The Federal Bureau of Investigation and the Cybersecurity and Infrastructure Security Agency released an advisory about the evasive threat actor tracked as Scattered Spider, a loosely knit hacking collective that now collaborates with the ALPHV/BlackCat Russian ransomware operation.
Scattered Spider, also known as 0ktapus, Starfraud, UNC3944, Scatter Swine, Octo Tempest, and Muddled Libra, is adept at social engineering and relies on phishing, multi-factory authentication push bombing (targeted MFA fatigue), and SIM swapping to gain initial network access on large organizations.
The group includes young English-speaking members (as young as 16) with diverse skill sets who frequent the same hacker forums and Telegram channels.
Some of the members are believed to also be part of the “Comm” – a loose-knit community involved in violent acts and cyber incidents that has been gaining wide media attention lately.
Contrary to the general belief that it is a cohesive gang, they are a network of individuals, with different threat actors participating in each attack. This fluid structure is what makes it difficult to track them.
However, according to Reuters journalists, the FBI knows the identities of at least 12 members of the group but none have been indicted or arrested yet.
Background
Scattered Spider attacks were documented since last summer when researchers at cybersecurity company Group-IB publishing a report about a spree of attacks aiming to steal Okta identity credentials and 2FA codes, which had started March the same year.
In December 2022, CrowdStrike profiled the threat actor as a financially motivated group targeting telcos, employing high-level social engineering tactics, defense reversal, and a rich set of software tools.
In January 2023, Crowdstrike discovered that Scattered Spider was using BYOVD (Bring Your Own Vulnerable Driver) methods to evade detection from EDR (endpoint detection and response) security products.
More recently, in September this year, to two high-profile attacks against MGM Casino and Caesars Entertainment, were attributed to Scattered Spider, where the threat actors used the BlackCat/ALPHV locker to encrypt systems.
Past activity from the threat actor includes attacks on MailChimp, Twilio, DoorDash, and Riot Games.
An October report by Microsoft, who calls them Octo Tempest, says that they are one of the most dangerous financial criminal groups, and have been known to resort to violent threats to achieve their goals.
source: Microsoft
The researchers’ findings about the group’s variety of attack methods indicate that its members have knowledge that extends to different areas of cybercrime, from social engineering and hacking, to SIM swapping, phishing, and bypassing login protections.
Scattered Spider tactics
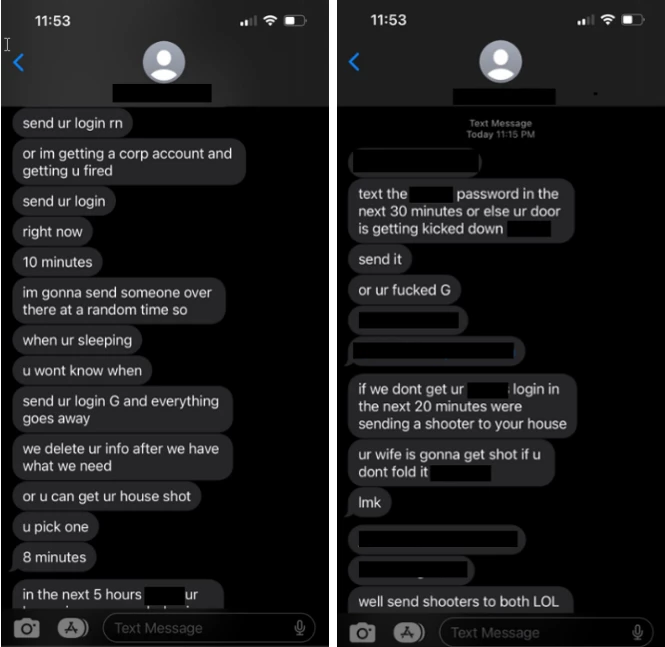
The FBI and CISA alert highlights Scattered Spider’s powerful initial access tactics that involve targeting a company’s employees by posing as IT or help-desk staff and tricking them into providing credentials or even direct network access.
Individual tactics include phone calls, SMS phishing, email phishing, MFA fatigue attacks, and SIM swapping. The domains used for email and SMS phishing abuse the Okta and Zoho ServiceDesk brands combined with the target’s name to make them appear legitimate.
After establishing a foothold on the network, Scattered Spider uses a range of publicly available software tools for reconnaissance and lateral movement, including:
- Fleetdeck.io: Remote system monitoring and management
- Level.io: Remote system monitoring and management
- Mimikatz: Credential extraction
- Ngrok: Remote web server access via internet tunneling
- Pulseway: Remote system monitoring and management
- Screenconnect: Network device remote connection management
- Splashtop: Network device remote connection management
- Tactical.RMM: Remote system monitoring and management
- Tailscale: VPN for secure network communications
- Teamviewer: Network device remote connection management
Apart from the above legitimate tools used for malicious purposes, Scattered Spider also conducts phishing attacks to install malware like the WarZone RAT, Raccoon Stealer, and Vidar Stealer, to steal from compromised systems login credentials, cookies, and other data useful in the attack.
A new tactic observed in the threat group’s recent attacks is data exfiltration and file encryption using the ALPHV/BlackCat ransomware, followed by communication with the victims via a messaging app, email, or other secure tools to negotiate a ransom payment.
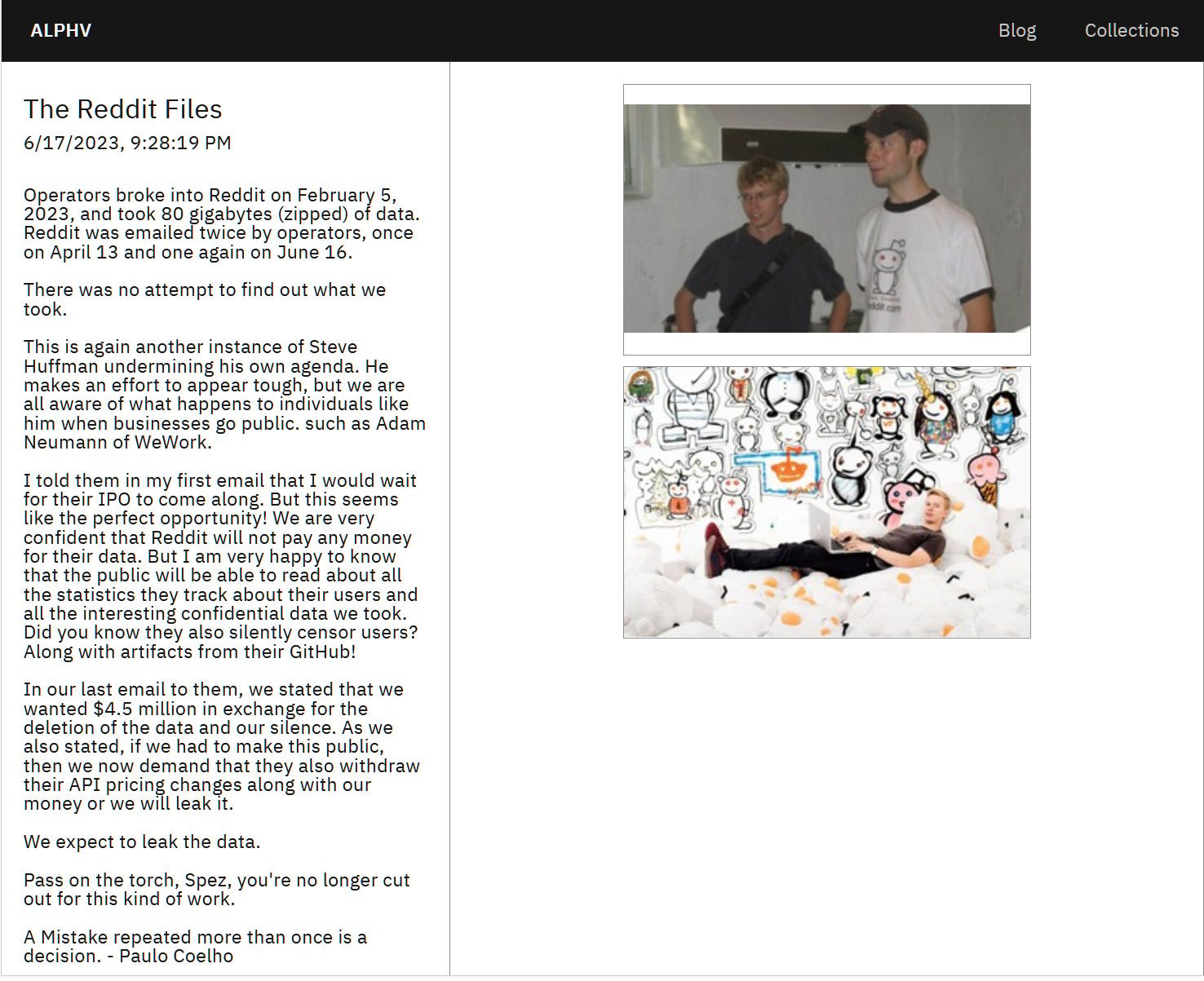
The Scattered Spider actors affiliated with BlackCat are also known to use the ransomware gang’s data leak site as part of their extortion attempts, where they leak data or issue statements about the attack, as it happened with their attack on Reddit.
source: BleepingComputer
Scattered Spider shows particular interest in valuable assets like source code repositories, code-signing certificates, and credential storage.
Also, the attackers closely monitor the victim’s Slack channels, Microsoft Teams, and Microsoft Exchange emails for messages containing any indication that their activities have been discovered.
“The threat actors frequently join incident remediation and response calls and teleconferences, likely to identify how security teams are hunting them and proactively develop new avenues of intrusion in response to victim defenses” – Federal Bureau of Investigation
The agency adds that the cybercriminals achieve this “by creating new identities in the environment” that often have fake social media profiles for a false sense of legitimacy.
Proposed mitigations
The FBI and CISA recommend implementing specific mitigations to protect against threats imposed by Scattered Spider.
Key recommendations in the advisory propose to:
- Use application controls with “allowlisting” to manage software execution.
- Monitor remote access tools and implement phishing-resistant multifactor authentication (MFA).
- Secure and limit Remote Desktop Protocol (RDP) usage with best practices and MFA.
- Maintain offline backups and adhere to a robust data recovery plan.
- Follow NIST standards for strong, less frequently changed passwords.
- Keep systems and software regularly updated, focusing on patching vulnerabilities.
- Implement network segmentation to control traffic and prevent ransomware spread.
- Use network monitoring and Endpoint Detection and Response (EDR) tools to detect abnormal activities.
- Enhance email security by disabling risky links and encrypting backup data.
Finally, organizations are advised to test and validate their security controls against MITRE ATT&CK techniques described in the advisory.
