A new hacking group has leaked the configuration files, IP addresses, and VPN credentials for over 15,000 FortiGate devices for free on the dark web, exposing a great deal of sensitive technical information to other cybercriminals.
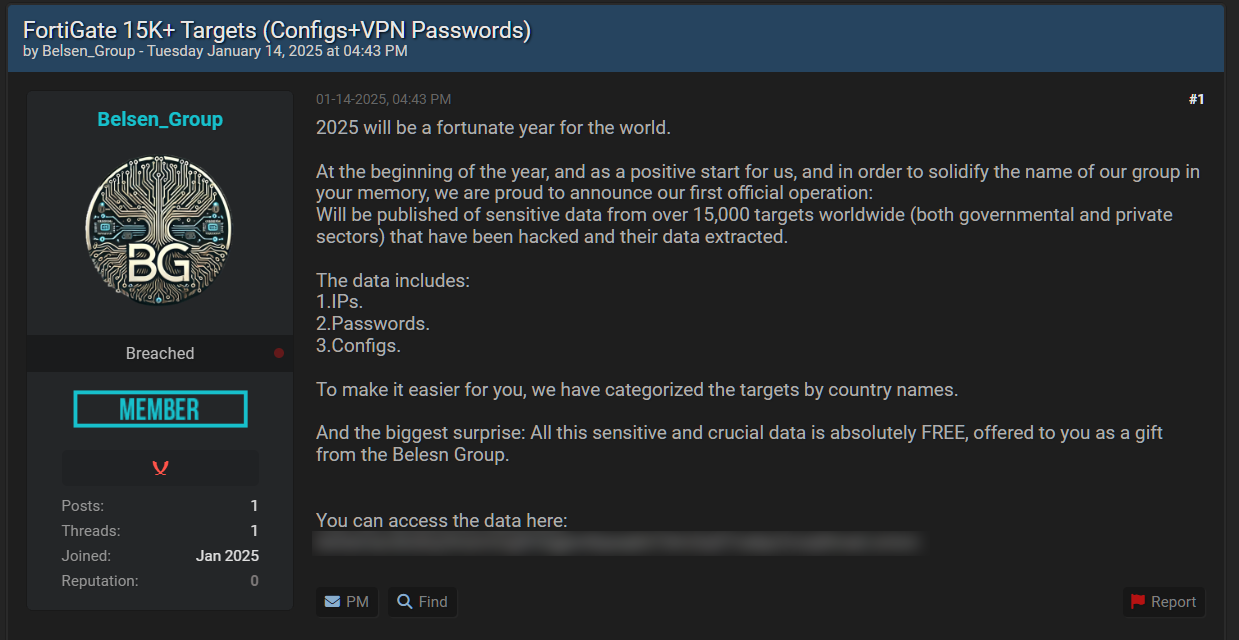
The data was leaked by the “Belsen Group,” a new hacking group first appearing on social media and cybercrime forums this month. To promote themselves, the Belsen Group has created a Tor website where they released the FortiGate data dump for free to be used by other threat actors.
“At the beginning of the year, and as a positive start for us, and in order to solidify the name of our group in your memory, we are proud to announce our first official operation: Will be published of sensitive data from over 15,000 targets worldwide (both governmental and private sectors) that have been hacked and their data extracted,” reads a hacking forum post.
Source: BleepingComputer
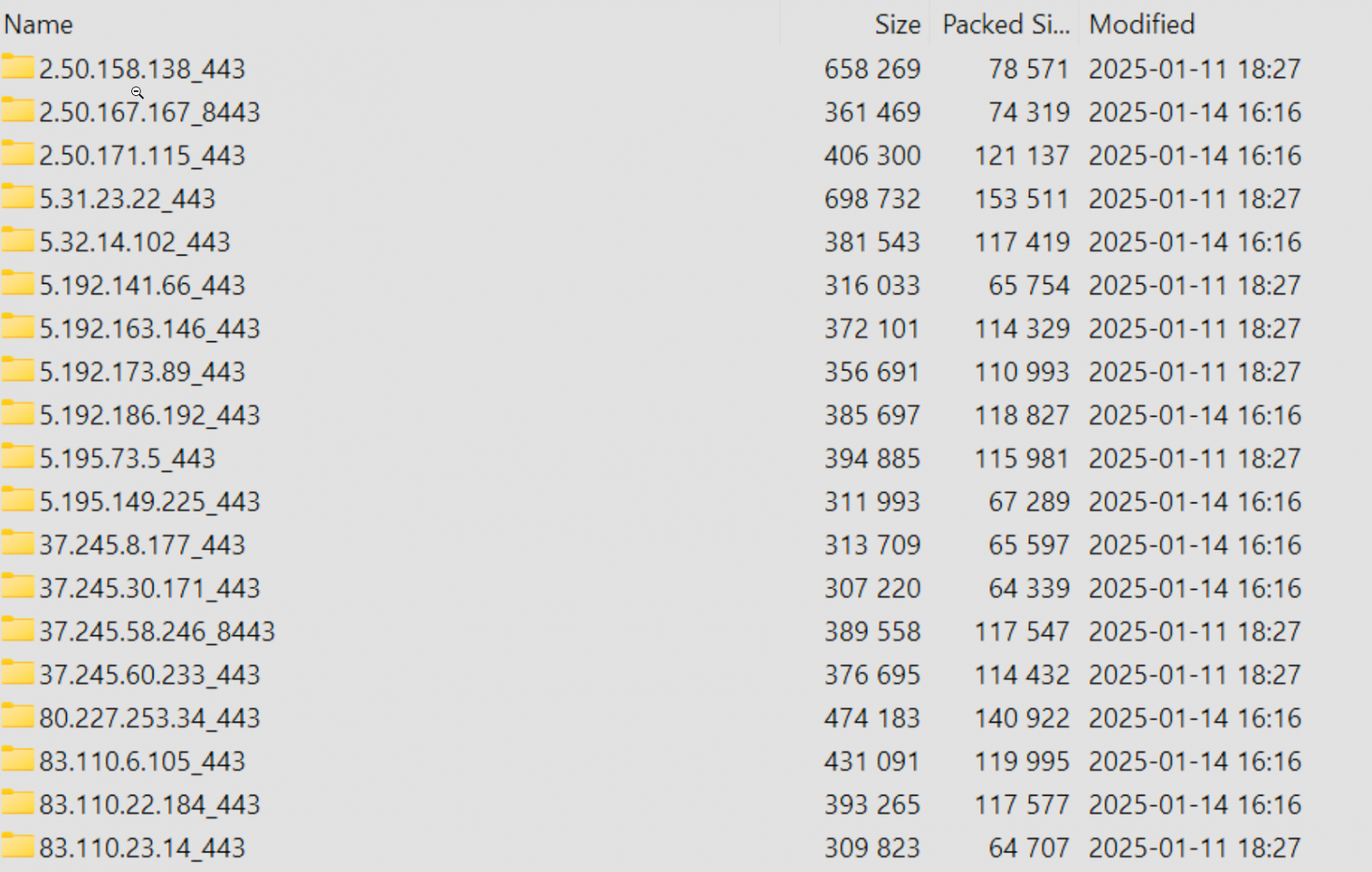
The FortiGate leak consists of a 1.6 GB archive containing folders ordered by country. Each folder contains further subfolders for each FortiGate’s IP address in that country.
Source: Beaumont
According to cybersecurity expert Kevin Beaumont, each IP address has a configuration.conf (Fortigate config dump) and a vpn-passwords.txt file, with some of the passwords in plain text. The configs also contain sensitive information, such as private keys and firewall rules.
In a blog post about the FortiGate leak, Beaumont says that the leak is believed to be linked to a 2022 zero-day tracked as CVE-2022–40684 that was exploited in attacks before a fix was released.
“I’ve done incident response on one device at a victim org, and exploitation was indeed via CVE-2022–40684 based on artefacts on the device. I’ve also been able to verify the usernames and password seen in the dump matches the details on the device,” explains Beaumont.
“The data appears to have been assembled in October 2022, as a zero day vuln. For some reason, the data dump of config has been released today, just over 2 years later.”
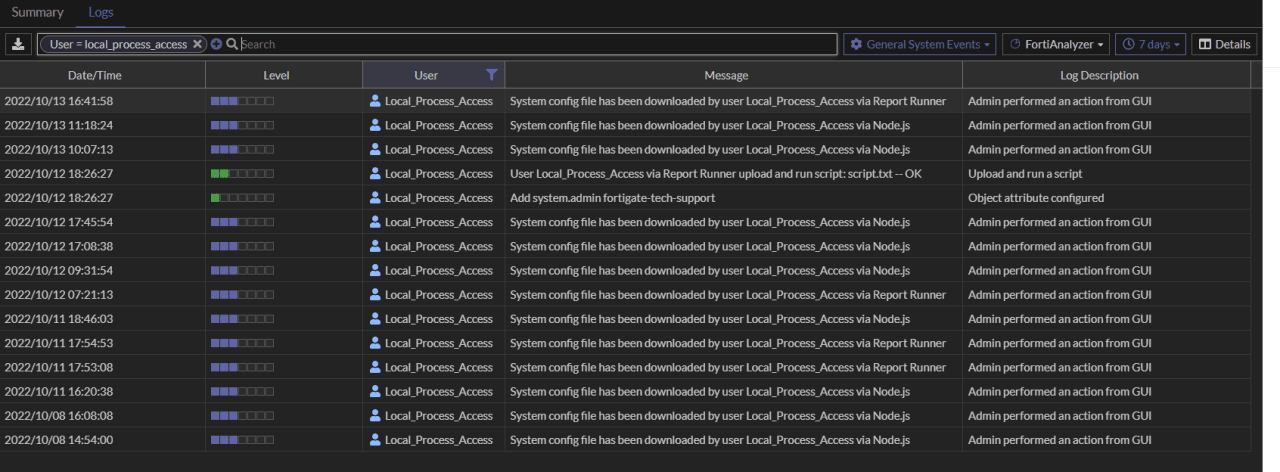
In 2022, Fortinet warned that threat actors were exploiting a zero-day tracked as CVE-2022–40684 to download config files from targeted FortiGate devices and then add a malicious super_admin account called ‘fortigate-tech-support’.
Source: Fortinet
German news site Heise analyzed the data leak and also said that it was gathered in 2022, with all devices utilizing FortiOS firmware 7.0.0-7.0.6 or 7.2.0-7.2.2.
“All devices were equipped with FortiOS 7.0.0-7.0.6 or 7.2.0-7.2.2, most with version 7.2.0. We did not find any FortiOS version in the data trove that was newer than version 7.2.2, released on October 3, 2022,” Heise reported.
However, FortiOS 7.2.2 fixed the CVE-2022–40684 flaw, so it would be unclear how devices running that version could be exploited with this vulnerability.
Even though these configuration files were collected in 2022, Beaumont warns that they still expose a lot of sensitive information about a network’s defenses.
This includes firewall rules and credentials that, if not changed at the time, should be changed immediately now that the data has been released to a broader pool of threat actors.
Beaumont says that he plans to release a list of the IP addresses in the leak so FortiGate admins can know if the leak impacted them.
BleepingComputer also reached out to both the threat actors and Fortinet with questions about the leak and will update the story if we receive a response.



