PromptSpy is a newly discovered Android malware family that abuses Google’s Gemini generative AI model to make real‑time decisions on how to manipulate the user interface and stay active on infected devices.
PromptSpy’s AI‑assisted functionality is focused on persistence rather than initial infection or data theft.
Instead of relying on hardcoded tap coordinates or fragile UI selectors, the malware sends Gemini a natural‑language prompt plus an XML snapshot of the current screen, including each element’s text, type, and bounds.
Gemini analyzes this context and returns JSON instructions describing what gesture to perform (tap, long‑press, swipe) and where on the screen to execute it, allowing PromptSpy to “lock” its malicious app in the Recent Apps list even when the user tries to close it.
ESET describes it as the first known Android threat to integrate generative AI directly into its execution flow, with the main goal of enabling stealthy persistence and full remote control of compromised phones.
A code snippet of PromptSpy’s initialization of communication with Gemini, including the first prompt used.
The malware maintains a loop: it executes Gemini’s instructions via Accessibility Service, captures the updated UI, and keeps prompting until Gemini confirms that the app is successfully pinned, making the technique robust across devices, OEM skins, and OS versions.
Android AI Malware
Beyond its AI‑driven persistence, PromptSpy behaves like a powerful remote‑access tool centered around a built‑in VNC component.
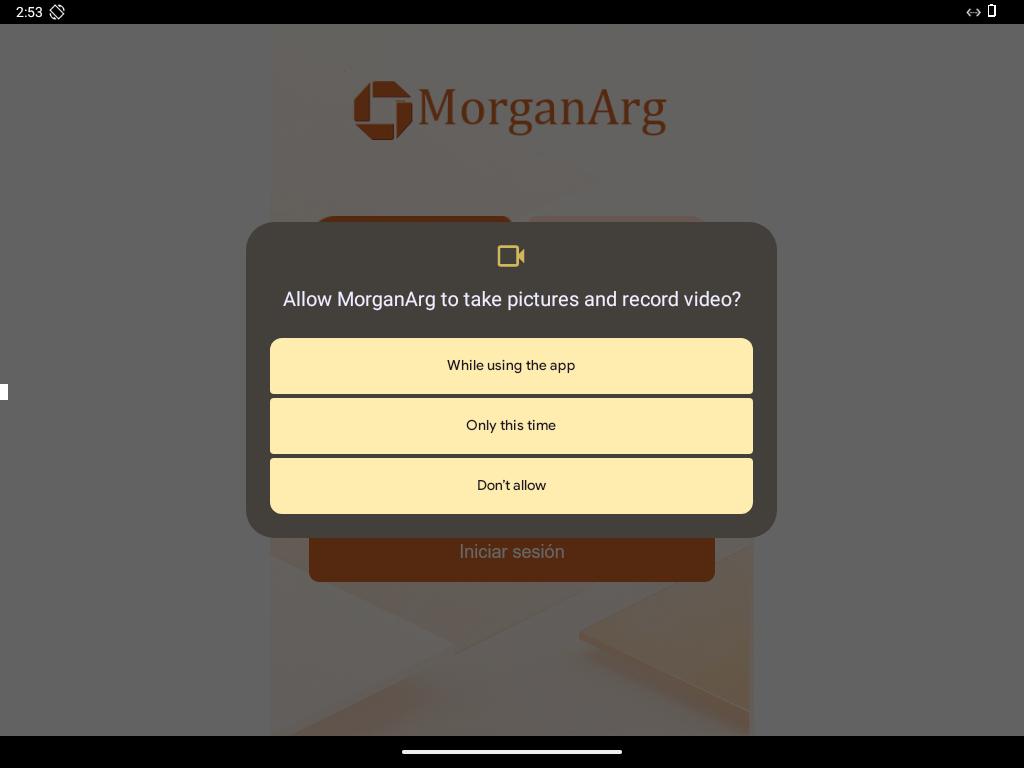
VirusTotal showed the spoofed website in Spanish, with an Iniciar sesión (Login) button, indicating that the page was probably intended to mimic a website of a bank.
Once the victim grants Accessibility permissions, operators can view the device screen in real time, simulate taps and gestures, and perform arbitrary actions as if they were physically using the phone.
The malware can capture lockscreen credentials, collect device information, take screenshots, record screen activity as video, and report foreground app state back to its operators.
Communication with a hardcoded command‑and‑control server over the VNC protocol is protected using AES encryption, and the C2 can also deliver a Gemini API key campaign and tasking instructions to the malware.
PromptSpy aggressively resists removal by abusing Accessibility to draw invisible overlays over critical buttons, including those related to uninstalling the app or turning off its privileges.
Our technical analysis focuses on the PromptSpy dropper and its payload, PromptSpy. PromptSpy is embedded (app-release.apk) inside the dropper’s asset directory.
These transparent rectangles intercept user taps on “Uninstall” or “Stop” actions, effectively blocking normal cleanup; ESET notes that rebooting into Safe Mode and removing the app from system settings is the reliable remediation path.
ESET’s investigation links PromptSpy to a multistage campaign that appears financially motivated and aimed primarily at users in Argentina.
Samples related to an earlier variant dubbed VNCSpy were first uploaded to VirusTotal from Hong Kong in January 2026, while more advanced PromptSpy builds arrived from Argentina in February 2026.
The droppers were distributed via domains such as mgardownload[.]com and m‑mgarg[.]com, which mimicked JPMorgan Chase–style branding under the name “MorganArg”, suggesting a banking fraud theme with Spanish‑language lures.
Pivoting on this infrastructure revealed another Android phishing trojan signed with the same certificate and using the same fake banking site, likely serving as an initial stage that pushes victims toward installing PromptSpy.
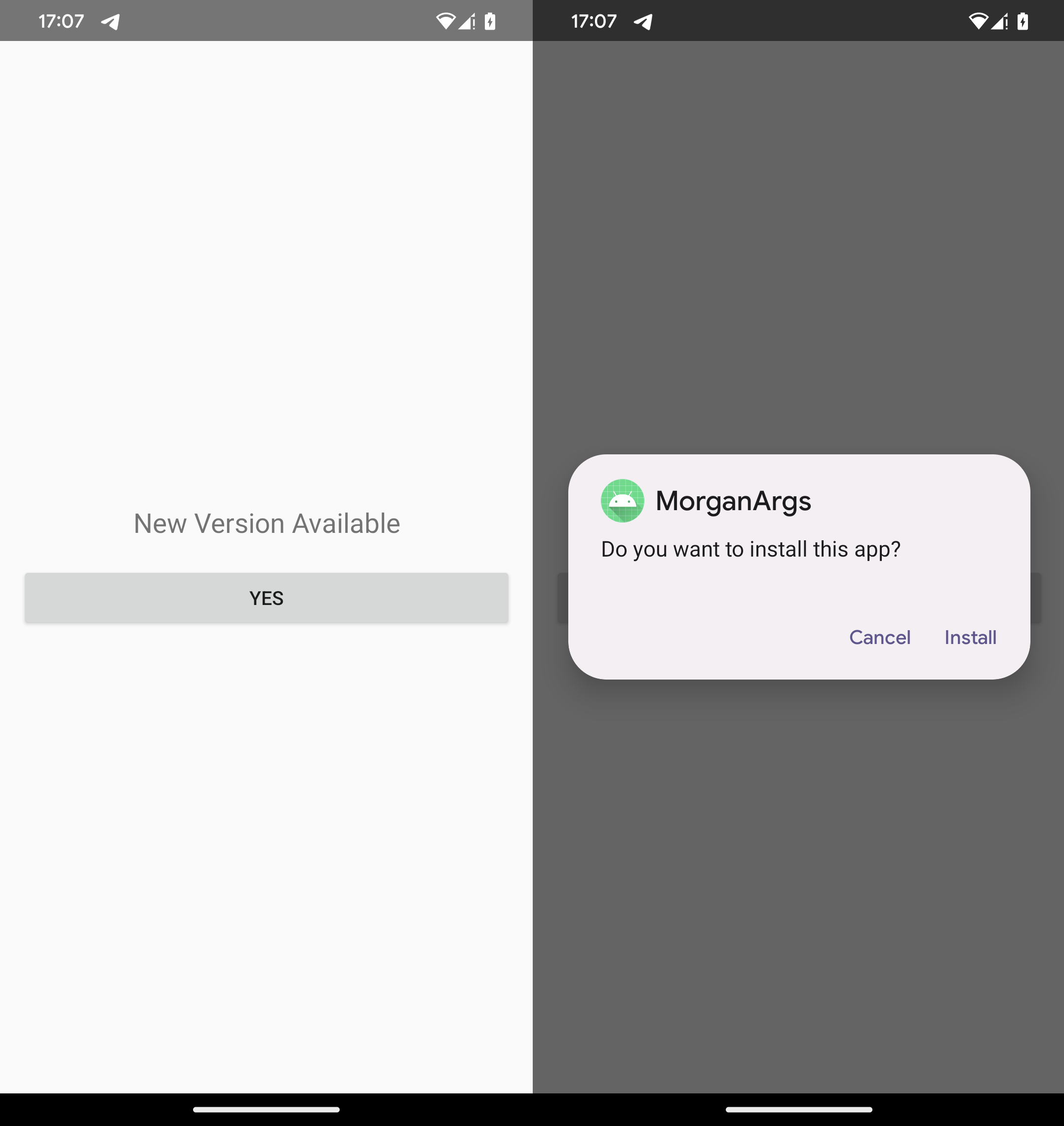
Although the malware has not yet appeared in ESET’s telemetry and may still be at a proof‑of‑concept stage, the identified distribution domains indicate that at least limited in‑the‑wild testing has taken place.
Code‑level clues, including simplified Chinese debug strings and handling of Chinese Accessibility events, suggest development in a Chinese‑speaking environment, even though the active targeting currently centers on Latin American users.
PromptSpy is not available on Google Play, but Google Play Protect now detects known variants, providing automatic protection for devices with Play Services enabled.finance.
PromptSpy follows ESET’s earlier discovery of PromptLock, an AI‑powered ransomware prototype from 2025 that used a local language model to generate malicious scripts, underlining a growing trend of threat actors weaving generative AI into real‑world malware operations.
IOCs
| SHA-1 | Filename | Detection | Description |
|---|---|---|---|
| 6BBC9AB132BA066F63676E05DA13D108598BC29B | net.ustexas.myavlive.apk | Android/Spy.VNCSpy.A | Android VNCSpy malware. |
| 375D7423E63C8F5F2CC814E8CFE697BA25168AFA | nlll4.un7o6.q38l5.apk | Android/Spy.VNCSpy.A | Android VNCSpy malware. |
| 3978AC5CD14E357320E127D6C87F10CB70A1DCC2 | ppyzz.dpk0p.ln441.apk | Android/Spy.VNCSpy.A | Android VNCSpy malware. |
| E60D12017D2DA579DF87368F5596A0244621AE86 | mgappc-1.apk | Android/Spy.PromptSpy.A | Android PromptSpy dropper. |
| 9B1723284E311794987997CB7E8814EB6014713F | mgappm-1.apk | Android/Spy.PromptSpy.A | Android PromptSpy dropper. |
| 076801BD9C6EB78FC0331A4C7A22C73199CC3824 | mgappn-0.apk | Android/Spy.PromptSpy.A | Android PromptSpy dropper. |
| 8364730E9BB2CF3A4B016DE1B34F38341C0EE2FA | mgappn-1.apk | Android/Spy.PromptSpy.A | Android PromptSpy dropper. |
| F8F4C5BC498BCCE907DC975DD88BE8D594629909 | app-release.apk | Android/Spy.PromptSpy.A | Android PromptSpy. |
| C14E9B062ED28115EDE096788F62B47A6ED841AC | mgapp.apk | Android/Phishing.Agent.M | Android phishing malware. |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.