Cybercriminals are exploiting Google Search Ads to distribute malware through deceptive landing pages that impersonate Apple’s official website design.
The malicious ads appear prominently in Google Search results when users search for “mac cleaner,” displaying trusted domains such as docs.google.com and business.google.com as landing pages.
However, clicking these ads redirects users to Google Apps Script macros pages disguised with Apple’s official branding, complete with replica navigation menus and interface elements.
Security researchers have identified a sophisticated campaign targeting macOS users who are searching for disk cleanup utilities, with ads redirecting victims to malicious Google Apps Script pages that host remote code execution payloads.
The pages contain deceptive instructions promising to help users check storage or free up disk space on their machines common maintenance tasks that lull users into a false sense of security.
Technical Analysis
The malware employs multiple obfuscation techniques to conceal its true purpose. The first variant uses a chain of commands that begins with social engineering messaging: “Cleaning macOS Storage…” followed by hidden Base64-encoded commands.
The sequence uses base64 -D to decode the hidden string, transforming gibberish into executable shell commands.
Additional deceptive messages like “Installing packages please wait…” create the illusion of legitimate system maintenance while the malware executes remotely.
The second payload variant is more direct in its approach, employing /bin/bash -c to execute commands passed as arguments.
Command substitution $(…) runs hidden instructions, while echo | base64 -d decodes obfuscated URLs that the curl -fsSL command retrieves from attacker-controlled servers.
This technique bypasses user visibility by using silent flags, downloading and immediately executing remote scripts without any system feedback.
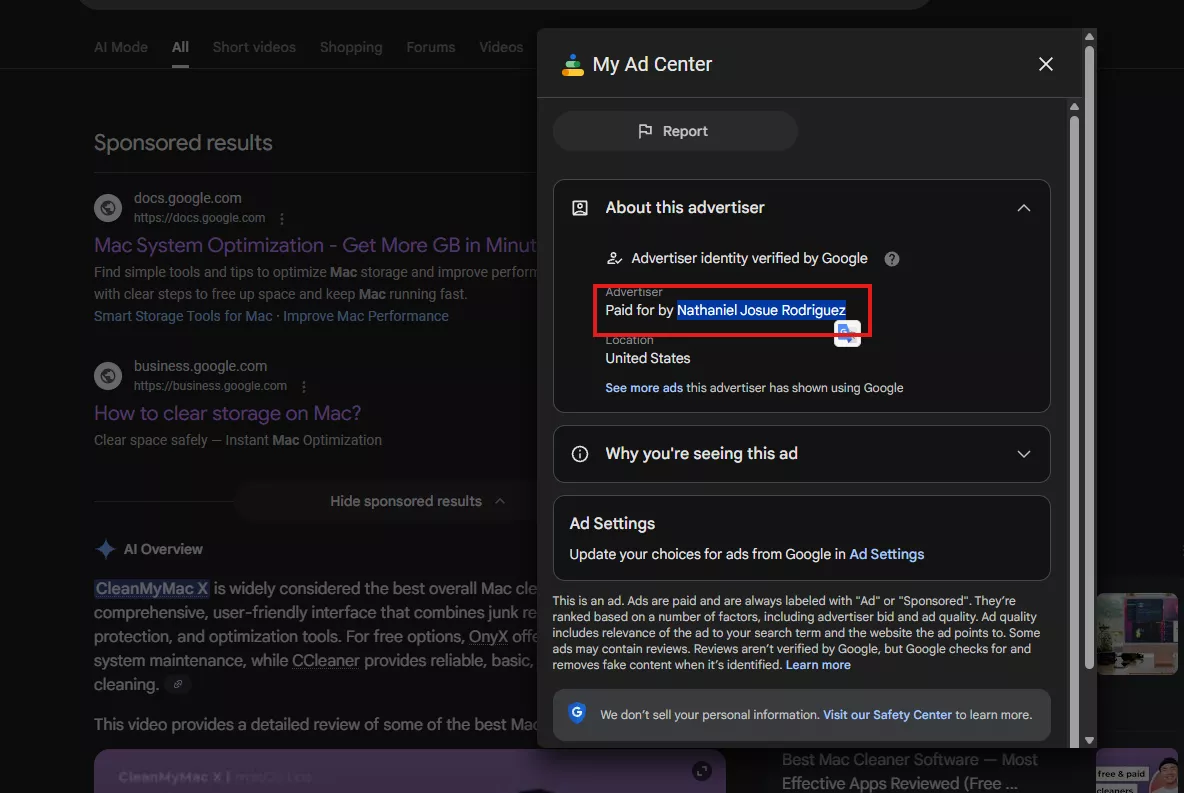
The first advertiser, Nathaniel Josue Rodriguez, shows legitimate ads in Google’s Transparency Center for unrelated domains.
Both payloads represent remote code execution (RCE) vulnerabilities that grant attackers complete control over infected systems.
Once executed, the scripts could install malware, steal SSH keys, add persistent backdoors, deploy cryptocurrency miners, exfiltrate sensitive files, or modify critical system settings. Users would remain unaware of the compromise due to the silent execution flags.
Compromised Ad Accounts
Investigation revealed that the Google Ads accounts behind this campaign appear to have been compromised.
Similarly, ads from Aloha Shirt Shop display a mix of legitimate and suspicious content through the same platform, suggesting credential compromise rather than intentional malicious campaigns by the account owners.
Researchers have reported these malicious ads to Google for removal and investigation. However, the campaign demonstrates how threat actors continue to exploit legitimate advertising platforms as distribution vectors, combining social engineering with technical obfuscation to compromise macOS systems at scale.
This pattern indicates attackers likely obtained access to legitimate, verified Google Ads accounts through credential theft, account takeover, or other unauthorized means.
Using established accounts allows threat actors to bypass initial verification checks and immediately distribute malware through trusted advertising channels.
Users should exercise caution when clicking sponsored search results, particularly for system maintenance utilities.
Verification through official Apple channels remains essential before executing any cleanup instructions. For legitimate macOS maintenance, users should consult Apple’s official support documentation or use established, reputable system utilities from verified sources.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
