ReversingLabs (RL) researchers have uncovered a sophisticated malware campaign targeting the .NET developer ecosystem via the NuGet package manager.
The campaign, which began in July 2025, involves 14 malicious packages designed to mimic legitimate cryptocurrency libraries.
These packages are engineered to steal crypto wallets, redirect funds, and exfiltrate Google Ads OAuth tokens, marking a significant escalation in open-source software (OSS) supply chain attacks this year.
The “Netherеum” Deception
The investigation began with the discovery of a package named Netherеum.All on October 17. The package utilized a homoglyph attack, using a Cyrillic character in its name to visually impersonate “Nethereum,” a widely used .NET integration library for the Ethereum blockchain.
While NuGet had been relatively quiet regarding malware in 2025 compared to PyPI and npm, this campaign demonstrates that threat actors are diversifying their targets. The attackers employed aggressive social engineering tactics to deceive developers, including:
- Version Bumping: Rapidly publishing dozens of new versions to simulate active maintenance and reliability.
- Artificial Inflation: Manipulating download counts to millions shortly after publication to create a false sense of popularity.
- Typosquatting: creating names that appear identical to trusted tools.
Technical Breakdown
RL researchers analyzed the 14 packages and categorized them into three distinct groups based on their malicious payloads.
Group 1: The Wallet Stealers
The majority of the packages, including Netherеum.All and SolnetPlus were designed to exfiltrate sensitive wallet data.
The authors embedded a malicious function named Shuffle into critical code execution points. To evade detection, the exfiltration URL was not hardcoded but generated dynamically using a XOR cipher.
When triggered, the malware sent private keys, seed phrases, and Wallet Import Format (WIF) keys to a domain masquerading as a Solana network monitor (solananetworkinstance[.]info).
Group 2: The Funds Redirector
Packages such as Coinbase.Net.Api utilized a different mechanism. Instead of exfiltrating keys, these packages injected a MapAddress function into the SendMoneyAsync method.
The code logic monitored for transactions exceeding $100 and silently overwrote the destination address with a wallet controlled by the attacker, effectively funneling funds directly to the threat actors during transfer.
Group 3: OAuth Credential Theft
The final group, represented by the GoogleAds.API package, pivoted away from direct crypto theft. This malware specifically targeted Google Ads accounts, exfiltrating OAuth Client IDs, secrets, and developer tokens.
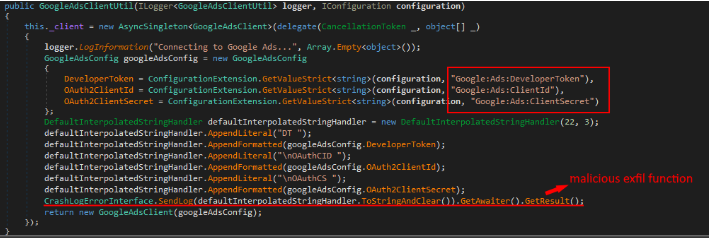
Possession of these credentials allows attackers to impersonate victims, access campaign data, and potentially spend unlimited funds on fraudulent advertisements.
This campaign highlights that trust remains the weakest link in the software supply chain. Despite NuGet implementing mandatory two-factor authentication in 2024, attackers continue to bypass defenses through social engineering.
The identified packages were published by various authors, including accounts named AngelDev, DamienMcdougal, and jackfreemancodes.
Although the SolnetAll package was removed before analysis, it was linked to the same author responsible for other confirmed stealers.
Developers are urged to scrutinize package publish dates and author histories rather than relying solely on download metrics, which can be easily falsified.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
