Threat researchers have uncovered a sophisticated mobile malware campaign attributed to North Korea-linked threat actor Kimsuky, leveraging weaponized QR codes and fraudulent delivery service impersonations to trick users into installing remote access trojans on their smartphones.
The ENKI WhiteHat Threat Research Team identified the latest iteration of “DOCSWAP” malware being distributed through an intricate social engineering scheme that begins with phishing messages containing malicious URLs.
When users access these links from personal computers, they receive QR codes prompting them to switch to mobile devices for viewing.
The QR codes ultimately redirect victims to distribution servers hosting malicious Android applications disguised as legitimate services.
Leveraging APK metadata and infrastructure overlaps, we identified three additional malicious applications and seven C&C servers.
The distribution workflow employed server-side logic to detect the user’s device type, displaying security warnings and download prompts exclusively to Android users while blocking access from desktop browsers.
QR Code Attack Campaign
When victims clicked the “Install security app” button, the server initiated an APK download while simultaneously logging access attempts and transmission details to tracking databases.
Security researchers confirmed that attackers distributed the malware from infrastructure located at 27.102.137[.]181, creating fake delivery tracking pages that impersonated major logistics companies, including CJ Logistics.

The malicious application, named “SecDelivery.apk,” implements a sophisticated two-stage infection mechanism.
Upon execution, it decrypts an embedded encrypted APK file using a newly developed native decryption function rather than the Java-based XOR decryption employed in earlier DOCSWAP variants.
This evolved approach applies multiple obfuscation layers including bit inversion, 5-bit rotation, and XOR encryption with a 4-byte key, substantially increasing detection evasion capabilities.
The decrypted payload launches a persistent malicious service that provides complete remote access trojan functionality.
The malware requests an extensive array of dangerous permissions including file system access, SMS interception, phone state monitoring, and background service execution capabilities.
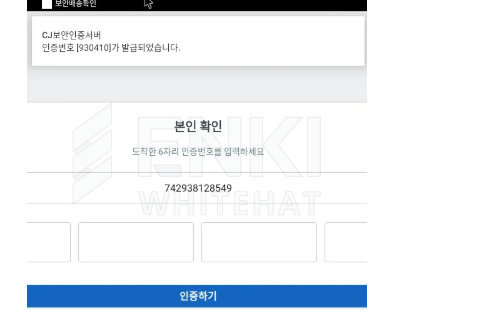
Notably, the application displays a fake authentication screen masquerading as an over-the-top verification system, requesting a hardcoded delivery tracking number to maintain the deception while users execute the malicious payload in the background.
The decrypted internal APK establishes command and control connections to the distribution server, implementing 57 distinct commands enabling attackers to steal sensitive data, record audio, capture keystrokes, and control infected devices remotely.
When the app runs, SplashActivity loads the encrypted resources embedded in the APK, obtains the various permissions required for malicious behavior.
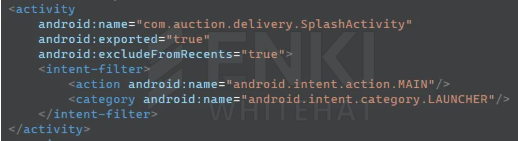
Researchers identified multiple indicators conclusively attributing this campaign to Kimsuky, including the presence of the “Million OK!!!!” signature string previously associated with the threat group’s phishing infrastructure.
Potential Risks and Impact
The investigation revealed infrastructure overlap with known Kimsuky Naver phishing campaigns, identical parameter structures, and shared command and control server infrastructure.
Delivery number is hardcoded within the APK as “742938128549”, and we assess the threat actor likely delivered it alongside the malicious URL during the initial access phase.
Additionally, embedded Korean-language comments within the malware code and distribution websites including phrases like “leave log when button is clicked” and “APK download started” strongly indicate the threat actors’ Korean language proficiency and ties to North Korean operations.
The comprehensive analysis uncovered seven additional command and control servers employing identical JARM fingerprints, as well as three additional malicious applications disguised as delivery services, cryptocurrency airdrops, and VPN applications.
Researchers also documented proxy-based phishing sites harvesting Naver and Kakao credentials from victims through sophisticated login credential interception routines.
Security professionals recommend users verify link destinations before clicking, particularly from unknown senders, and adopt conservative evaluation of app permission requests.
Organizations should implement mobile threat detection solutions, enforce application vetting policies, and educate employees regarding sophisticated phishing techniques targeting mobile platforms.
The campaign demonstrates evolving North Korean capabilities in mobile exploitation and underscores the critical importance of mobile security awareness across enterprise and consumer environments.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
