The NCSC’s VRS Journey
Since 2018, 844 hackers have submitted vulnerabilities to the NCSC’s VRS. The NCSC invited a selection of those hackers who have shown themselves to be exemplars of vulnerability disclosure to receive a limited edition Challenge Coin. The coins are a symbol of the NCSC’s gratitude and recognition for the hackers’ valuable work in helping protect the UK from cyber threats. The NCSC CTO, Ollie Whitehouse, and Cabinet Office Deputy Director for Cyber Policy and Capabilities, Michael Brunton-Spall, presented the coins and personally thanked the recipients.
The challenge coins have been designed to depict a person or element important in the history of British computing; Ada Lovelace, Alan Turing, Charles Babbage, and the Bombe. Read more about the coins in the NCSC’s blog.
Recognising Hackers as a VRS Best Practice
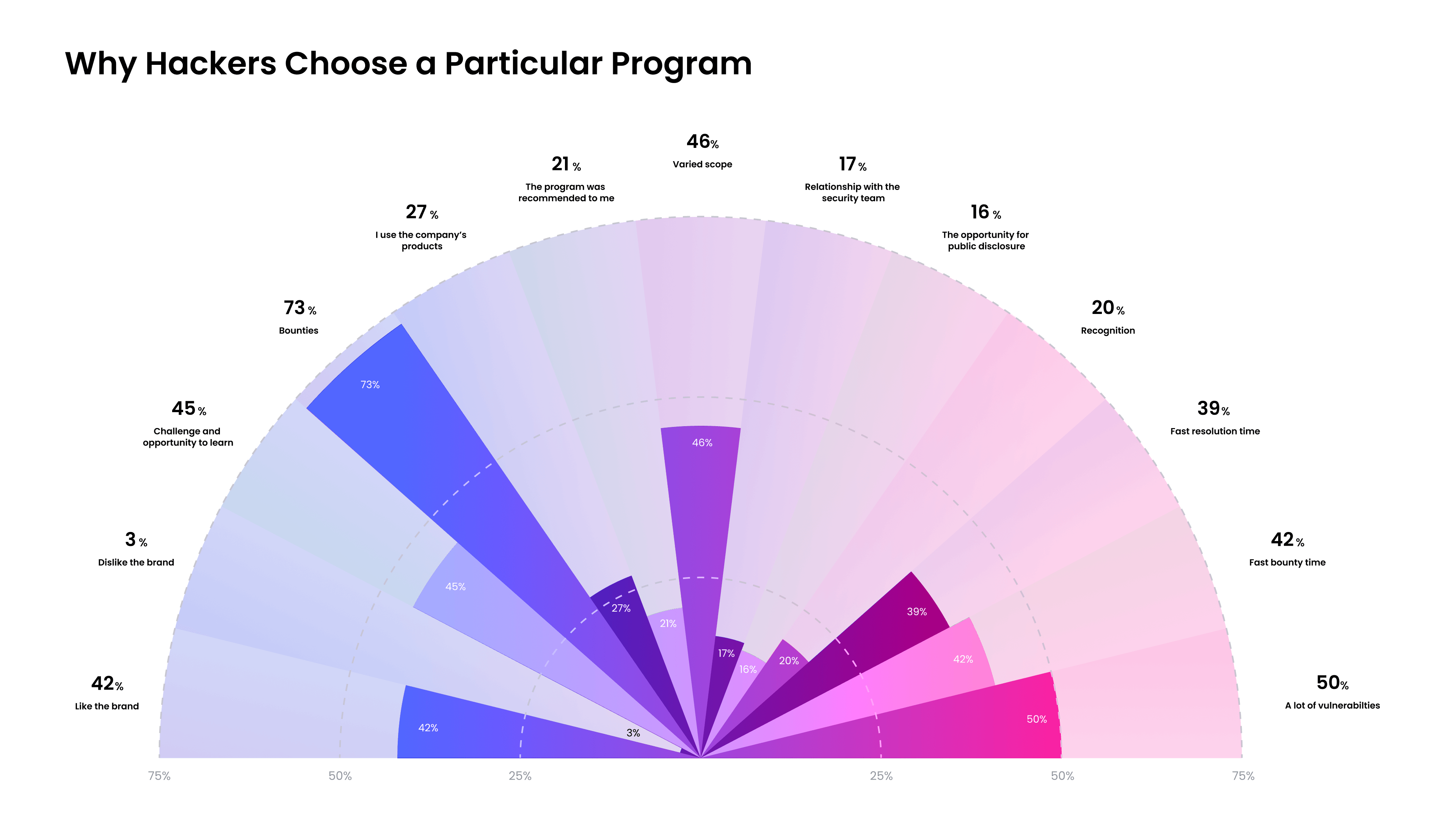
Hacker recognition is a key aspect of vulnerability disclosure best practice. HackerOne’s annual Hacker-Powered Security Report shows that in addition to monetary rewards, hackers pick programs based on recognition and the relationship they build with the customer team.
Three of the attending hackers had the opportunity to present their research during the event, which felt like an important moment in their work being recognised and legitimised.
Security researcher, Dejaun Barker, talks about his hacker journey to hacking the NCSC:
“I’ve been hacking since I was about 16, from attempting to phish my brothers to finding bug bounty platforms where hackers can assist in finding vulnerabilities without getting a knock at the door! This, partnered with my day job working with the public sector, led to me to the NCSC VRS. I would be doing an injustice if I didn’t help protect UK Government assets outside of work.
Ethical hackers and security researchers have an insane amount of skill, expertise, and knowledge to look for vulnerabilities and flaws in systems that the average user does not. If you solely rely on the everyday users of your systems and applications to report vulnerabilities, will they be skilled enough to identify critical weaknesses?
It’s an honour, and a huge accomplishment, to be invited to the NCSC HQ and bring all of the work I’ve done virtually into almost ‘fact’ from ‘fiction’. If the medal wasn’t a big enough of an achievement, presenting definitely was! Showcasing my findings, my hours of work, and dedication to like-minded individuals and industry experts was something I’ll never forget. I will forever be honoured and will continue my efforts to secure the UK Government.”

Security researcher and founder of Inquirix, Abi Waddell, speaks about why recognition is important to her:
“Security testing, like other similar audit and `problem-finding’ jobs, is largely thankless because people are not always keen to discover flaws in their systems. A simple `thank-you’ goes a long way – even more than monetary rewards – and this event showed this wider appreciation. Events like this contribute to reassuring other organisations that welcoming input from the security research community is to be encouraged. It can only be to their benefit to receive vulnerability reports from those who volunteer their time and expertise. Without this program, key vulnerabilities would still be found, but simply go unreported or not be reported via the proper channels.”
One of the world’s top ethical hackers has also spent time on the NCSC’s program, motivated to help protect his community. Sean Roesner discusses why he takes time out of hacking for bounties to look for bugs for the NCSC:
“When I saw that I could poke on GOV.UK I got really curious about what assets were out there on the internet and challenged myself to identify a vulnerability affecting a .gov.uk site. I have been able to discover some easily fixable bugs, such as not sanitising user input and creating custom XSS filters. I believe It’s important for governments to collaborate with ethical hackers because there is talent all over the world ready to help them secure their assets. By working with ethical hackers, the NCSC is able to “tap” into this community of hackers who can produce the results they want. Many hackers also feel proud to help secure their governments.”
For more information, read the NCSC’s write-up of the event.
