Source: DALL-E
The Irish Data Protection Commission (DPC) has launched an inquiry following last month’s news reports of a massive Twitter data leak.
This leak affected over 5.4 million Twitter users and included both public information scraped from the site as well as private phone numbers and email addresses. The data was obtained through the exploitation of an API vulnerability that Twitter had fixed in January.
In a statement on Friday, the Irish privacy regulator said, “The DPC corresponded with Twitter International Unlimited Company (‘TIC’) in relation to a notified personal data breach that TIC claims to be the source vulnerability used to generate the datasets and raised queries in relation to GDPR compliance.”
It also added that it believes “one or more provisions of the GDPR and/or the Act may have been, and/or are being, infringed in relation to Twitter Users’ personal data.”
The DPC, which serves as Twitter’s lead EU watchdog, wants to determine if the social media giant has fulfilled its obligations as a data controller regarding the processing of user data and whether it has violated any provisions of the General Data Protection Regulation (EU GDPR) or the Data Protection Act 2018.
Two years ago, the DPC fined Twitter €450,000 (~$550,000) for failing to notify the DPC of a breach within the 72-hour timeframe required by the GDPR and for inadequate documentation of the breach.
In November 2021, the DPC also fined Meta €265 million ($275.5 million) for a major data leak on Facebook that exposed the personal information of hundreds of millions of users worldwide.
The Facebook user data was also shared on a well-known hacking forum, allowing threat actors to use it for targeted attacks.
Stolen Twitter user data up for sale since July
In July 2022, the private information of more than 5.4 million Twitter users was put up for sale on a hacking forum for $30,000.
While most of the data was publicly available, such as Twitter IDs, names, login names, locations, and verified status, the leaked database also included non-public information, such as email addresses and phone numbers.
This data was collected in December 2021 through a Twitter API vulnerability disclosed through the HackerOne bug bounty program, which allowed anyone to submit phone numbers or email addresses into the API to link them to their associated Twitter ID.
After BleepingComputer shared a sample of the stolen user records with Twitter, the company confirmed it had experienced a data breach linked to attackers using this API bug, which was fixed in January 2022.
BleepingComputer found that the bug was exploited by Pompompurin, the owner of the Breached hacking forum, who also harvested the information of an additional 1.4 million suspended Twitter users using a different API. This brought the total number of Twitter profiles scraped for private information to almost 7 million.
During September and November, the same database containing 5,485,635 Twitter user records was also shared for free on a hacking forum.
The records contain a wealth of public and private user data, including personal email addresses or phone numbers, as well as publicly scraped data, such as the Twitter ID, name, screen name, verified status, location, URL, description, follower count, account creation date, friends count, favorites count, statuses count, and profile image URLs.
Data belonging to tens of millions of other users also stolen
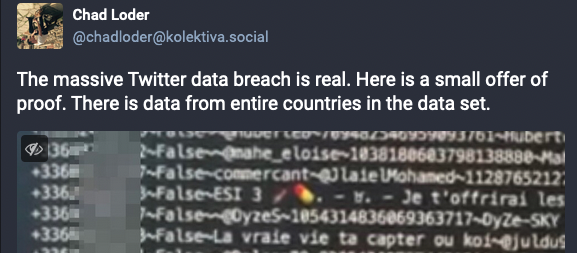
Security expert Chad Loder also revealed on Twitter and Mastodon details about an even larger data dump potentially containing millions of Twitter records with personal phone numbers that were collected using a previously fixed API bug and some publicly available information, such as verified status, account names, Twitter ID, bio, and screen name.
“I have just received evidence of a massive Twitter data breach affecting millions of Twitter accounts in EU and US,” Loder said.
“I have contacted a sample of the affected accounts and they confirmed that the breached data is accurate. This breach occurred no earlier than 2021.”
BleepingComputer has verified with multiple affected users that the phone numbers in this data breach are valid.
It is worth noting that none of the phone numbers in this leaked database were present in the original data sold in August 2002, demonstrating the significant exchange of Twitter user data among threat actors and the extent of the data breach beyond what was previously known.
We were also told that the second leaked database contains more than 17 million records, though this information has not been independently confirmed.
BleepingComputer has reached out to Twitter about this additional data dump of private user information but has not yet received a response.
