In the past year alone, we have reported almost five hundred unique malvertising incidents related to Google search ads. While it can be difficult to attribute each incident to a specific threat actor, we usually notice similarities between campaigns.
Some malvertisers go to great lengths to bypass security controls, while others know they will get caught and are willing to burn their accounts and infrastructure. Having said that, we have generally observed stealthier attacks and the one we are covering in this blog is one of them.
Targeting the popular communication tool Slack, a threat actor is relying on several online tools to narrow down their victims’ list and most importantly evade detection.
Context is everything
For several days we noticed a suspicious ad for Slack that appeared when you googled the search term for it. The ad actually looks quite legitimate and is listed above the organic search result for the official site. Despite its appearance, we knew it was likely malicious, even though clicking on it at the time would only result in being redirected to slack.com.
Almost every Google ad contains additional information about its advertiser and why it was displayed to you. This is accessible by clicking on the 3 dots beside the ad URL and it brings you to the Google Ads Transparency Center. What we notice is that this advertiser is promoting products that look targeted at the Asian market, and then there’s this Slack ad that appears in the middle of nowhere.

We’ve mentioned before how contextualized detection could be a good way to identify an advertiser account that has been compromised. We don’t know whether Google’s algorithms are trained on this or not, but it has certainly helped us many times in the past to find new malicious ad campaigns.
Slow cooking
For days, clicking on this Slack ad would only redirect to a price page on Slack’s official website. Ads aren’t always weaponized right away; in fact it is a common practice for threat actors to let their ad ‘cook’ such that it does not immediately become detected.

Eventually, we saw a change in behavior. Rather than redirecting to slack.com, now the ad first started redirecting to a click tracker. This is one of the weaknesses in the Google ad ecosystem as such services can be abused to filter clicks and essentially send traffic to a domain of anyone’s choosing. Tracking templates as they are known, are a built-in feature that has become synonym with fraud for us.
Playing games of hide and seek
Now the ad’s final URL had become slack-windows-download[.]com an interesting choice for a domain name created less than a week ago. While it is obvious that this page was automatically generated, perhaps using AI, there is nothing malicious on it. For whatever reason, the server side checks determined that we should only be seeing this decoy page at the time:
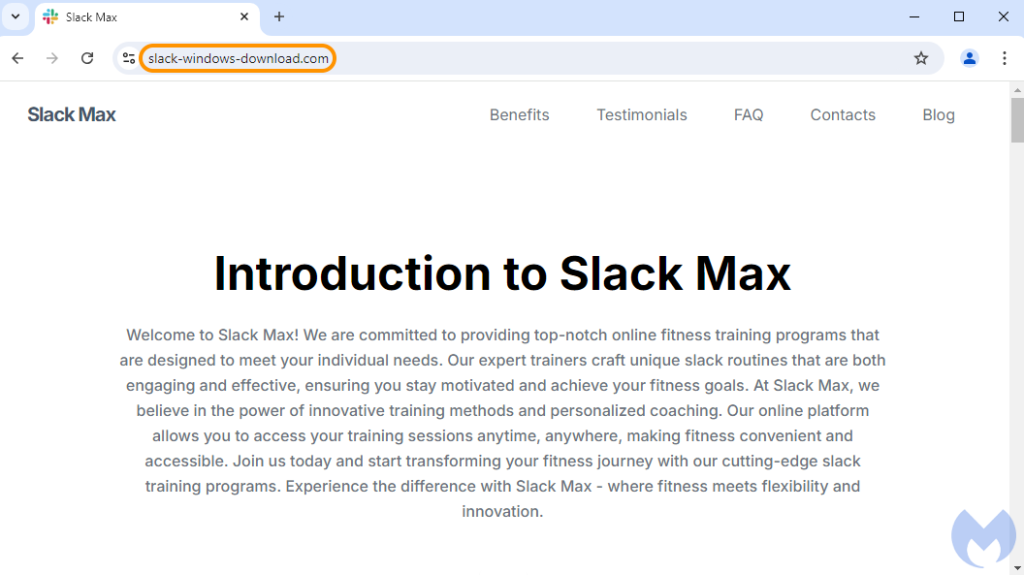
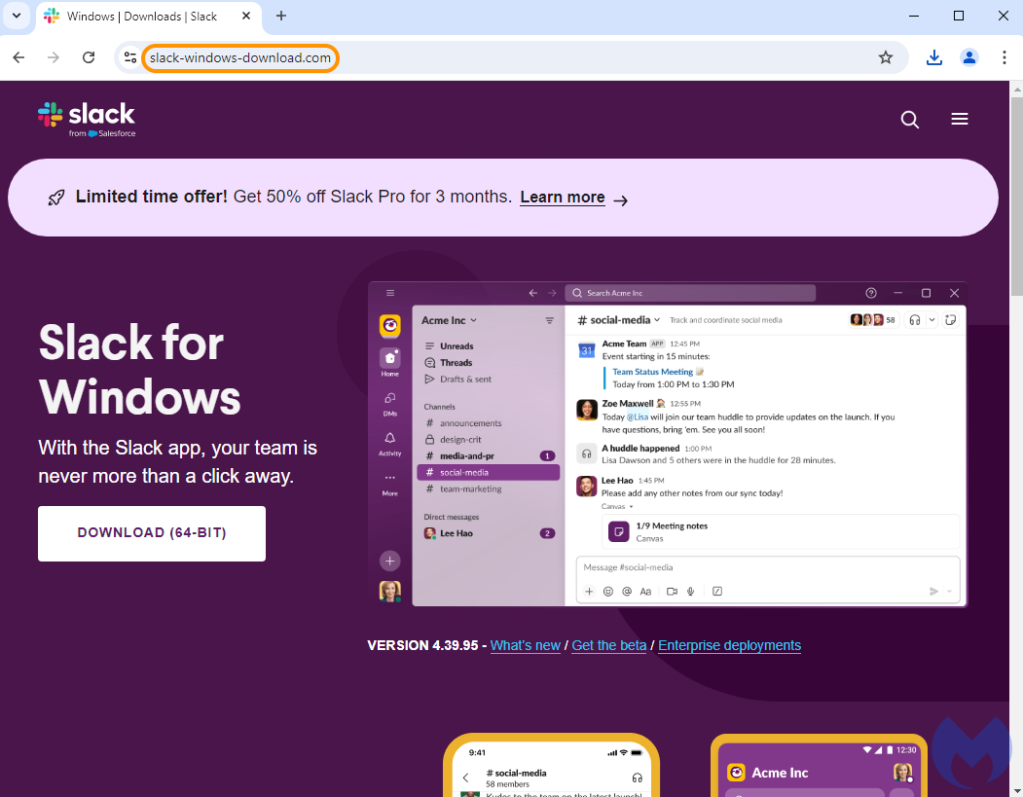
After tweaking various settings, we finally saw the malicious page, meant to impersonate Slack and offer a download link to unsuspecting victims. It is the same domain as the one above, but the content is completely different. That type of behavior is known as cloaking, where different users are shown different content:
Below is a network traffic capture showing what was required to get to this page. There are a few things worth noting:
- The Google ad URL redirects to a click tracker, followed by another. There is no way for Google to know where users are going at this point.
- The click trackers themselves are blinded on what happens next, thanks to a link shortener followed by one more cloaking domain.
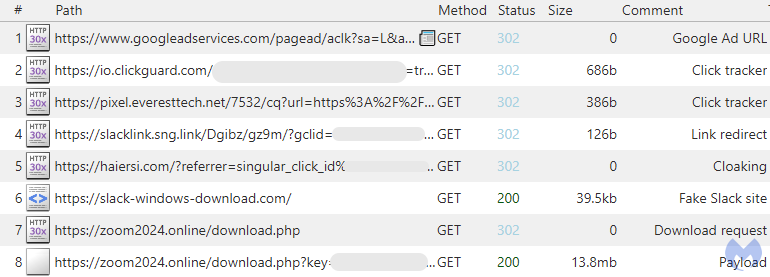
This deep layering makes it incredibly difficult to evaluate an ad without resorting to specific tooling and knowledge of the threat actors’ TTPs.
Malware payload
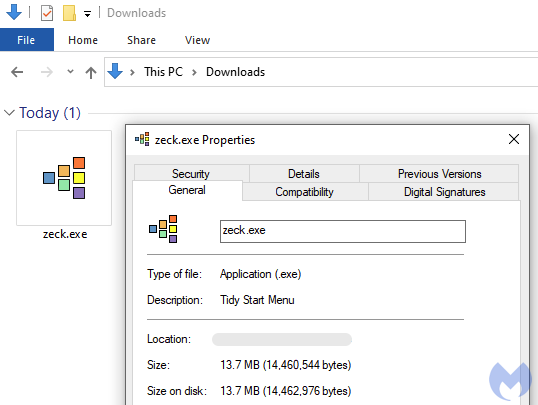
The download button triggers a file download from another domain that may hint at a parallel campaign targeting Zoom. A key is passed to the server to request the malware binary to users who went through the delivery chain.
Dynamic analysis in a sandbox shows a remote connection to 45.141.87[.]218, a server previously used by SecTopRAT, a remote access Trojan with stealer capabilities. This payload was previously dropped in other malvertising chains, one of them impersonating NordVPN.
Conclusion
Malwarebytes was already blocking that command and control server and we’ve improved our detection coverage by adding the supporting and delivery infrastructure used in this campaign. In addition, we’ve reported the malicious ad to Google and Cloudflare has now flagged the decoy domains that were abusing its services, as phishing.
We expect malvertisers to continue to exploit free and paid platforms to help them avoid detection, but we also should be aware that they may be more patient and wait for the right moment to unleash a new campaign.
Indicators of Compromise
Link redirect
slacklink[.]sng[.]link
Cloaking
haiersi[.]com
Decoy sites
slack-windows-download[.]com
slack-download-for-windows[.]com
Payload download
zoom2024[.]online
Payload SHA256
59e5e07ffa53ad721bc6b4c2ef435e08ae5b1286cda51415303978da474032d2
