The North Korean state-sponsored Lazarus hacking group has launched a sophisticated cyberespionage campaign targeting European defense contractors involved in uncrewed aerial vehicle (UAV) manufacturing.
The attacks appear directly linked to North Korea’s efforts to accelerate its domestic drone production capabilities through industrial espionage.
The targeted organizations include a metal engineering firm, an aircraft component manufacturer, and a specialized defense company, with at least two heavily involved in UAV technology development and production.
The campaign represents a new wave of Operation DreamJob, Lazarus’s signature social engineering operation that uses fake job offers at prestigious companies as bait.
Starting in late March 2025, ESET identified multiple attacks targeting three defense-sector companies across Southeastern and Central Europe.
Victims receive fraudulent job descriptions alongside trojanized PDF readers, which deliver malware when executed. This deceptive tactic has proven remarkably effective despite widespread security awareness campaigns.
The attackers deployed ScoringMathTea, a sophisticated remote access trojan (RAT) that has served as Lazarus’s payload of choice for three years.
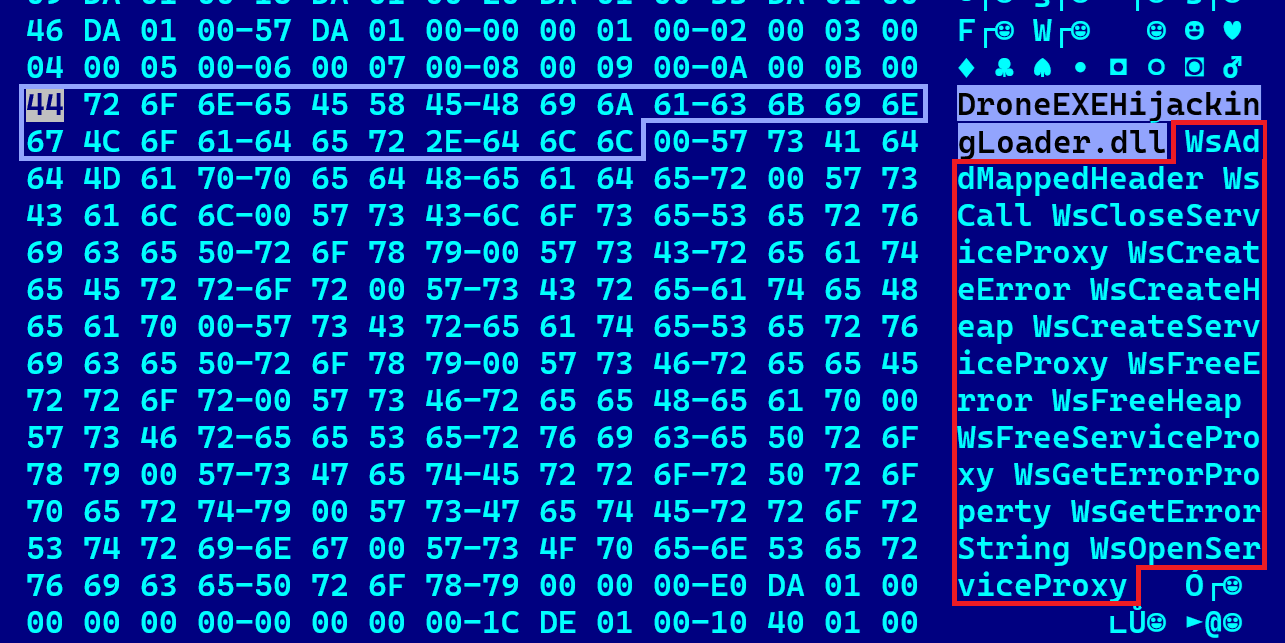
BinMergeLoader leverages the Microsoft Graph API and uses Microsoft API tokens for authentication.
First observed in October 2022, ScoringMathTea supports approximately 40 commands, enabling attackers to manipulate files and processes, collect system information, establish TCP connections, and execute downloaded payloads.
One dropper sample discovered by researchers contained the internal name “DroneEXEHijackingLoader.dll,” providing a direct link to the campaign’s focus on UAV technology theft.
The malware leverages DLL side-loading techniques and trojanizes legitimate open-source projects from GitHub including TightVNC Viewer, MuPDF reader, and plugins for Notepad++ and WinMerge to evade detection.
ESET researchers noted significant evolution in the group’s tactics, including new DLL proxying libraries and improved selection of open-source projects for trojanization.
The malware uses compromised WordPress servers for command-and-control communication, typically storing server components within theme or plugin directories.
The timing and target selection strongly suggest the campaign aims to steal proprietary UAV designs, manufacturing processes, and industrial know-how.
North Korea has invested heavily in domestic drone capabilities, with recent reports indicating Pyongyang is developing low-cost attack UAVs for potential export to African and Middle Eastern markets. Russia is reportedly assisting North Korea in producing knockoff Iranian Shahed suicide drones.
North Korea’s flagship reconnaissance drone, the Saetbyol-4, appears as a carbon copy of the Northrop Grumman RQ-4 Global Hawk, while the Saetbyol-9 combat drone closely resembles General Atomics’ MQ-9 Reaper.
These designs demonstrate North Korea’s reliance on reverse engineering and intellectual property theft to advance its military capabilities.
At least one targeted company manufactures critical components for UAV models currently deployed in Ukraine, which North Korean forces may have encountered on the frontline in Russia’s Kursk region, where North Korean troops were deployed in 2025.
Additionally, the company is involved in advanced single-rotor drone development unmanned helicopter technology that Pyongyang is actively developing but has not successfully militarized.
Attribution and Broader Context
ESET attributed the attacks to Lazarus with high confidence based on multiple indicators: the social engineering methodology, trojanization of GitHub open-source projects for DLL side-loading, deployment of ScoringMathTea, and targeting of European aerospace and defense sectors.
Lazarus, also known as HIDDEN COBRA, is an advanced persistent threat (APT) group linked to North Korean intelligence services and active since at least 2009.
The group is responsible for high-profile incidents including the 2016 Sony Pictures Entertainment hack, tens-of-millions-of-dollar cyberheists, the 2017 WannaCry ransomware outbreak, and ongoing attacks against South Korean infrastructure.
Security experts recommend defense contractors implement rigorous employee training on social engineering tactics, particularly fake recruitment lures.
Organizations should scrutinize job offers from unexpected sources, verify executable files before opening, and deploy advanced endpoint detection solutions capable of identifying trojanized legitimate software.
Network segmentation and privileged access management can limit lateral movement if initial compromise occurs.
IoCs
| SHA-1 | Filename | Detection | Description |
|---|---|---|---|
| 28978E987BC59E75CA22562924EAB93355CF679E | TSMSISrv.dll | Win64/NukeSped.TL | QuanPinLoader. |
| 5E5BBA521F0034D342CC26DB8BCFECE57DBD4616 | libmupdf.dll | Win64/NukeSped.TE | A loader disguised as a MuPDF rendering library v3.3.3. |
| B12EEB595FEEC2CFBF9A60E1CC21A14CE8873539 | radcui.dll | Win64/NukeSped.TO | A dropper disguised as a RemoteApp and Desktop Connection UI Component library. |
| 26AA2643B07C48CB6943150ADE541580279E8E0E | HideFirstLetter.DLL | Win64/NukeSped.TO | BinMergeLoader. |
| 0CB73D70FD4132A4FF5493DAA84AAE839F6329D5 | libpcre.dll | Win64/NukeSped.TP | A loader that is a trojanized libpcre library. |
| 03D9B8F0FCF9173D2964CE7173D21E681DFA8DA4 | webservices.dll | Win64/NukeSped.RN | A dropper disguised as a Microsoft Web Services Runtime library. |
| 71D0DDB7C6CAC4BA2BDE679941FA92A31FBEC1FF | N/A | Win64/NukeSped.RN | ScoringMathTea. |
| 87B2DF764455164C6982BA9700F27EA34D3565DF | webservices.dll | Win64/NukeSped.RW | A dropper disguised as a Microsoft Web Services Runtime library. |
| E670C4275EC24D403E0D4DE7135CBCF1D54FF09C | N/A | Win64/NukeSped.RW | ScoringMathTea. |
| B6D8D8F5E0864F5DA788F96BE085ABECF3581CCE | radcui.dll | Win64/NukeSped.TF | A loader disguised as a RemoteApp and Desktop Connection UI Component library. |
| 5B85DD485FD516AA1F4412801897A40A9BE31837 | RCX1A07.tmp | Win64/NukeSped.TH | A loader of an encrypted ScoringMathTea. |
| B68C49841DC48E3672031795D85ED24F9F619782 | TSMSISrv.dll | Win64/NukeSped.TL | QuanPinLoader. |
| AC16B1BAEDE349E4824335E0993533BF5FC116B3 | cache.dat | Win64/NukeSped.QK | A decrypted ScoringMathTea RAT. |
| 2AA341B03FAC3054C57640122EA849BC0C2B6AF6 | msadomr.dll | Win64/NukeSped.SP | A loader disguised as a Microsoft DirectInput library. |
| CB7834BE7DE07F89352080654F7FEB574B42A2B8 | ComparePlus.dll | Win64/NukeSped.SJ | A trojanized Notepad++ plugin disguised as a Microsoft Web Services Runtime library. A dropper from VirusTotal. |
| 262B4ED6AC6A977135DECA5B0872B7D6D676083A | tzautosync.dat | Win64/NukeSped.RW | A decrypted ScoringMathTea, stored encrypted on the disk. |
| 086816466D9D9C12FCADA1C872B8C0FF0A5FC611 | N/A | Win64/NukeSped.RN | ScoringMathTea. |
| 2A2B20FDDD65BA28E7C57AC97A158C9F15A61B05 | cache.dat | Win64/NukeSped.SN | A downloader similar to BinMergeLoader built as a trojanized NPPHexEditor plugin. |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




