Russian cybercriminals have laundered over $35 million in stolen cryptocurrency linked to the devastating 2022 LastPass breach, according to new forensic analysis by blockchain intelligence firm TRM Labs.
The 2022 attack exposed encrypted password vaults belonging to roughly 30 million customers worldwide.
While the vaults were initially protected by encryption, attackers who downloaded them could crack weaker master passwords offline, creating a multi-year window to steal assets.
New waves of theft throughout 2024 and 2025 have weaponized those compromised credentials, particularly targeting users holding cryptocurrency.
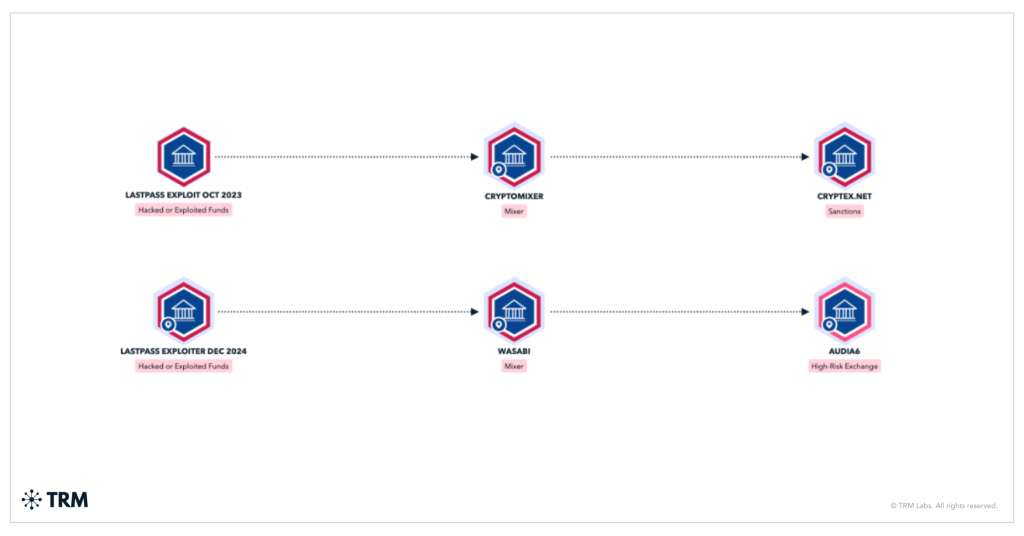
TRM’s analysis traced approximately $28 million in stolen Bitcoin through Wasabi Wallet, a cryptocurrency mixer designed to obscure transaction trails, and identified another $7 million moving through similar laundering pathways.
The stolen funds ultimately converged at two high-risk Russian exchanges: Cryptex (sanctioned by OFAC in 2024) and Audi6, both historically linked to cybercriminal activity.
“The attackers used a consistent operational signature,” TRM researchers explained. Stolen Bitcoin keys were imported into identical wallet software, producing recognizable transaction patterns.
Non-Bitcoin assets were rapidly converted to Bitcoin via swap services before being deposited into mixing services, a technique that, in theory, should obscure criminals’ identities.
Yet TRM’s proprietary “demixing” techniques revealed what mixers cannot hide: behavioral fingerprints that linked activity before and after mixing to the same actors.
Despite CoinJoin obfuscation, researchers identified clustering patterns, withdrawal timing, and wallet interactions that pointed to coordinated Russian cybercrime infrastructure.
The findings underscore two critical insights. First, mixing services are becoming less reliable as threat actors maintain consistent infrastructure over time.
Second, Russian exchanges continue functioning as systemic enablers of global cybercrime, facilitating millions in illicit fund transfers despite international enforcement pressure.
Early Wasabi withdrawals occurred within days of wallet drains, suggesting that attackers themselves orchestrated the laundering rather than reselling stolen keys to other criminals.
This operational continuity strengthens confidence in attribution of the original 2022 intrusion to Russian-based actors. However, definitive attribution of the original 2022 intrusion remains unconfirmed.
The LastPass case demonstrates how single credential breaches cascade across years, and how cybercriminal ecosystems exploit geographic financial infrastructure to monetize stolen data at scale.
For the 25 million affected users, the threat remains active a stark reminder that breached credentials represent persistent, long-tail risk.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
