A pharmaceutical company lost cancer treatment funding, a Florida condo association lost half a million dollars, and thousands more fell victim—all thanks to a $24-per-month criminal marketplace.
Microsoft seized control of RedVDS, a global cybercrime subscription service that enabled fraud at industrial scale, marking the tech giant’s 35th civil action against cybercrime infrastructure. The coordinated takedown, executed alongside law enforcement in the United States, United Kingdom, Germany and Europol, shut down a marketplace that powered millions in fraud losses with virtual computers available for less than the cost of a Netflix subscription.
RedVDS operated like any legitimate software-as-a-service platform, complete with a customer dashboard, loyalty programs and referral bonuses. But instead of productivity tools, it sold disposable virtual machines running unlicensed Windows software that criminals used to launch attacks anonymously and at scale.
“For as little as $24 a month, RedVDS provides criminals with access to disposable virtual computers that make fraud cheap, scalable, and difficult to trace,” Steven Masada, assistant general counsel of Microsoft’s Digital Crimes Unit, wrote in the company’s announcement.
The service fueled roughly $40 million in reported fraud losses in the United States alone since March 2025. But that figure represents only confirmed cases—the actual damage likely reaches far higher because fraud frequently goes unreported and victims span the globe.
Among those hit hardest was H2-Pharma, an Alabama pharmaceutical company that lost more than $7.3 million earmarked for lifesaving cancer treatments, mental health medications and children’s allergy drugs. The Gatehouse Dock Condominium Association in Florida lost nearly $500,000 in resident-contributed funds intended for essential repairs. Both organizations joined Microsoft as co-plaintiffs in the legal action.


RedVDS Sent 1 Million Phishing Mails Daily
The scale of RedVDS’s operations reveals how cybercrime-as-a-service platforms have industrialized digital theft. In just one month, more than 2,600 distinct RedVDS virtual machines sent an average of one million phishing messages daily to Microsoft customers alone. While Microsoft’s defenses blocked most attempts—part of the 600 million cyberattacks it stops every day—the sheer volume meant some still reached inboxes.
Since September 2025, RedVDS-enabled attacks compromised or fraudulently accessed more than 191,000 organizations worldwide. These figures represent only Microsoft’s visibility across its customer base, suggesting the true impact extends far beyond what any single company can measure.
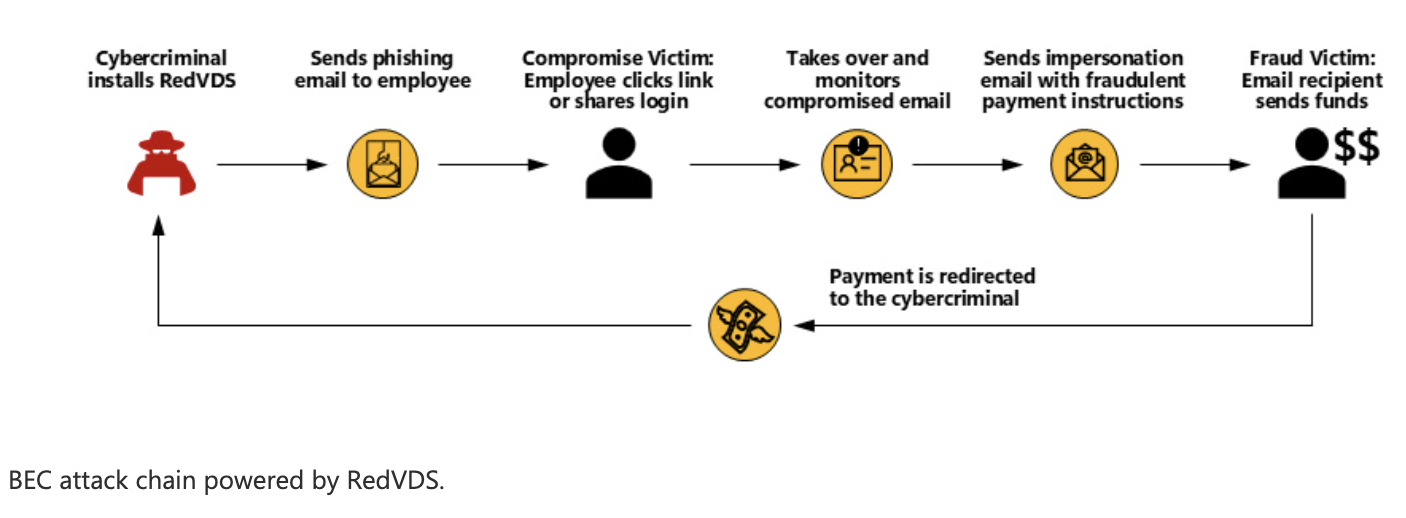
Criminals weaponized RedVDS primarily for business email compromise, a sophisticated fraud tactic where attackers infiltrate email accounts, monitor conversations and wait for the perfect moment to strike. When a payment or wire transfer approaches, they impersonate trusted parties and redirect funds, often moving money within seconds.

Special Focus on Real Estate Domain, Among Others
The service proved especially devastating in real estate transactions. Attackers compromised accounts belonging to realtors, escrow agents and title companies, then sent strategically timed emails with fraudulent payment instructions designed to divert closing funds and escrow payments. Microsoft observed RedVDS activity affecting more than 9,000 customers in the real estate sector, with particularly severe impacts in Canada and Australia.
But the threat extended far beyond property deals. Construction companies, manufacturers, healthcare providers, logistics firms, educational institutions and legal services all fell victim to RedVDS-enabled scams that disrupted everything from production lines to patient care.
What made RedVDS particularly dangerous was how criminals enhanced their attacks with artificial intelligence. Attackers paired the service with generative AI tools that identified high-value targets faster and generated realistic, multimedia email threads mimicking legitimate correspondence. In hundreds of cases, Microsoft observed criminals leveraging face-swapping, video manipulation and voice cloning AI to impersonate individuals with disturbing accuracy.
The coordinated takedown seized two domains hosting RedVDS’s marketplace and customer portal while laying groundwork to identify the individuals behind the operation. Germany’s Public Prosecutor’s Office Frankfurt am Main and the German State Criminal Police Office Brandenburg participated in the action, while Europol’s European Cybercrime Centre worked to disrupt the broader network of servers and payment systems supporting RedVDS customers.
Microsoft’s action builds on the company’s sustained strategy through its Digital Crimes Unit, which has now launched 35 civil actions targeting cybercrime infrastructure. The company also participates in global initiatives including the National Cyber-Forensics and Training Alliance and the Global Anti-Scam Alliance .
With the RedVDS disruption, Microsoft has shown a shift in approach from chasing individual attackers to dismantling the services enabling crime at scale. As cybercrime-as-a-service platforms continue emerging, this infrastructure-focused strategy aims to make criminal operations harder to sustain and easier for potential victims to avoid.
Masada stressed that falling victim to these schemes should carry no stigma, noting that organized, professional criminal groups execute attacks by intercepting and manipulating legitimate communications between trusted parties.
Simple precautions can significantly reduce risk: questioning urgent requests, verifying payment instructions through known contact numbers, watching for subtle email address changes, enabling multifactor authentication, keeping software updated and reporting suspicious activity to law enforcement.
