Microsoft has fixed a known issue triggering Windows Security warnings that Local Security Authority (LSA) Protection is off by removing the feature’s UI from settings.
LSA Protection helps defend Windows users against credential theft by preventing untrusted code from being injected into the LSASS.exe process to dump its memory or extract information.
Microsoft acknowledged a known issue causing persistent alerts asking for Windows restarts following a stream of reports mentioning “Local Security Authority protection is off. Your device may be vulnerable.” warnings even though LSA Protection was already enabled.
As the company revealed, the issue affects Windows 11 21H2 and 22H2 systems, and it was caused by a buggy Microsoft Defender Antivirus antimalware platform update.
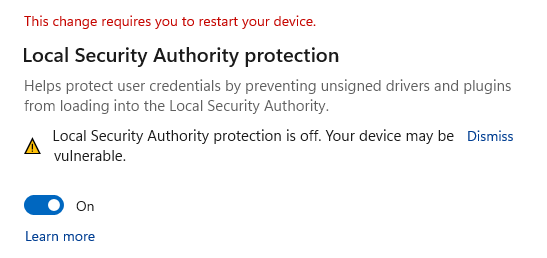
Redmond now says they have fixed the confusing alerts in a new Microsoft Defender Antivirus antimalware platform update.
“This issue was resolved in an update for Microsoft Defender Antivirus antimalware platform KB5007651 (Version 1.0.2303.27001). If you would like to install the update before it is installed automatically, you will need to check for updates,” reads an update to the Windows Health dashboard from Microsoft.
However, BleepingComputer has learned that this was fixed by removing the LSA Protection user interface altogether from the Windows Settings app, causing the warnings to no longer be displayed.
BleepingComputer also learned that LSA Protection is still supported, although the UI was removed from settings, and users can still manually enable/disable the security feature using the Registry or Group/MDM policies.
However, without the user interface, there is no way to check from the Windows settings anymore if LSA Protection is enabled.
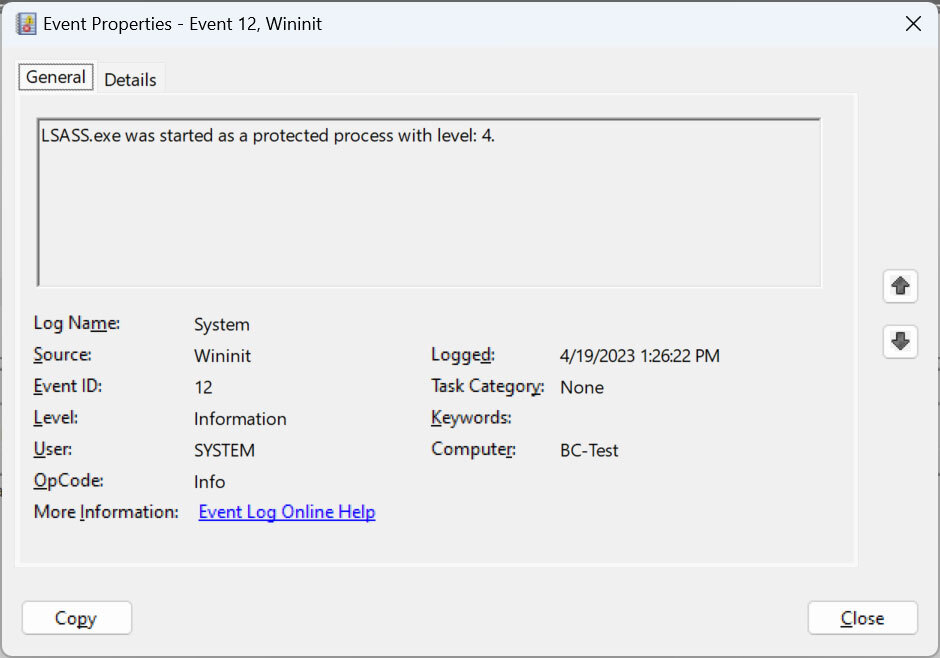
Despite this, users can still check if the feature is enabled using the Windows Event Viewer. If you find a Wininit event 12 saying that “LSASS.exe was started as a protected process with level:4,” it means the process is being isolated and protected by LSA Protection.
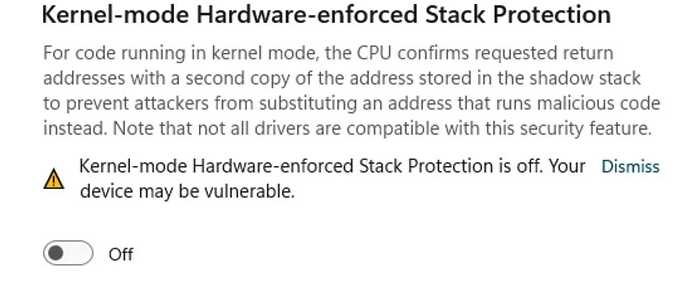
Kernel-mode Hardware-enforced Stack Protection warnings
As BleepingComputer reported last week after the LSA Protection UI was removed from the Windows Security > Device Security > Core Isolation settings page, users are now seeing similar alerts, this time warning them that their devices may be vulnerable because Kernel-mode Hardware-enforced Stack Protection (HSP) is off due to conflicting drivers.
Kernel-mode HSP protects against ROP (Return Oriented Programming) based control flow attacks that can lead to malicious code execution using modern CPU hardware features like Intel’s Control-flow Enforcement Technology (CET) or ARM’s Pointer Authentication Code (PAC).
Once this security feature is enabled, Windows ensures that no incompatible drivers are loaded; however, users report that the list of incompatible drivers is empty on affected systems.
Furthermore, some conflicting game anti-cheat drivers detected as incompatible will trigger Windows crashes or prevent games from launching when Kernel-mode HSP is enabled. Games impacted by this issue include PUBG, Valorant (Riot Vanguard), Bloodhunt, Destiny 2, Genshin Impact, Phantasy Star Online 2 (Game Guard), and Dayz.
Last month, Microsoft also announced that LSA Protection would be enabled default for Windows 11 Insiders in the Canary channel if their systems pass an incompatibility audit check (Microsoft is yet to provide details on the compatibility issues being audited).
