Suspected Russian attackers are targeting the hospitality sector with fake Booking.com emails and a fake “Blue Screen of Death” to deliver the DCRat malware.
The malware delivery campaign starts with phishing emails that feature room charge details in euros, which means that European organizations are likely targets.
But, according to Securonix researchers, the attackers’ are more than capable of adapting the campaign to target other industries.
The campaign
The attackers are sending out emails impersonating Booking.com:
The fake Booking.com email (Source: Securonix)
The “See Details” button/link in the fake reservation cancellation alert directs victims to a clone of the legitimate Booking.com site. JavaScript on the site shows a pop-up window, saying that the site is taking too long to load and urging the visitor to click on a button to refresh the page.
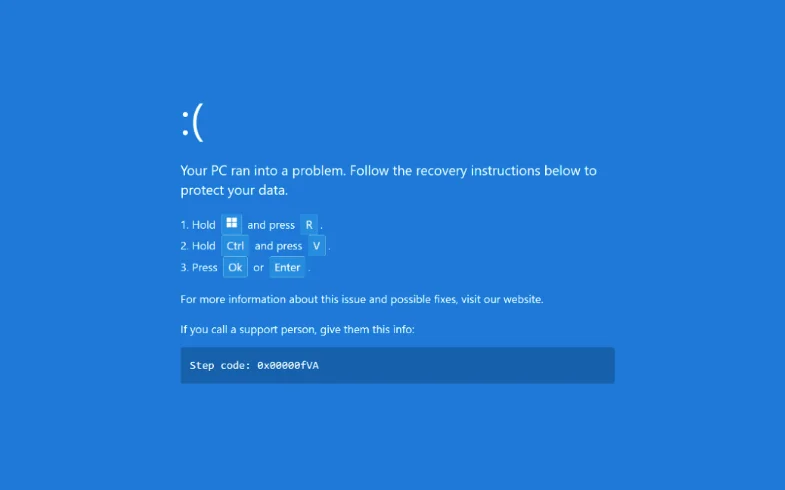
Those who do will see their browser enter full-screen mode and be presented with a fake Windows BSOD screen instructing them to “follow recovery instructions”:
The fake BSOD (Source: Securonix)
The provided steps make unsuspecting users open the Windows Run dialog box and paste and execute a malicious PowerShell command.
The command opens a decoy Booking.com admin page in the default browser, and secretly downloads a malicious project file (.proj) and compiles and executes it with Windows’ Microsoft Build Engine (MSBuild.exe).
“Threat actors use this technique to proxy execution through a trusted Windows utility,” the researchers explained. Once the project file is executed, it tries to covertly cripple Windows Defender, so it won’t notice when DCRat is finally downloaded and executed.
If the machine is run in Standard User mode, the project file will trigger repeated UAC prompts asking the user to allow it Admin privileges. If already in Admin mode, DCRat is immediately downloaded and executed, and an Internet Shortcut is created in the user’s Startup folder to ensure the malware runs automatically every time the user logs in.
DCRat can log keystrokes, drop additional malicious payloads, and allows persistent remote access to infected computers.
ClickFix social engineering and Living off the Land techniques
Securonix researchers correlated this attack activity with previous malware delivery campaigns that relied on HTML Application (.hta) files and Windows’ Microsoft HTML Application Host (mshta.exe) utility to execute the malicious payloads via embedded URLs.
“While effective in its simplicity, this earlier method was prone to detection. The ‘.hta’ and associated PowerShell scripts contained straightforward execution logic, typically a direct path to the RAT, which made them easy targets for antivirus vendors and automated security controls. The shift to the current MSBuild-based chain represents a strategic pivot towards more evasive, ‘Living off the Land’ techniques to bypass these defenses,” they explained.
The many variations of the ClickFix social engineering technique have proved to be very effective at tricking users into starting infection chains and evading defensive technologies.
The researchers have shared indicators of compromise and hunting queries, and are advising organizations to educate employees about the ClickFix tactic, monitor MSBuild.exe and other legitimate system binaries for unusual behavior, watch for the creation of suspicious file types in %ProgramData% and Internet Shortcut files in the Startup folder, and enable PowerShell logging.
Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!