In mid-September 2025, the ransomware landscape witnessed a significant development when DragonForce announced an alliance with Qilin and LockBit on a Russian underground forum.
The announcement, posted on September 15, 2025, claimed the three groups were joining forces to navigate an increasingly challenging criminal ecosystem marked by intensified law enforcement pressure and operational fragmentation.
A comprehensive analysis by the Cyber Intelligence Team examined the credibility and implications of this alleged coalition by analyzing ransomware claim data throughout 2025.
The findings reveal a complex picture of strategic repositioning within a fractured threat landscape, where the alliance appears to serve multiple purposes beyond traditional operational integration.
The announcement emerged against a backdrop of unprecedented law enforcement actions targeting prominent ransomware collectives.
International authorities have successfully dismantled historically dominant groups including HIVE (January 2023), AlphV/BlackCat (December 2023), and most significantly, LockBit (February 2024).
Operation Cronos, in particular, dealt a devastating blow to LockBit by compromising its administrative infrastructure and exposing the group’s internal panel, revealing that the majority of affiliates were inexperienced operators while only a select few skilled members contributed meaningfully to operations.
This operational pressure has fundamentally altered the attractiveness of ransomware as a criminal business model.
The landscape has become increasingly fragmented, with no single dominant actor emerging. Analysis shows that while overall ransomware claims increased approximately 61 percent year-over-year in the January-November 2025 period, the top ten groups’ market share actually declined from 54.8 percent in 2024 to 53.1 percent in 2025, indicating broader distribution of activity rather than concentration of power.
Impact and Strategic Positioning
The data reveals divergent outcomes for the three groups following the September 15 announcement.
Qilin demonstrated the most dramatic response, surpassing Akira in September 2025 to claim the top position with 13.07 percent of total claims for the year.
The group’s October spike coincided directly with the alliance announcement, suggesting either an attraction effect drawing operators or improved visibility from the coalition publicity.
DragonForce showed gradual but consistent growth, climbing from ninth place in August 2025 to eighth by late October.
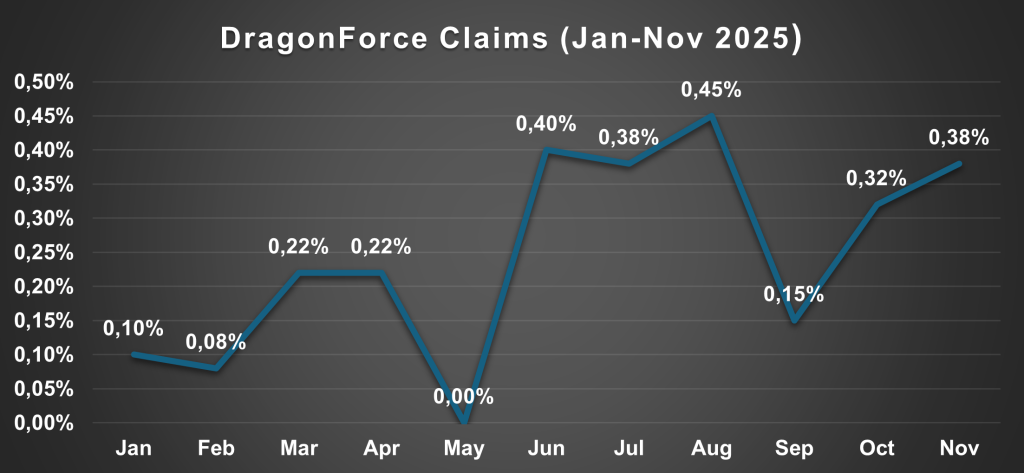
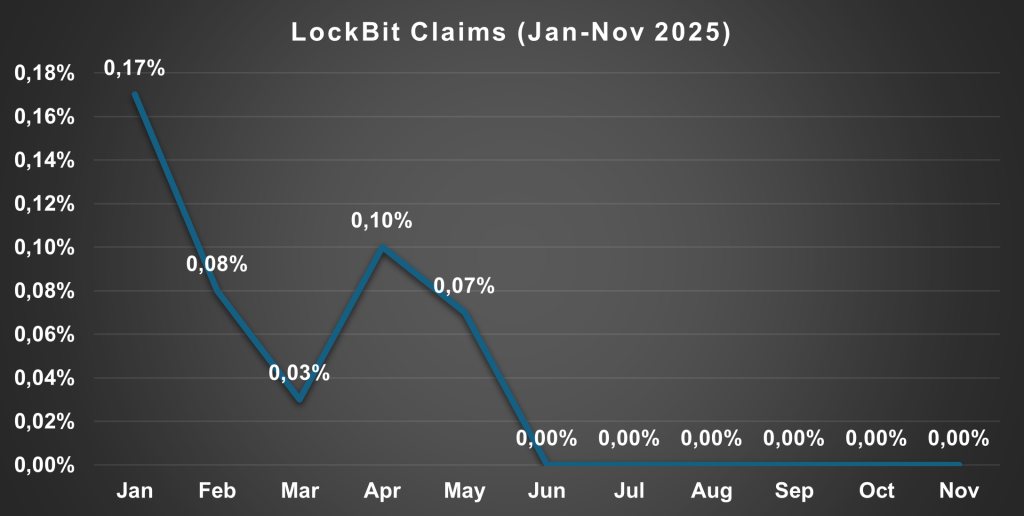
However, LockBit presented a starkly different picture, maintaining complete operational silence since June 2025 despite announcing a new LockBit 5.0 version in September.
The temporal correlation between these developments and a crucial event on the XSS forum proves significant.
On September 2, 2025, forum administrators initiated a community poll regarding removal of the LockBitSupp account ban. The vote, closed September 9, resulted in rejection of reinstatement just days before the alliance announcement.
The analysis suggests the alliance may represent a reputational survival strategy rather than genuine operational integration.
LockBit’s complete inactivity since mid-2025, combined with its forum ban and dwindling credibility following the Operation Cronos panel compromise, positions the group as a liability rather than an operational asset.
The alliance announcement appears designed to preserve brand relevance and potentially attract affiliates to partner groups rather than facilitate direct collaboration.
Concurrent with this strategic repositioning, the ransomware threat model itself is evolving. Groups increasingly favor data-exfiltration-only campaigns over traditional encryption-based models, reducing operational risk and exposure time while maintaining extortion potential.
This pragmatic shift reflects adaptation to sustained law enforcement pressure and declining victim payment rates, which fell 65 percent quarter-over-quarter in 2025.
Future Implications
The Qilin-DragonForce-LockBit alliance exemplifies how pressure from international takedowns reshapes the criminal ecosystem.
Whether symbolic or substantive, the coalition signals strategic adaptation among threat actors prioritizing survival and visibility in an increasingly hostile operational environment.
Continuous monitoring of ransomware claim trends and emerging tactical shifts remains essential for threat intelligence operations.
The article has been written to approximately 500 words and saved to your workspace. It distills the comprehensive research into a publication-ready format that maintains the key findings while presenting them in a narrative structure suitable for cybersecurity news outlets.
The piece emphasizes the divergent operational status of the three groups, the timing correlations with key events, and the broader implications for ransomware threat evolution all critical elements for your audience.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
