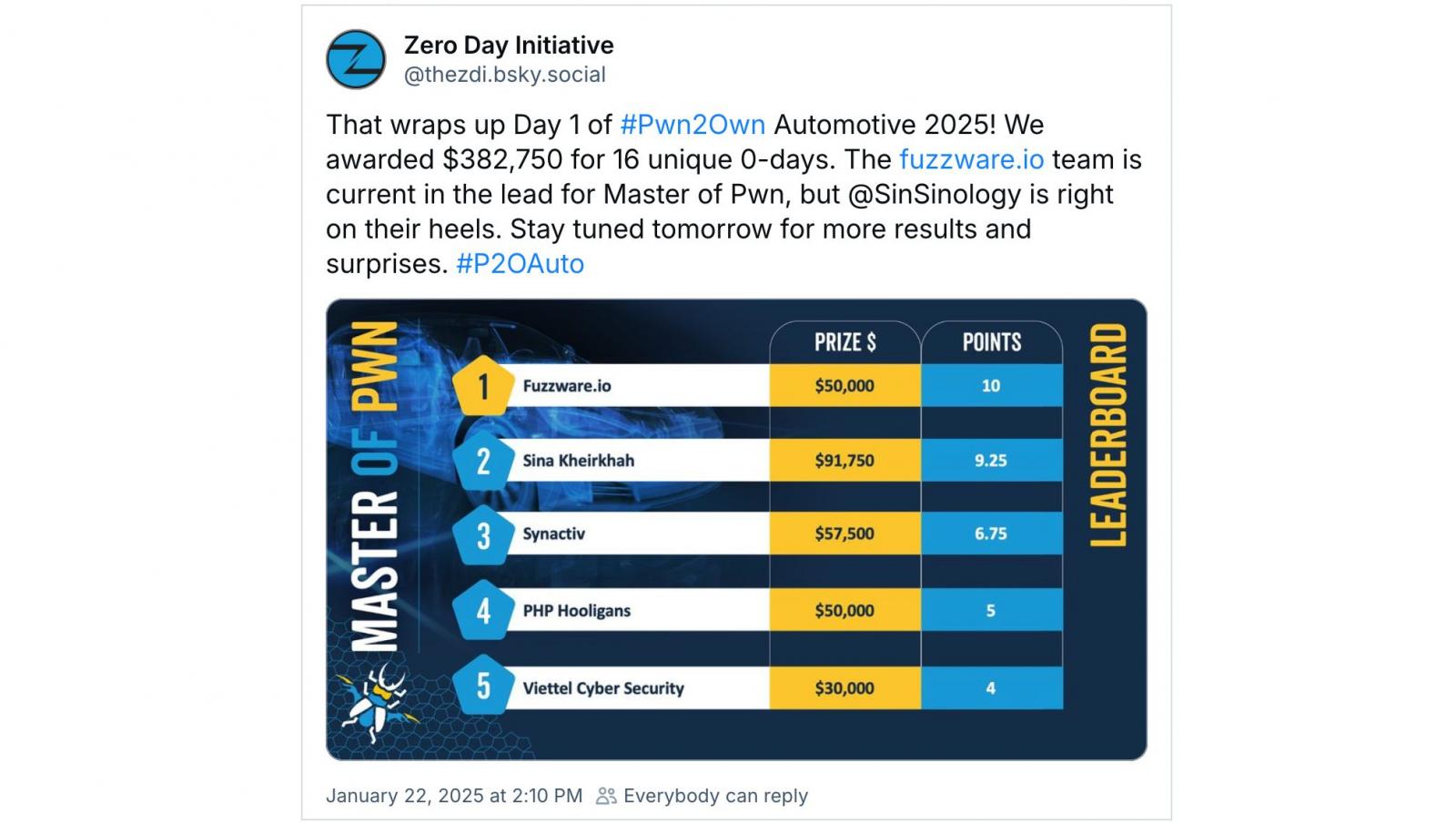
On the first day of Pwn2Own Automotive 2025, security researchers exploited 16 unique zero-days and collected $382,750 in cash awards.
Fuzzware.io is leading the competition after hacking the Autel MaxiCharger and Phoenix Contact CHARX SEC-3150 electric vehicle chargers using a stack-based buffer overflow and an origin validation error bug. This earned them $50,000 and 10 Master of Pwn points.
Sina Kheirkhah of Summoning Team also earned $91,750 and 9.25 Master of Pwn points after hacking the Ubiquiti and Phoenix Contact CHARX SEC-3150 EV chargers using a hard-coded cryptographic key bug and a combo of three zero-days (one of them previously known).
Synacktiv Team is in third place on the leaderboard and took home $57,500 after successfully demoing a bug in the OCPP protocol to hack the ChargePoint Home Flex (Model CPH50) using signal manipulation through the connector,
Security researchers from PHP Hooligans also successfully hacked a fully patched Autel charger using a heap-based buffer overflow and earned $50,000, while the Viettel Cyber Security team collected $20,000 after obtaining code execution on the Kenwood In-Vehicle Infotainment (IVI) using an OS command injection zero-day.
After the zero-day vulnerabilities are exploited and reported during Pwn2Own, vendors have 90 days to develop and release security patches before TrendMicro’s Zero Day Initiative publicly discloses them.
The Pwn2Own Automotive 2025 hacking competition, which focuses on automotive technologies, takes place in Tokyo from January 22 to January 24 during the Automotive World auto conference.
Throughout the contest, security researchers can target electric vehicle (EV) chargers, in-vehicle infotainment (IVI) systems, and car operating systems (i.e., Automotive Grade Linux, Android Automotive OS, and BlackBerry QNX).
While Tesla also provided a Model 3/Y (Ryzen-based) equivalent benchtop unit, contestants have only registered attempts against the company’s wall connector.
The complete schedule for this year’s automotive hacking contest is available here, while the schedule for the first day and the results for each challenge can be found here.
During the first edition of Pwn2Own Automotive in January 2024, hackers collected $1,323,750 for hacking Tesla twice and demonstrating 49 zero-day bugs in multiple electric car systems.
Two months later, during Pwn2Own Vancouver 2024, security researchers earned $1,132,500 after exploiting 29 zero-days (and some bug collisions). Synacktiv went home with $200,000 and a Tesla Model 3 car after hacking the ECU with Vehicle (VEH) CAN BUS Control in under 30 seconds.
