We all know the feeling of waiting for a performance review. It can be a stressful time, and unfortunately, cybercriminals are now using that anxiety to their advantage. A recent report by AhnLab Security Intelligence Center (ASEC) has revealed a clever new email scam, which uses fake employee reports to trick people into installing dangerous software on their computers.
How the Trap is Set
The scam starts with an email that looks like it is coming from management or HR. The message mentions the performance reviews for October 2025 and claims that the company is planning to let some people go. To make it feel more urgent, the email tells the reader they need to check an attached file to see where they stand.
This is a classic social engineering trick involving scaring people into thinking their jobs are at risk. The attackers hope you will act quickly and open the attachment without thinking twice.
The Hidden Danger in the Attachment
The attached file, as per AhnLab’s report, is usually a zipped or compressed folder in which there’s a file named ‘staff record pdf.exe’. It is worth noting that if your computer is set to hide file extensions, this will look like a regular PDF document. However, in reality, it is an executable program. As soon as the user double-clicks this file, it launches malware known as Guloader.
This software is particularly tricky because it doesn’t immediately show up on your hard drive but hides in the computer’s temporary memory and reaches out to a Google Drive link to download the rest of its tools. By using a trusted site like Google Drive, the hackers can easily bypass basic security filters.
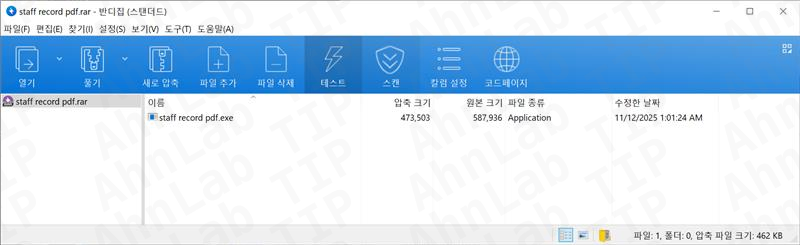
What Happens if You Get Infected?
The final goal of this attack is to install Remcos RAT. As soon as this virus is active, it connects back to the hacker’s home base. In this specific case, the malware was found communicating with a server at 196.251.116.219 using ports 2404 and 5000.
This connection allows hackers to watch you through your webcam, listen via your microphone, see every key you type, and even steal your saved passwords and browser history.
To protect yourself, always be wary of unexpected emails about dismissals or reports, especially if they have attachments. Also, make sure your computer is set to show full file extensions so you can spot an ‘.exe’ file pretending to be a document. Regularly changing your passwords and using extra login security can also help keep your data safe if a slip-up happens.
(Photo by Xavier Cee on Unsplash)
