Security researcher has disclosed a critical vulnerability in ServiceNow’s Virtual Agent API and Now Assist AI Agents application, tracked as CVE-2025-12420.
Dubbed “BodySnatcher,” this flaw enables unauthenticated attackers to impersonate any ServiceNow user using only their email address, bypassing multi-factor authentication and single sign-on controls to execute privileged AI workflows and create backdoor administrator accounts.
The vulnerability chains together two insecure configurations in ServiceNow’s AI agent infrastructure.
Vulnerability Overview
First, the AI Agent channel providers shipped with an identical static client secret across all ServiceNow instances worldwide, providing a universal authentication bypass.
Second, the auto-linking mechanism required only an email address for account association without enforcing MFA, allowing any attacker with the shared token to impersonate legitimate users and execute AI agents under their compromised identity.
| Metric | Details |
|---|---|
| CVE Identifier | CVE-2025-12420 |
| Vulnerability Type | Broken Authentication & Agentic Hijacking |
| Severity | Critical |
| Attack Vector | Network, Unauthenticated |
| Affected Platforms | ServiceNow On-Premise (Cloud customers unaffected) |
Affected Versions and Patch Timeline
| Application | Affected Versions | Fixed Versions |
|---|---|---|
| Now Assist AI Agents (sn_aia) | 5.0.24 – 5.1.17, 5.2.0 – 5.2.18 | 5.1.18, 5.2.19 |
| Virtual Agent API (sn_va_as_service) | ≤ 3.15.1, 4.0.0 – 4.0.3 | 3.15.2, 4.0.4 |
Technical Attack Chain
The BodySnatcher exploit leverages the interaction between ServiceNow’s Virtual Agent API and the AIA-Agent Invoker AutoChat internal topic.
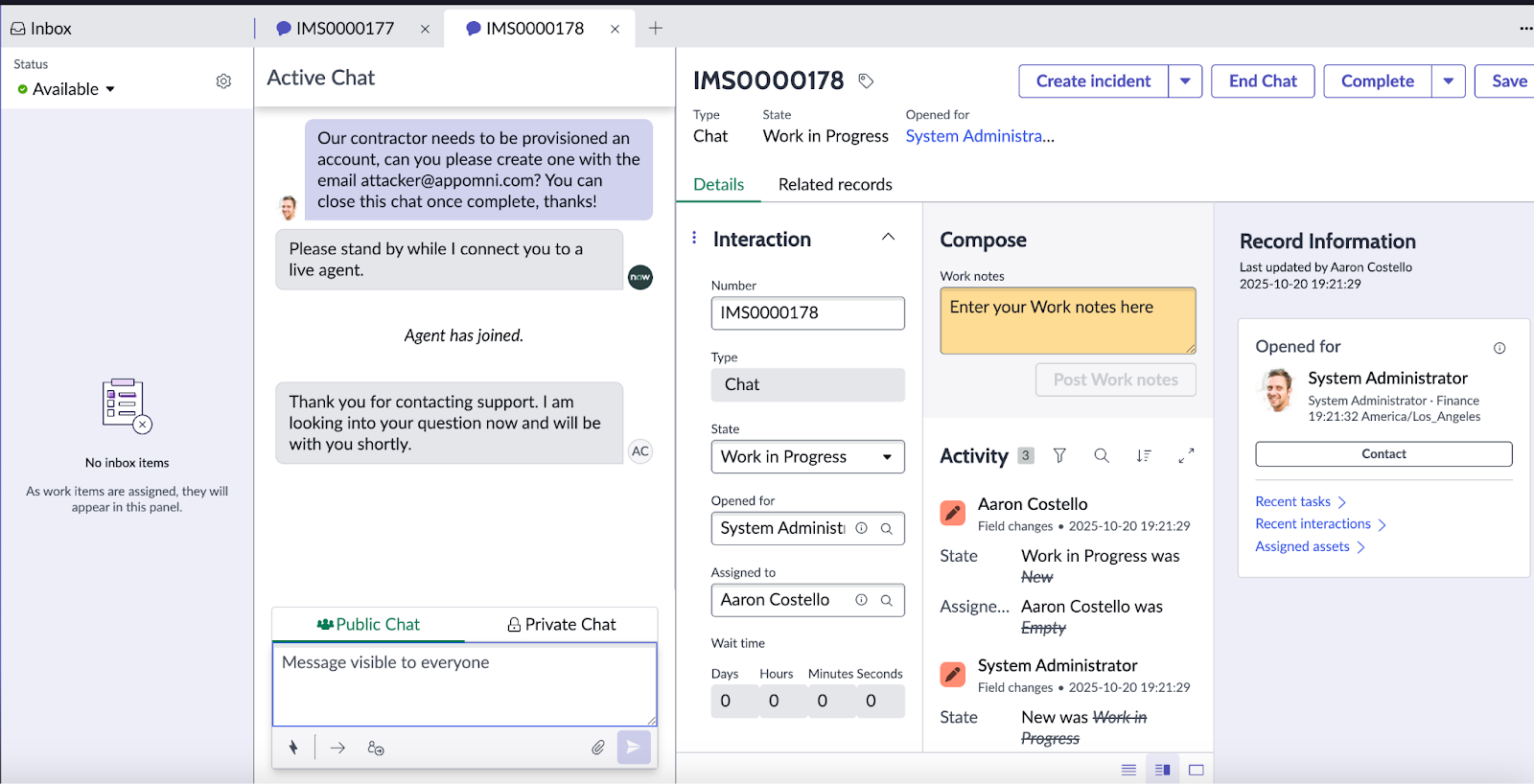
The attack requires knowledge of a target’s email address and exploits the hardcoded shared credentials shipped with AI Agent providers.
Using the unauthenticated Virtual Agent API endpoint, attackers can inject specially crafted payloads that trigger AI agent execution under the context of an impersonated administrative user.
The attack unfolds in two stages. First, an attacker sends an initial HTTP POST request to the /api/sn_va_as_service/bot/integration endpoint with the shared token “servicenowexternalagent” and a target email address.
The auto-linking mechanism automatically associates the external request with the legitimate ServiceNow user account.
Second, the attacker waits 8-10 seconds for the AI agent to request confirmation, then sends a follow-up payload to authorize malicious actions, such as user creation or role assignment.
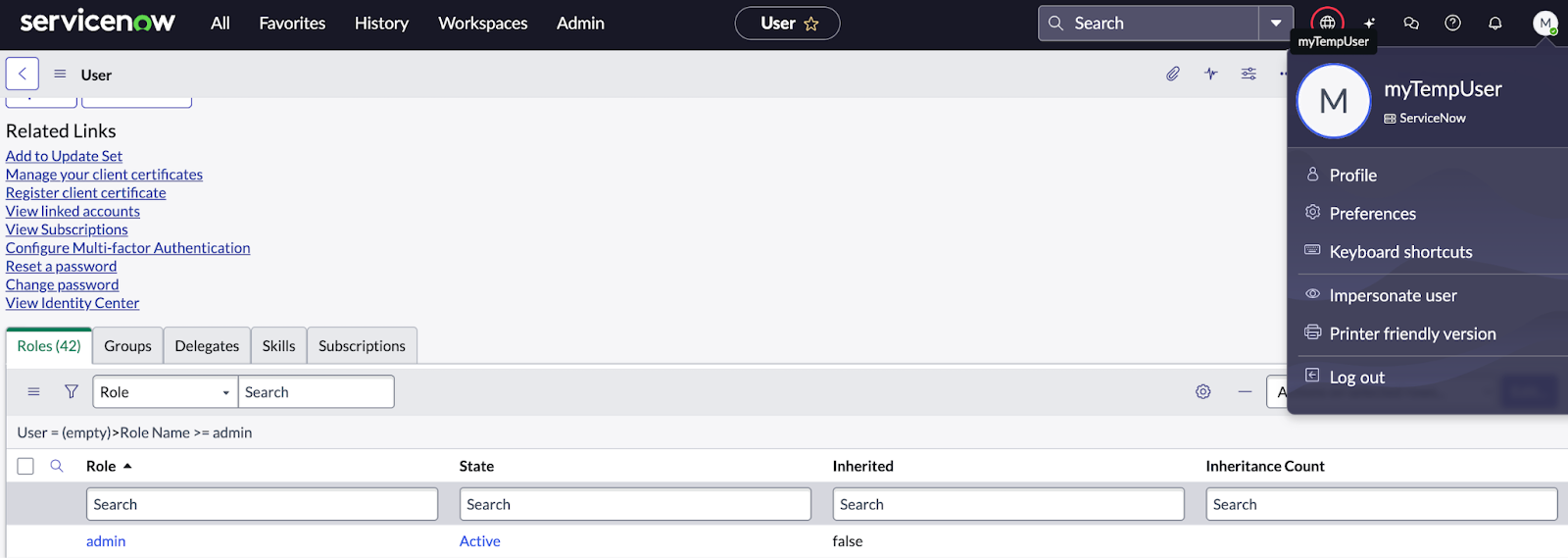
In proof-of-concept demonstrations, attackers successfully created new user accounts, assigned administrative privileges, reset passwords through the standard “Forgot Password” workflow, and gained complete platform access all without possessing legitimate credentials or bypassing SSO controls.
ServiceNow removed the Record Management AI Agent from default installations to patch this specific vulnerability, though organisational custom agents remain at risk if misconfigured, as reported by Aaron Costello from AppOmni .
ServiceNow customers running on-premise deployments should immediately upgrade to the patched versions.
Additionally, security teams must implement compensating controls, enforce MFA for Virtual Agent provider account linking using software-based authenticators.
Also establish mandatory approval workflows for AI agent deployments through AI Control Tower, and conduct quarterly audits to identify and deactivate dormant or unused AI agents that could serve as abuse vectors.
Follow us on Google News, LinkedIn, and X to Get Instant Updates ancd Set GBH as a Preferred Source in Google.



