Makop, a ransomware strain derived from Phobos, continues to pose a significant threat by exploiting exposed Remote Desktop Protocol (RDP) systems and integrating new attack components, including antivirus-killer modules and advanced privilege-escalation exploits.
Recent investigations by Acronis TRU researchers reveal that Makop operators have evolved their methodology to include multiple evasion techniques and secondary payload delivery mechanisms.
The attack chain follows a methodical pattern beginning with RDP exploitation through brute-force attacks targeting weak credentials, followed by network reconnaissance, privilege escalation, and ultimately encryption.
Operators demonstrate a pragmatic approach, abandoning attacks when security solutions prove too resilient, indicating a focus on minimizing effort while maximizing impact.
Makop operators primarily gain initial access by exploiting publicly exposed RDP services, leveraging weak or reused credentials through brute-force attacks.
The group has been observed using NLBrute, an older hacking tool from 2016 that automates large-scale RDP password guessing.
Once inside victim networks, attackers employ network scanning tools including NetScan and Advanced IP Scanner to identify active hosts and map network infrastructure for lateral movement activities.
Defense Evasion Tactics
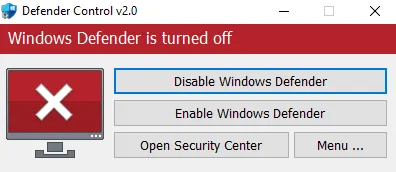
A critical evolution in Makop’s toolkit involves sophisticated defense evasion techniques. Attackers deploy multiple antivirus killers, including Defender Control and Disable Defender, to neutralize Microsoft Defender protections.
The group also leverages BYOVD (Bring Your Own Vulnerable Driver) techniques, exploiting legitimate signed drivers such as ThrottleStop.sys and hlpdrv.sys to gain kernel-level access and turn off EDR solutions.
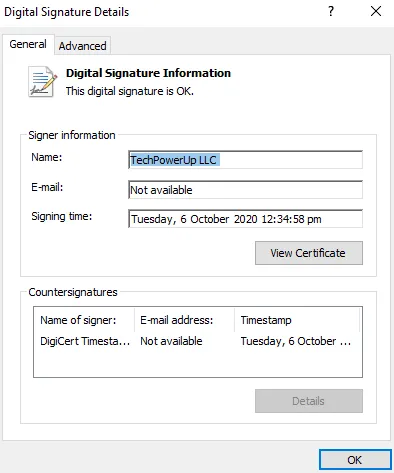
Additionally, operators use tailored uninstall software targeting region-specific security solutions.
The discovery of a customized Quick Heal AV uninstaller aligns with telemetry showing that 55% of Makop attacks target Indian organizations, suggesting attackers adapt their toolkit based on geographical victim profiles.
Makop operators maintain an extensive collection of local privilege escalation (LPE) exploits spanning from older to recent vulnerabilities.
The most frequently exploited CVEs include CVE-2017-0213, CVE-2018-8639, CVE-2021-41379, and CVE-2016-0099.
This diverse exploit portfolio enables operators to escalate privileges across different Windows versions and maintain redundancy when individual exploits fail.
GuLoader Integration
Attackers employ credential dumping tools such as Mimikatz, LaZagne, and NetPass to extract plaintext passwords, NTLM hashes, and cached credentials from victim systems.
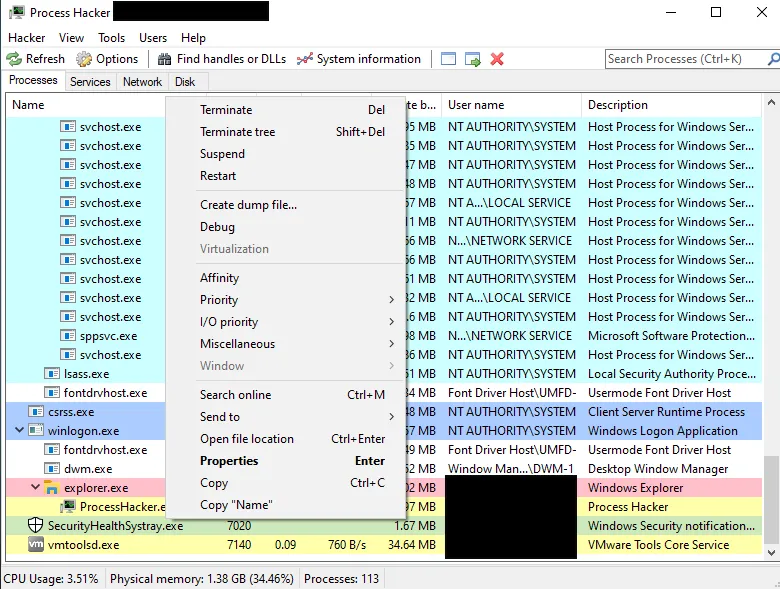
Lastly, they also abused applications such as Process Hacker and IOBitUnlocker. Both applications are legitimate but are abused by threat actors to easily terminate processes and delete programs.
These stolen credentials facilitate lateral movement and expand attacker access across organizational infrastructure.
A notable development involves the integration of GuLoader, a downloader trojan traditionally associated with delivering malware like AgentTesla and FormBook.
This marks the first documented case of GuLoader being used to distribute Makop ransomware, indicating an evolution toward more sophisticated secondary payload delivery mechanisms.
Makop attacks predominantly target organizations in India (55%), with additional incidents reported in Brazil, Germany, and other regions.
This distribution reflects opportunistic targeting of networks with lower security posture rather than geographical preference, as operators exploit weak authentication practices and lack of multi-factor authentication (MFA).
Organizations must prioritize securing RDP services through strong authentication mechanisms, implementing multi-factor authentication, and conducting regular patching of known LPE vulnerabilities.
Regular network monitoring, application whitelisting, and behavioral analysis can effectively detect and prevent Makop’s exploitation attempts before encryption occurs.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
