U.S. law enforcement today seized the clear web domain of the notorious BreachForums (aka Breached) hacking forum three months after apprehending its owner Conor Fitzpatrick (aka Pompompurin), under cybercrime charges.
Hosted at Breached[.]vc, the domain now shows a seizure banner saying the website was taken down by the FBI, the Department of Health and Human Services, the Office of Inspector General, and the Department of Justice based on a warrant issued by the U.S. District Court for the Eastern District of Virginia.
Other law enforcement authorities worldwide were also part of this action, including the U.S. Secret Service, Homeland Security Investigations, the N.Y. Police Department, the U.S. Postal Inspection Service, the Dutch National Police, the Australian Federal Police, the U.K. National Crime Agency, and Police Scotland.
As is common with domain seizure messages, law enforcement displayed the logo for the site. However, in a unique display, law enforcement took an unconventional approach by also featuring handcuffs added to Pompompurin’s avatar in the seizure banner.
BleepingComputer has learned that law enforcement also seized the pompur[.]in domain, which was Pompompurin’s personal site, as part of this operation.
While BreachForums’ clear net domain has been seized, its dark web counterpart doesn’t yet display the seizure banner but instead shows a “404 Not Found” Nginx error.
FBI and Justice Department spokespersons were not immediately available for comment when contacted by BleepingComputer earlier today.
As first reported by DataBreaches.net, these domain seizures also led to the seizure of one of their own sites used to report on data breaches.
Breached vs. the new Breached
After the arrest of Fitzpatrick, Baphomet, the remaining administrator, attempted to maintain the functioning of the original domains. However, Baphomet believed that federal agents gained access to the servers, prompting the admin to shut down the site on March 20th.
Soon after, visiting the domain displayed “502 – Bad Gateway” error messages, indicating the site was now shut down.
In June, after rumors of Baphomet partnering with Shiny Hunters, a threat actor notorious for numerous data breaches, to relaunch BreachForums on a new domain, the old Breached domain began displaying a default ‘Welcome to nginx!’ page.
This indicated that someone else had gained control over the domains and was altering their content and configuration. Baphomet denied responsibility for these changes.
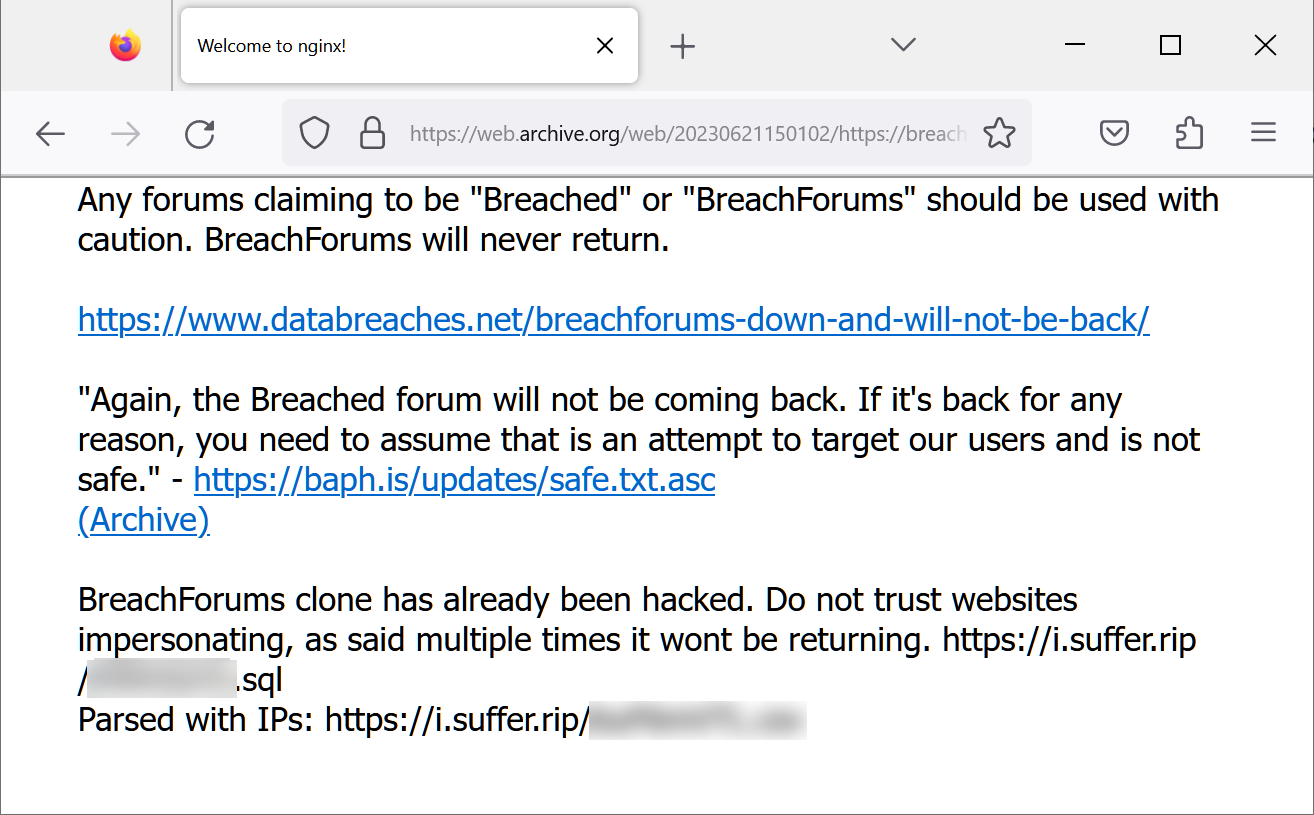
Even stranger, messages emerged on the old domains warning users that BreachedForums would never return and emphasizing that any forums claiming to be a new version of BreachedForum should be approached cautiously.
“Any forums claiming to be ‘Breached’ or ‘BreachForums’ should be used with caution. BreachForums will never return,” read a message posted on the Breached[.]vc domain.
This alert was later updated with alleged messages from Baphomet cautioning that any forums claiming to be the new BreachForums should be assumed unsafe. Baphomet denied it was them making these updates on the old domains.
In an escalating conflict between various hacking forums, Baphomet’s and Shiny Hunter’s new BreachForums was hit by its own data breach, with threat actors releasing the site’s stolen database.
Subsequently, an update appeared on the old Breached[.]vc domain, advising against trusting the BreachForums clone as it had already been hacked. This message also contained a link to an SQL file for the leaked stolen database from the new BreachedForums.
All of these new updates on the site included a hidden HTML comment stating ‘Meow,’ followed by a crying smiley face:
While some in the cybersecurity community felt that this was an attempt by law enforcement to discourage the return of further data breaches and hacking forums, this message also leaked the new BreachForums database, which is not something you would typically see from law enforcement.
The old forum’s domain began displaying the FBI’s seizure banner three days later.
Pompompurin’s arrest
During his arrest on March 15th, BreachForums’ owner openly admitted without a lawyer present and after waiving his constitutional rights that his real name was Connor Brian Fitzpatrick and that he was indeed Pompourin, according to a statement by FBI Special Agent John Longmire included in court documents.
He was charged with involvement in the theft and sale of sensitive personal information belonging to “millions of U.S. citizens and hundreds of U.S. and foreign companies, organizations, and government agencies.”
Fitzpatrick was released one day later on a $300,000 bond and was scheduled to appear in the District Court of the Eastern District of Virginia on March 24th.
On the day of his arraignment, the FBI confirmed in new court documents that they had access to BreachForums’ database.
After the owner’s arrest, Baphomet shut Breached down after saying they believed law enforcement had access to the forum’s servers.
Who is Pompompurin?
Pompompurin has been a high-profile member of RaidForums and part of a cybercriminal underground focused on hacking companies’ networks and selling or leaking stolen data online.
Following the seizure of RaidForums in 2022, Pompompurin created the BreachForums (or Breached) forum, which quickly became the largest platform for data leaks, frequently used by ransomware groups and other threat actors to leak stolen information.
Notably, before Fitzpatrick’s arrest, an unidentified individual attempted to sell personal data belonging to U.S. politicians. This data was obtained during the breach of D.C. Health Link, the healthcare provider for U.S. House members, their families, and staff.
Pompompurin was also involved in the breach of other high-profile organizations and companies. For instance, he exploited a vulnerability in the FBI’s Law Enforcement Enterprise Portal (LEEP) to send fake cyberattack alert emails.
He also stole customer data from Robinhood and purportedly exploited a Twitter bug to find the email addresses of approximately 5.4 million users.
It should also be noted that court documents released following Fitzpatrick’s arrest are yet to disclose any charges against Pompompurin linked to breaches and malicious activity beyond BreachForums.




