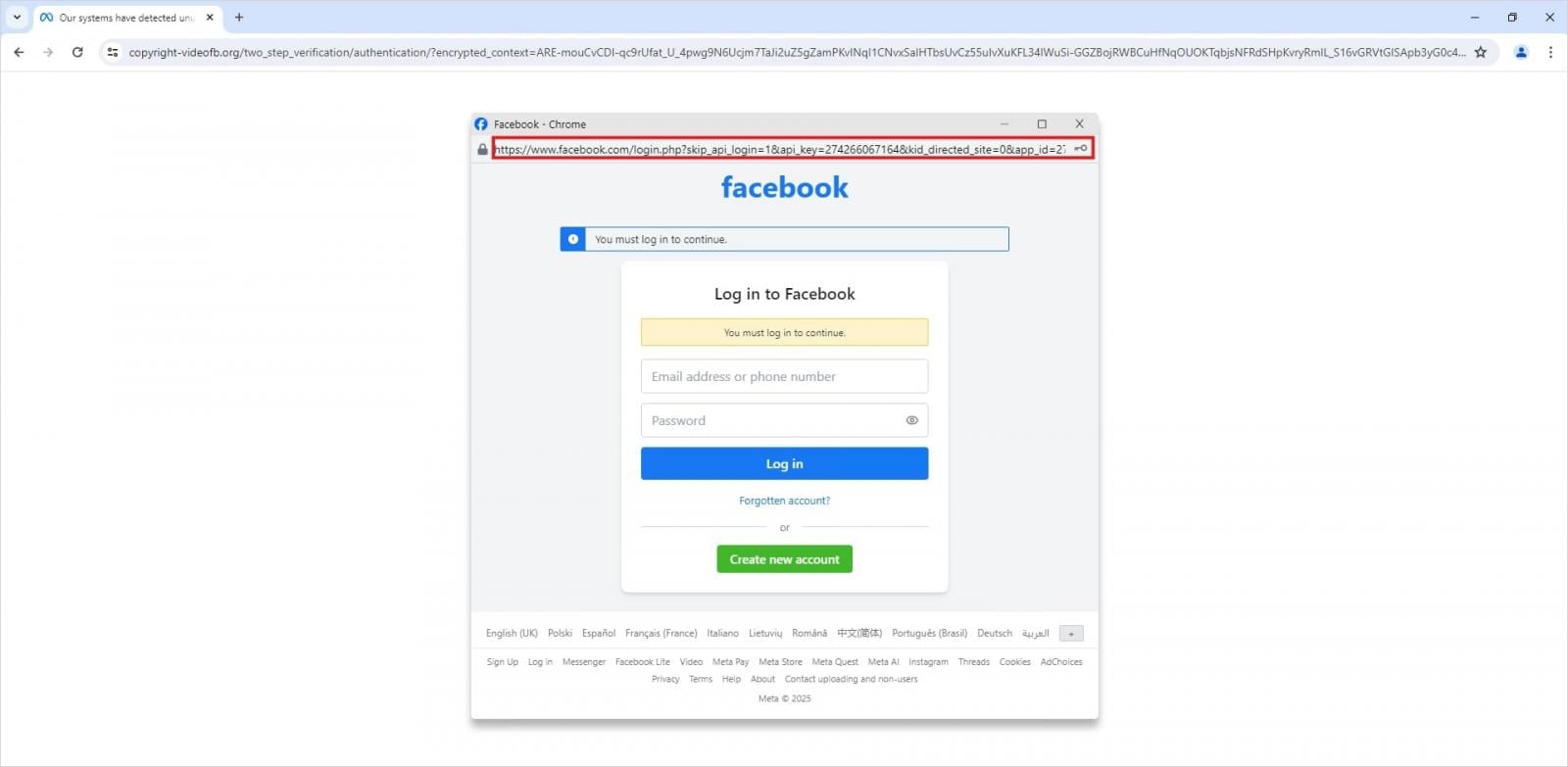
Source: Trellix
In parallel, Trellix discovered a high number of phishing pages hosted on legitimate cloud platforms like Netlify and Vercel, which mimic Meta’s Privacy Center portal, redirecting users to pages disguised as appeal forms that collected personal information.
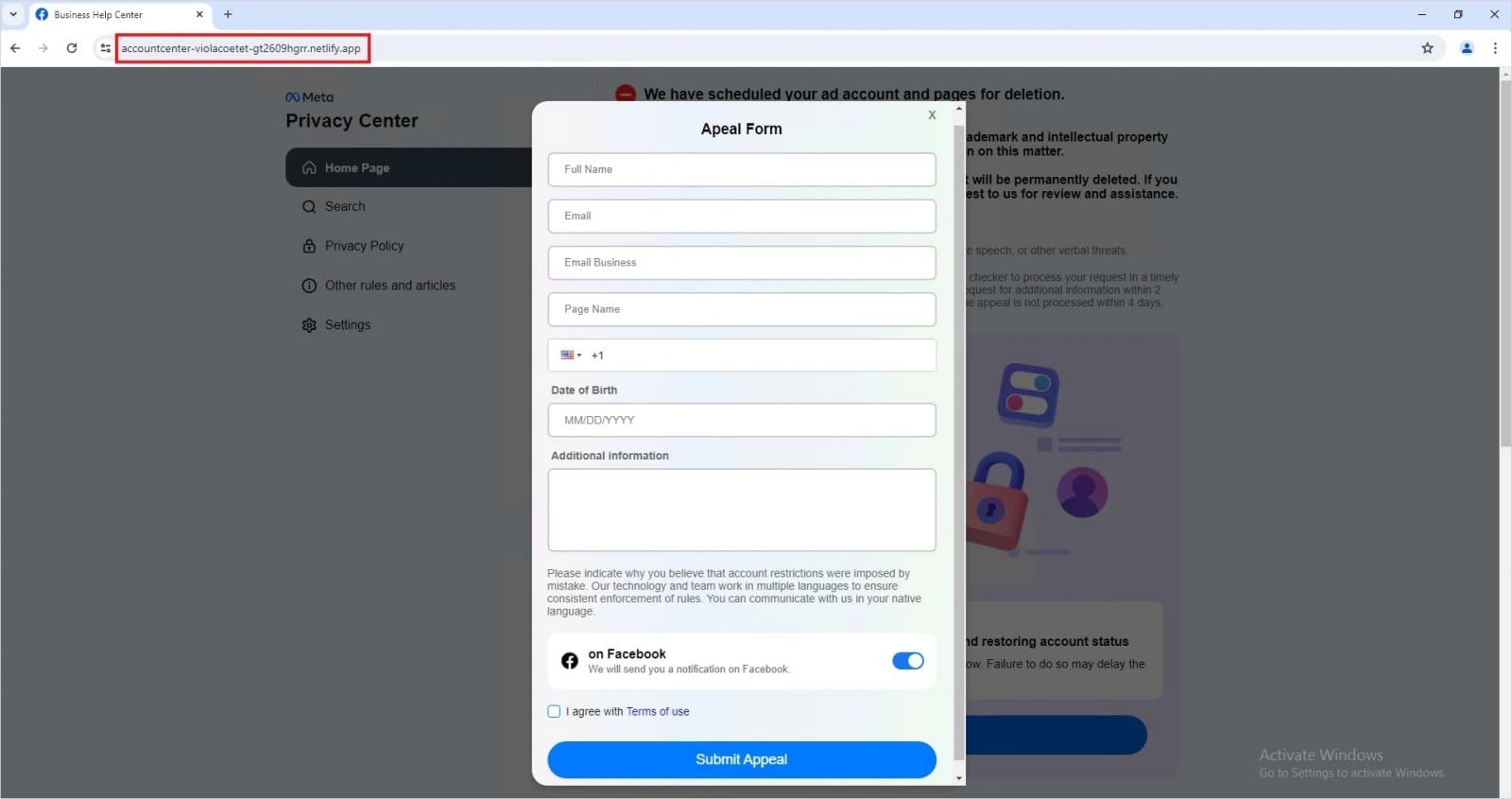
Source: Trellix
These campaigns constitute a significant evolution compared to standard Facebook phishing campaigns that security researchers typically observe.
“The key shift lies in the abuse of trusted infrastructure, utilizing legitimate cloud hosting services like Netlify and Vercel, and URL shorteners to bypass traditional security filters and lend a false sense of security to phishing pages,” reads the Trellix report.
“Most critically, the emergence of the Browser-in-the-Browser (BitB) technique represents a major escalation. By creating a custom-built, fake login pop-up window within the victim’s browser, this method capitalizes on user familiarity with authentication flows, making credential theft nearly impossible to detect visually.”
How to protect against BitM
When users receive account-related security alerts or infringement notifications, they should always navigate to the official URL in a separate tab instead of following embedded links or buttons on the email itself.
When prompted to enter credentials in login pop-ups, check if the window can move outside the browser window. iframes, which are essential for the BitB trick, are connected to the underlying window and cannot be pulled outside it.
The general recommendation for protecting access to your online accounts is to turn on the two-factor authentication protection feature. Although not infallible, this adds an extra layer of security against account takeover attempts even if credentials have been compromised.

It’s budget season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
