Cybersecurity researchers have uncovered a massive network of over 2,000 fraudulent online storefronts deliberately activated during the Black Friday and Cyber Monday shopping season to harvest consumer payment information and execute unauthorized financial transactions.
The discovery reveals two distinct but potentially coordinated phishing clusters that leverage shared infrastructure, automated templates, and brand impersonation tactics to exploit holiday shoppers seeking steep discounts.
The first cluster comprises more than 750 interconnected domains centered around Amazon-themed typosquatting, all utilizing uniform holiday countdown banners, fabricated trust indicators, and psychological urgency messaging.
Domains like amaboxreturns[.]com, amaznboxsaleus[.]com, and amazonreturnsbox[.]com deploy identical HTML flipclock holiday assets hosted on a shared suspicious CDN (cdn.cloud360[.]top) to create fake Black Friday, Cyber Monday, and Christmas sale environments.
The second cluster spans the broader .shop domain ecosystem and encompasses sites impersonating over 30 major consumer brands including Apple, Samsung, Dell, Cisco, HP, Logitech, Toshiba, Ray-Ban, Garmin, Shark, Seagate, Xiaomi, and Fujifilm.
A shared CSS structure enabling holiday-specific banners also showcasing the resource that was used to identify the other 750+ domains.
Analysis of the top 1,000 domains from this cluster revealed consistent Black Friday modal structures across numerous sites, indicating widespread reuse of the same scam-associated template.
Shell Websites Enable Payment Theft
These fraudulent storefronts capture complete billing and credit card details through fake checkout pages before redirecting victims to shell merchant websites that process PayPal and payment card transactions.
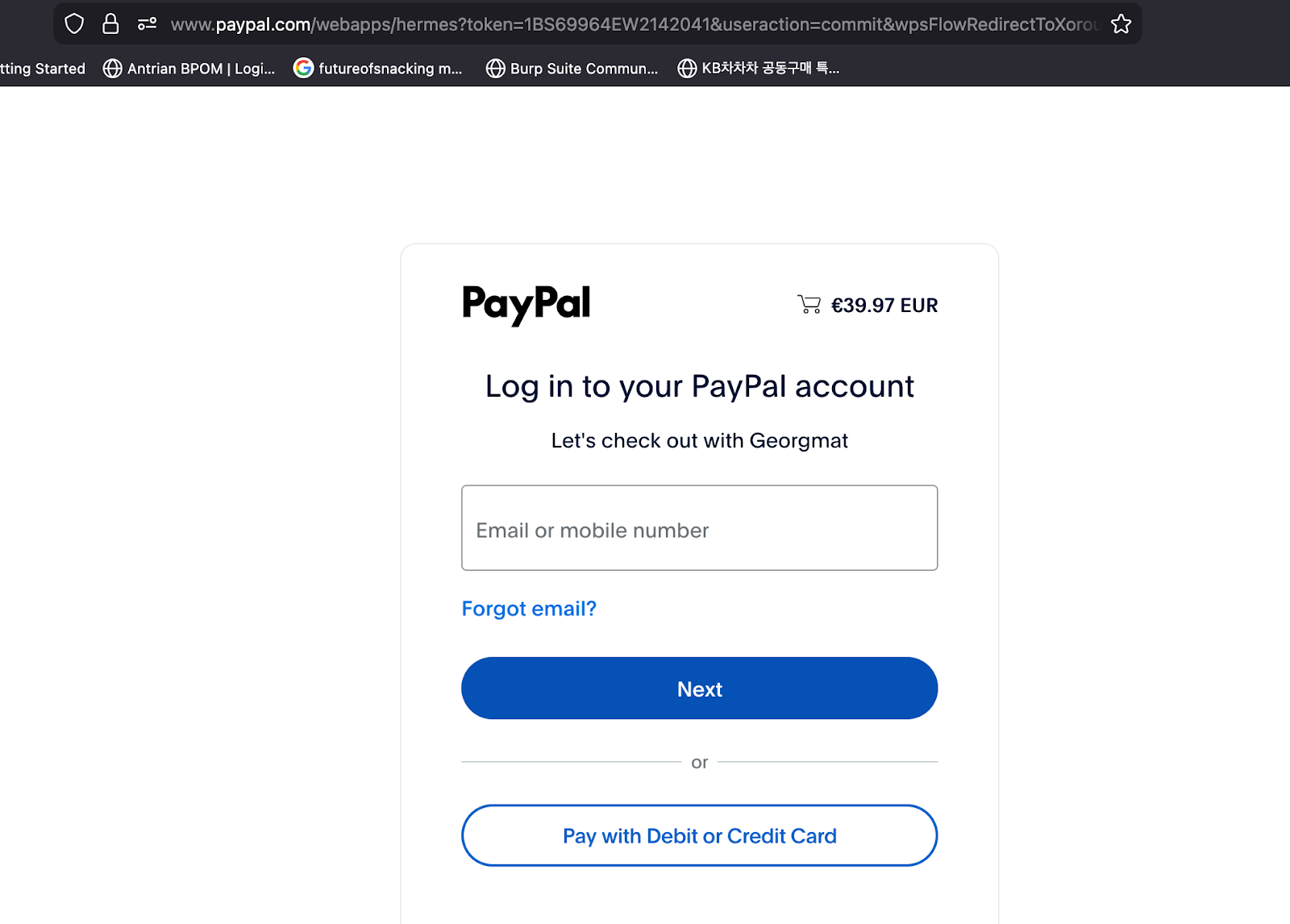
In documented cases, domains like georgmat[.]com hosted through China-based Alibaba Cloud Computing with registration details listing Guangdong serve as payment intermediaries that remain unflagged on security platforms like VirusTotal, reducing fraud detection likelihood and enabling attackers to complete unauthorized transactions.
Technical analysis uncovered shared hosting infrastructure across both campaigns, primarily utilizing Cloudflare’s content delivery network to conceal origin IP addresses and core attacker infrastructure.
WHOIS record statistics from the first cluster show domains registered through DNSPod (203 domains), Gname.com (121 domains), and Name.com (84 domains), with the majority created between November 2024 and March 2025 strategically timed for the holiday shopping season.
The second cluster demonstrated even greater automation, with approximately 70% of analyzed domains registered through Spaceship, Inc., predominantly in June and July 2025.
Sophisticated Social Engineering Tactics
Investigators identified recurring JavaScript files with identical body content (SHA-256 hash: 095a3ebc77f4e46b3adda543b61d90b7d3f20b41532c07772edd31908d060bb2) across thousands of .shop domains despite randomized filenames, providing a reliable signature for uncovering additional fraudulent sites.
Security experts warn shoppers to verify domain authenticity before entering payment information, avoid unfamiliar retailers offering unrealistic discounts, and scrutinize URLs for typosquatting patterns.
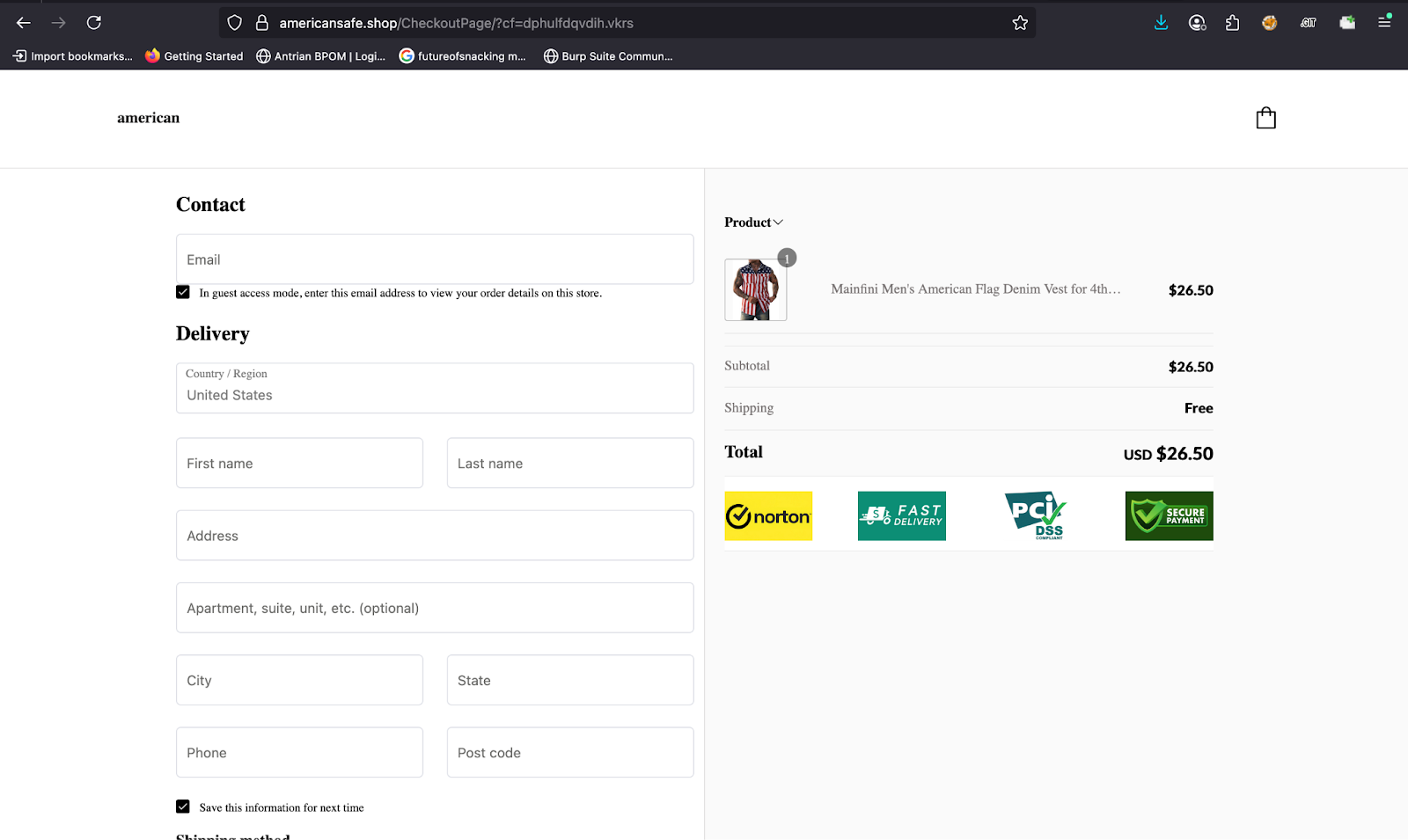
The fake stores employ multiple psychological manipulation techniques including fabricated trust badges claiming security certifications, countdown flipclock timers creating false urgency, pop-up notifications showing fake recent purchases, and scarcity messaging such as “Rush Buying” and “Tight Inventory.”
These elements pressure victims into completing transactions before recognizing the fraudulent nature of the sites.
While several domains have been taken down by registrars and hosting providers, many remain active, underscoring the continued risk to consumers during high-traffic holiday sale periods.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
