A sophisticated malware campaign dubbed “GhostPoster” has compromised approximately 50,000 Firefox users by exploiting browser extension icons.
Security researchers at Koi Security discovered that malicious actors are embedding hidden malware payloads directly within PNG logo files, turning seemingly innocent visual elements into dangerous delivery mechanisms that evade traditional security scanning.
The campaign spans 17 Firefox extensions with combined installations exceeding 50,000 users.
Among the malicious extensions, “Free VPN Forever” has been active on the Firefox Add-ons marketplace since September 2025, accumulating over 16,000 installations.
The extension remains live at the time of reporting, alongside numerous other compromised add-ons masquerading as VPN services, translation tools, weather forecasts, and ad blockers.
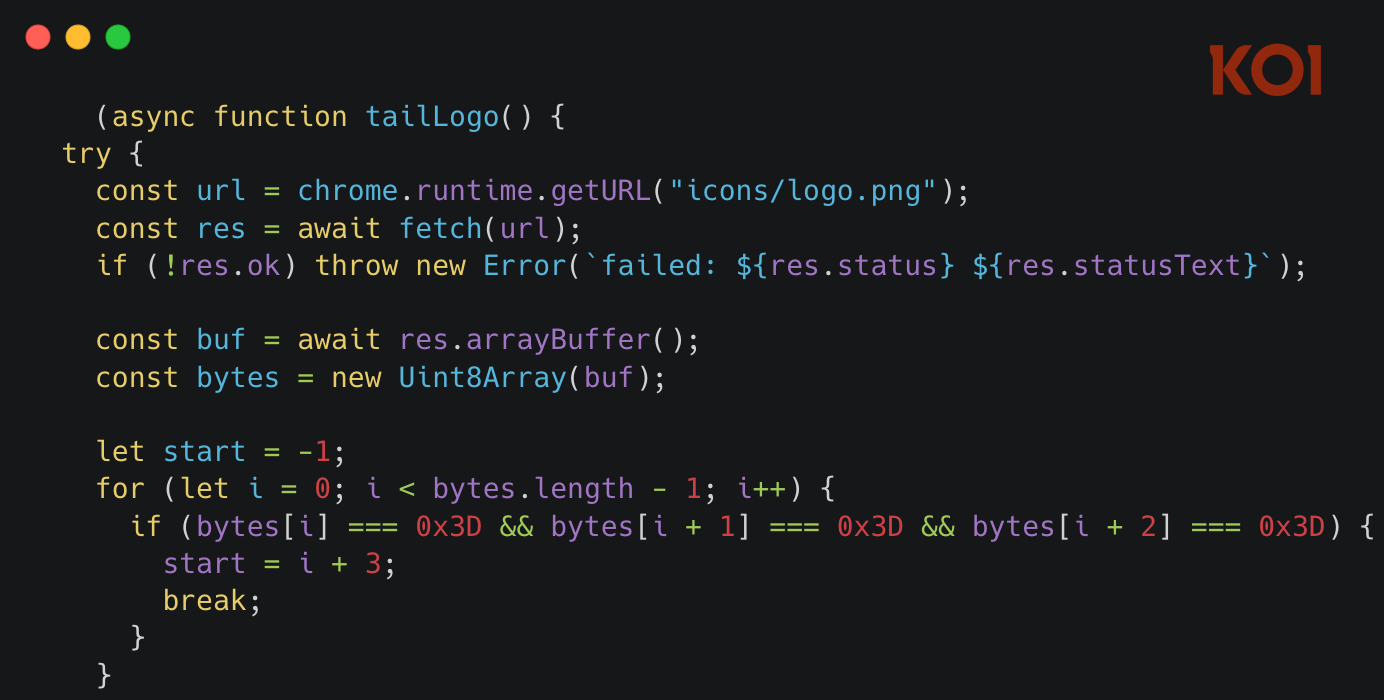
The attack employs steganography, a technique that conceals executable code within image files without affecting their visual appearance.
When extensions like Free VPN Forever load, they retrieve their own logo.png file, a standard operation that raises no security flags.
However, the extension then searches the image’s raw bytes for a specific marker consisting of three equals signs (===). Everything following this marker is not image data but hidden JavaScript code waiting to be extracted and executed.library
This multi-stage malware architecture begins with the logo serving as the initial loader. The extracted code contacts command-and-control servers at liveupdt[.]com or its backup dealctr[.]com to retrieve the actual payload.
The malware demonstrates sophisticated evasion tactics by waiting 48 hours between server check-ins and only fetching the payload 10% of the time.
This random behavior pattern makes it extremely difficult for security researchers monitoring network traffic to observe suspicious activity, as infected extensions may operate silently for extended periods.library
When the payload arrives from the C&C server, it undergoes custom encoding that swaps uppercase and lowercase letters, exchanges 8s and 9s, then applies Base64 decoding.
The decoded payload is XOR encrypted using the extension’s unique runtime ID before being stored in browser storage, establishing persistence on the victim’s system.library
Comprehensive Browser Hijacking
The final payload delivers a multi-faceted attack that monetizes infected browsers without user knowledge.
The malware intercepts affiliate links on major e-commerce platforms like Taobao and JD.com, redirecting commissions from legitimate affiliates to the attackers.
It injects Google Analytics tracking (ID: UA-60144933-8) into every visited page, collecting installation dates, infection duration, visited merchant networks, and unique browser identifiers.library+1
Perhaps most concerning, the malware actively strips critical security headers from HTTP responses, removing Content-Security-Policy and X-Frame-Options protections that defend against clickjacking and cross-site scripting attacks.
The extension includes multiple CAPTCHA bypass methods, using invisible overlays to simulate user interaction and external solvers hosted at refeuficn.github.io.
Hidden iframes are injected into pages for ad fraud and click fraud operations, disappearing after 15 seconds to avoid forensic detection.
Malicious VPN Extensions
GhostPoster represents the latest in a troubling trend of free VPN extensions turning malicious.
.png)
Earlier this month, Urban VPN Proxy, a Google-featured extension with 8 million users, was exposed for harvesting AI conversations from ChatGPT, Claude, and Gemini to sell to data brokers.
Similarly, FreeVPN.One, another verified extension with over 100,000 installations, was caught silently capturing screenshots of users’ banking information, private photos, and sensitive documents.
The GhostPoster campaign demonstrates how attackers are refining their techniques through experimentation.
The 17 identified extensions use varying delivery mechanisms, some employing PNG steganography while others download JavaScript directly or use hidden eval() calls with encoded C&C domains.
This suggests threat actors are testing which approaches evade detection longest and generate maximum revenue.
Users should immediately review their Firefox extensions and remove any unfamiliar or recently installed VPN and utility extensions to protect against this ongoing threat.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
