The precautions and techniques that have been put in place for the protection of email messages from unauthorized access, interception or manipulation is regarded as email security.
This includes the protection of confidential information, integrity, and availability of email communications while at the same time complying with cyber security threats like spam, phishing attacks, malware, or data breaches.
.png
)
Encryption, authentication, spam filtering, phishing protection, malware detection, data loss prevention, and user awareness are a whole range of disciplines that cover the subject of email security.
Individuals and organizations can benefit from the protection of confidentiality, integrity, or accessibility of their email messages, as well as mitigating risks to information exchange if they apply a comprehensive set of e.g. mail security measures.
Email security is of paramount importance due to the following reasons:
- Confidentiality: Without adequate email security measures in place, unauthorized people or organizations can intercept and access this data, resulting in privacy violations, identity theft, or business espionage.
- Data Protection and Compliance: Adequate email security measures help ensure compliance with legal regulations, such as the Health Insurance Portability and Accountability Act (HIPAA) in the healthcare industry.
- Intellectual Property Protection: In order to protect the competitive advantage and innovation of an enterprise, proper email security safeguards the company’s important intellectual property assets such as blueprints, patents, etc. against unauthorized access or theft.
- Business Continuity: A breach in email security can disrupt normal operations, leading to financial losses, reputational damage, and loss of customer trust.
- Phishing and Malware Defense: Effective email security solutions can recognize and filter phishing emails, shielding staff members and people from con artists and unintentional system compromise.
- Spam Management: Implementing spam filtering techniques helps clear up email inbox congestion, enabling users to concentrate on important correspondence and lowering the chance of coming into contact with hazardous information.
- Reputation Protection: The danger of becoming involved in harmful actions is decreased by using robust email security measures, such as authentication procedures and encryption, protecting reputation and trustworthiness.
Worrying About Sophisticated Email Threats? – Deploy Email Managed Detection & Response in Your IT Environment.
Evolving Email Threat Landscape: Challenges and Risks
Organizations and individuals must handle a number of risks and challenges posed by the changing email threat landscape in order to maintain effective email security.
Use a strong email security solution to address the issues and lower the risks in order to do this. The complete email security platform Trustifi provides a number of options to improve your email security.
The main challenges and risks that constitute email threats are listed below:
Sophisticated Phishing Attacks: Cybercriminals employ advanced social engineering techniques, creating highly convincing phishing emails that mimic legitimate organizations or individuals.
By detecting phishing attempts and malicious content, email security solutions like Trustifi help users avoid falling victim to scams.
Business Email Compromise (BEC): Business email compromise, commonly referred to as CEO fraud or whaling, attacks businesses by impersonating senior executives or reliable partners.
BEC assaults employ a strategy called social engineering in order to take advantage of the authority and trust inside the company.
Malware and Ransomware: Email is the most frequent method of propagating malware or ransomware to an unknown user.
Organizations can rely on solutions like Trustifi to detect and prevent these types of Phishing as well as Malware threats, with the help of modern technologies.
Insider Threats: Insider threats involve individuals within an organization misusing their authorized access to compromise email security.
This can include intentionally leaking sensitive information, conducting unauthorized activities, or engaging in fraudulent activities using their email accounts.
Mobile Device Vulnerabilities: Mobile devices may lack security measures, making them more susceptible to attacks. Lost or stolen devices can lead to unauthorized access to email accounts and potential data breaches.
Compliance and Regulatory Challenges: To protect sensitive data, businesses must comply with several rules and laws, such as the General Data Protection Regulation (GDPR) and industry-related regulations.
Organizations should adopt efficient incident response plans, regularly monitor email traffic for anomalies, and stay updated on emerging threats to stay ahead of the evolving email threat landscape with AI-powered solutions like Trustifi.
What AI Powered in Email Security
AI-powered technology plays a significant role in improving standard email security by taking advantage of advanced algorithms and machine learning techniques.
AI algorithms can analyze large amounts of data and identify patterns, anomalies, indicators of malicious activity, etc.
This enables AI-powered systems to proactively block and prevent such threats from reaching users’ inboxes. for example, utilizes AI algorithms to provide robust threat intelligence and proactive detection, ensuring potentially harmful emails are identified and intercepted.
70% of global employees have noticed a surge in the frequency of scam emails and texts in the last few months.
AI-powered technology can also analyze user behavior, email content, and communication patterns to establish a baseline of normal activity.
By continuously monitoring and learning from these patterns, the algorithms can identify anomalies that may indicate suspicious or malicious behavior.
For example, if an email account suddenly starts sending an unusually high volume of emails or exhibits unusual patterns of activity, AI can flag it as a potential compromise.
Trustifi employs AI algorithms to detect unauthorized access, compromised accounts, or unusual email activity, alerting users to security risks.
AI-powered Natural Language Processing algorithms can analyze the content of emails to identify potentially malicious or suspicious elements.
These algorithms can understand and interpret the context and intent of email communications, enabling them to detect hidden phishing URLs, deceptive language, or malicious attachments.
As the algorithms analyze large volumes of email data, it allows them to evolve their threat detection capabilities and stay ahead of evolving email security challenges.
AI-powered capabilities help mitigate the risks associated with email-based attacks, protect sensitive information, and ensure a safer email communication environment.
The Role of Email Security Providers With AI
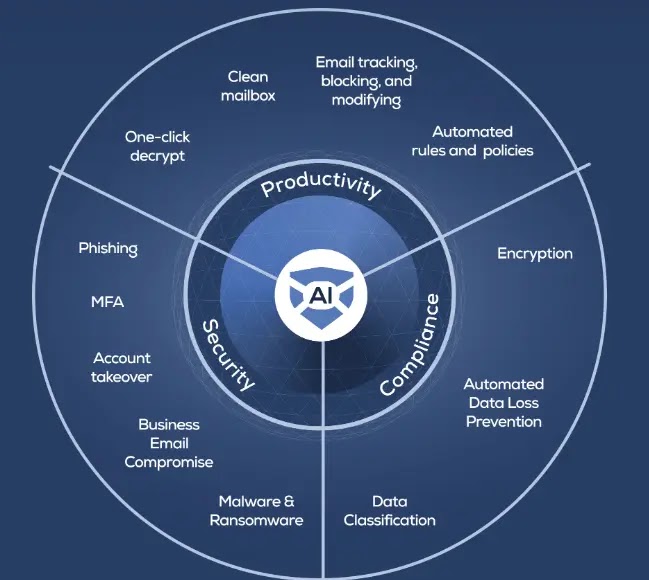
Email security providers (ESPs) play a crucial role in ensuring email security for organizations and individuals. ESPs offer a range of solutions and features to protect against email-based threats and create a secure communication environment.
Trustifi, as an example of an ESP, exemplifies the role of ESPs in email security.
With the increasing sophistication of phishing attacks and malware threats, ESPs employ advanced technologies to detect and prevent these risks.
It includes real-time scanning and analysis of email content, attachments, and links to identify and block suspicious emails.
ESPs like Trustifi provide email tracking that enables senders to receive notifications when their emails are opened or read, enhancing transparency and accountability.
They also incorporate effective data loss prevention (DLP) measures. It scans email content for predefined patterns or sensitive data types, such as credit card numbers or social security numbers, and applies appropriate security controls, such as encryption or access restrictions, to prevent data breaches.
ESPs employ advanced algorithms and technologies to analyze email content, sender reputation, and other factors to identify and block spam emails.
By implementing powerful spam filters, ESPs like Trustifi can prevent unwanted and potentially malicious emails from reaching users’ inboxes, reducing the risk of falling victim to scams or malware.
ESPs often provide encryption mechanisms, such as Transport Layer Security (TLS) and Secure/Multipurpose Internet Mail Extensions (S/MIME), to encrypt email messages and attachments.
Trustifi, for example, offers end-to-end email encryption, providing an additional layer of security for sensitive communications.
Furthermore, ESPs deploy secure email gateways to intercept and analyze incoming and outgoing email traffic. These gateways act as a barrier between the email server and external networks, scanning email content for threats and vulnerabilities.
By implementing secure email gateways, ESPs like Trustifi can detect and block malicious emails, preventing them from reaching the intended recipients and reducing the risk of email-based attacks.
Key Challenges in Email Security: Addressing Vulnerabilities
Email security faces various key challenges that need to be addressed to ensure the protection of sensitive information and mitigate the risks associated with cyber threats.
Trustifi, as an email security provider leveraging AI-powered technology, offers many solutions to tackle these challenges.
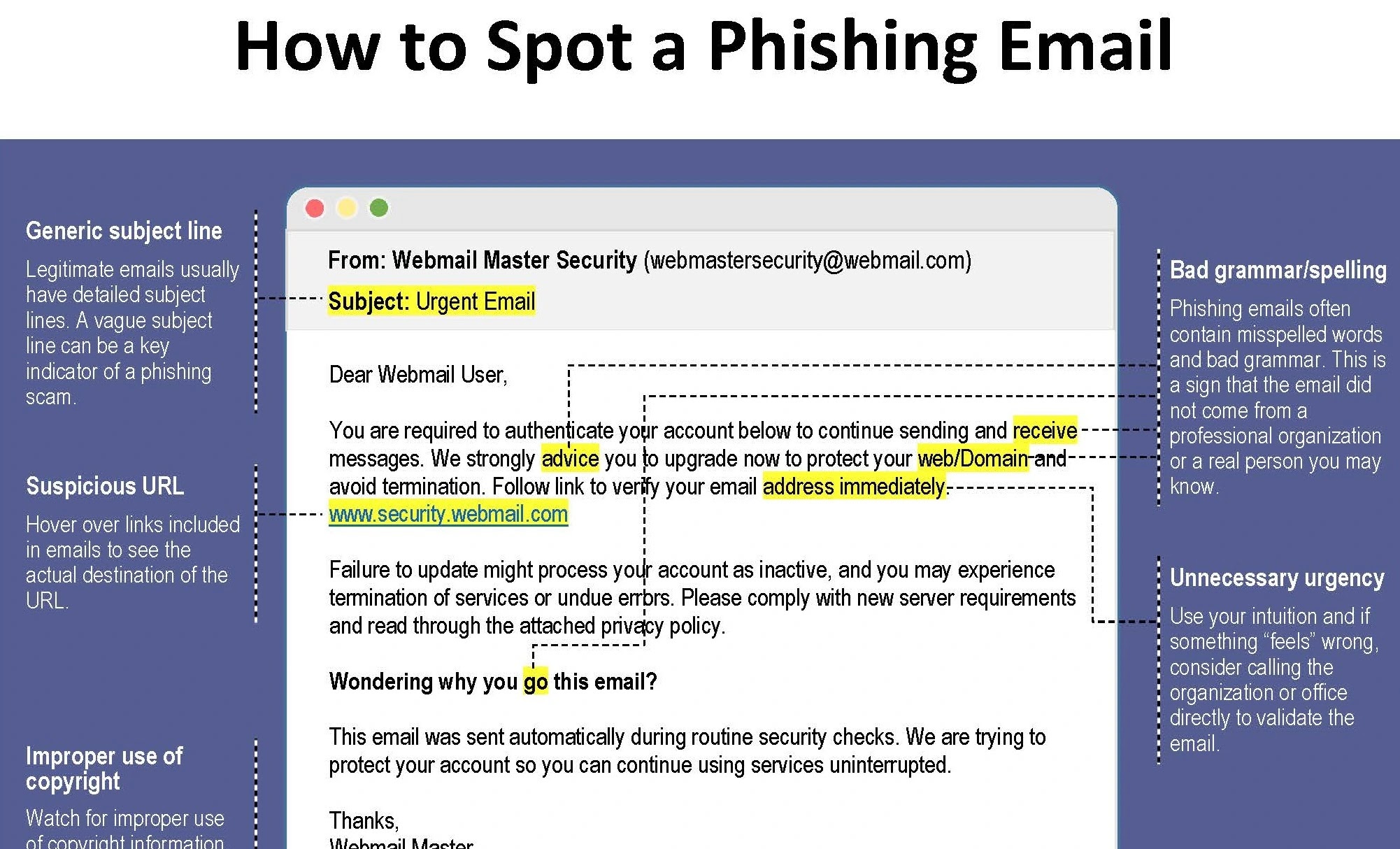
Phishing remains a prevalent challenge, with cybercriminals attempting to trick users into divulging sensitive information.
AI-powered solutions like Trustifi.com use advanced algorithms to analyze email content, URLs, and sender reputation to identify and block phishing attempts.
Emails are commonly used to deliver malware and ransomware, which can compromise systems and data.
AI-powered email security solutions can identify malicious attachments, links, and suspicious behavior indicative of malware or ransomware.
By employing machine learning techniques to detect anomalies in email communications, Trustifi.com helps prevent users from falling victim to phishing attacks.
Trustifi utilizes AI algorithms to detect and block such threats, ensuring that users’ systems and data remain protected from malware infections and ransomware attacks.
Preventing unauthorized access to sensitive information and addressing the risk of data leakage is crucial.
AI-powered email security solutions employ techniques like data loss prevention and user behavior analysis to identify and prevent the unauthorized transmission of data.
Trustifi.com’s AI algorithms monitor email activity, detect potential leaks, and provide real-time alerts to mitigate the risk of unauthorized access and leakage.
AI-powered solutions can monitor user behavior, identify unusual activity, and detect potential insider threats. Compliance with regulatory requirements and industry standards is essential for organizations.
AI-powered email security solutions can also assist in meeting compliance obligations by providing features such as email archiving, tamper-proof certified email delivery, and secure email storage.
AI algorithms enable the detection of phishing attempts, malware threats, data leakage, insider threats, and support compliance requirements.
With the continuous learning capabilities of AI, ESPs like Trustifi evolve their threat detection mechanisms to stay ahead of emerging email security risks and provide users with a robust defense against cyber threats.
Implementing AI-Powered Email security solutions “Trustifi” can secure your business from today’s most dangerous email threats, such as Email Tracking, Blocking, Modifying, Phishing, Account Take Over, Business Email Compromise, Malware & Ransomware
Future Trends in Email Security
Email security is an ever-evolving field, and as technology advances and new threats emerge, email security measures must also evolve.
To keep pace with hackers, organizations need AI-based threat detection and response technology to defend against known, emerging, and never-before-seen email-borne threats.
AI and machine learning technologies can help to identify patterns and anomalies in email traffic, which can be used to detect and prevent attacks such as phishing, malware, and spam.
As these technologies become more advanced, they will likely become more widely used in email security.
Email security is just one part of an organization’s overall security strategy. In the future, we may see greater integration between email security and other security systems, such as firewalls, intrusion detection systems, and security information and event management (SIEM) platforms, to provide a more comprehensive approach to security.
With the increasing importance of data protection and privacy regulations, such as GDPR and CCPA, organizations will need to focus more on securing sensitive data in their emails.
This may include implementing encryption, access controls, and data loss prevention (DLP) technologies.
Traditional authentication methods, such as passwords and two-factor authentication, are becoming less secure as attackers find new ways to steal credentials.
In the future, we may see more advanced authentication methods, such as biometrics and behavioral authentication, to provide better security.
The adoption of zero-trust security models is gaining momentum and will play a significant role in securing email communications.
Zero-trust security is an approach that assumes no trust, even for users and devices within the internal network.
It emphasizes continuous verification and strict access controls to protect sensitive data.
In the context of email security, a zero-trust model requires authentication and authorization for every access request, regardless of the user’s location or network.
This means that users and devices are not automatically trusted based on their network location but must authenticate themselves before gaining access to email systems and data.
Implementing AI-Powered Email security solutions can secure your business from today’s most dangerous email threats, such as Email Tracking, Blocking, Modifying, Phishing, Account Take Over, Business Email Compromise, Malware & Ransomware – Request Free Demo.
