A long-running phishing campaign is abusing Calendly-branded job invitations to compromise Google Workspace and Facebook Business accounts, with a particular focus on hijacking ad management platforms used by agencies and large brands.
The operation, uncovered by Push Security, combines Attacker‑in‑the‑Middle (AiTM) and Browser‑in‑the‑Browser (BITB) techniques with targeted controls to evade detection and maximize the value of stolen access.
Researchers first observed the campaign after a Push customer was hit with a highly targeted email attack aimed at their Google Workspace account, which served as the organization’s primary identity provider for Google apps and downstream single sign-on.
Despite the breadth of access a compromised Google Workspace account would provide, the attacker’s apparent priority was seizing control of accounts used to manage digital advertising.
The initial lure in this case was framed as a job opportunity with LVMH, sent from an address impersonating “Inside LVMH,” the group’s talent acquisition and training arm.
The email was well-written, tailored with victim-specific details, and appeared to come from a legitimate employee whose identity could be easily verified via open-source searches.
Phishing Pages Capture Google Workspace Logins
Push Security assesses it is plausible that generative AI and web-scraped data were used to craft these convincing exchanges.
Critically, the phishing link was only delivered after an initial back-and-forth, embedded as a Calendly-style link to “book time for a call.”
This multi-stage choreography is designed to slip past email security tools tuned to scan for embedded links and urgent calls to action.
Clicking the link sends victims to a fake Calendly landing page, complete with CAPTCHA, before presenting a “Continue with Google” option.
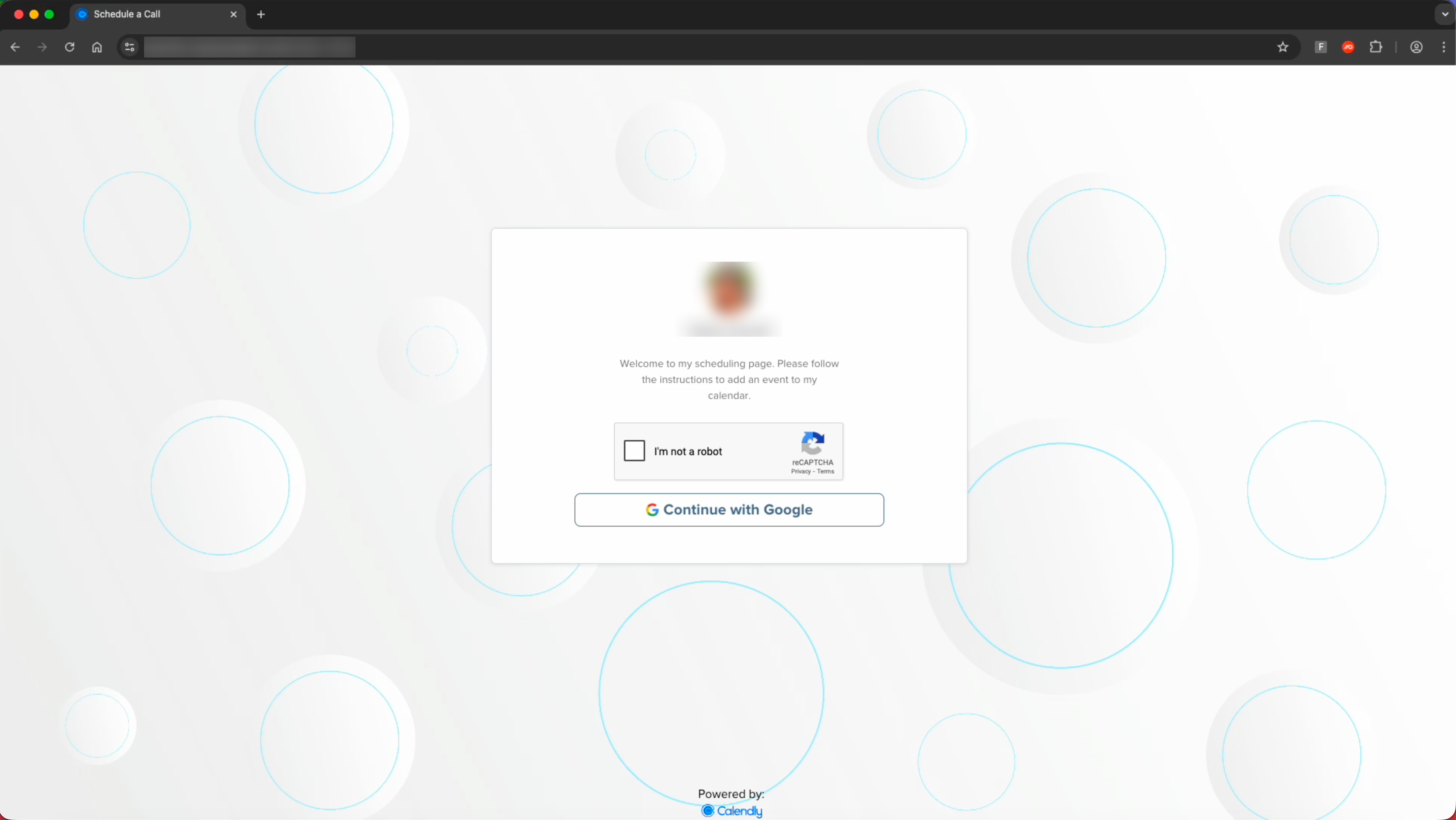
From there, the victim is redirected into an AiTM phishing page that proxies the real Google login flow while displaying Calendly branding, making it visually distinct from more common Google-themed phishing kits.
The page uses conditional loading and domain-based checks to ensure only the intended organization’s email domains can proceed.
Attempts to log in with other domains are blocked, preventing security analysts and automated scanners from easily observing the credential-harvesting logic.
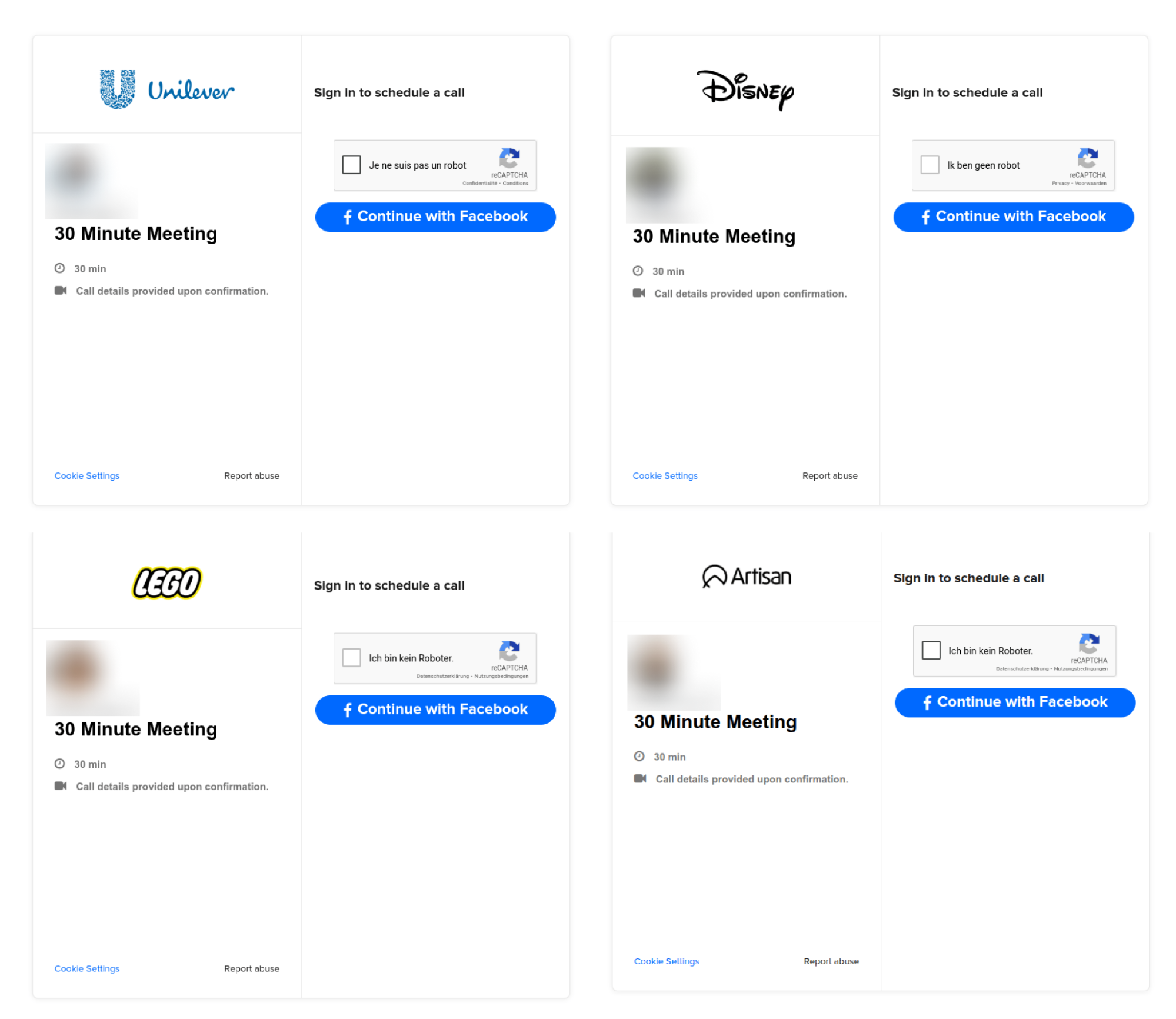
Push Security identified numerous related pages sharing the same Calendly-themed design, impersonating recruiters or HR staff at LVMH, Lego, Mastercard, Uber, and other major brands.
Spot and Stop These Imitation Invite Attacks
A second variant, dating back more than two years, targets Facebook Business accounts via similar themed pages, with at least 31 unique URLs being recycled over time to impersonate different companies.
A newer third variant blends both approaches, targeting Google and Facebook accounts via Calendly-styled pages that spawn a BITB pop-up.
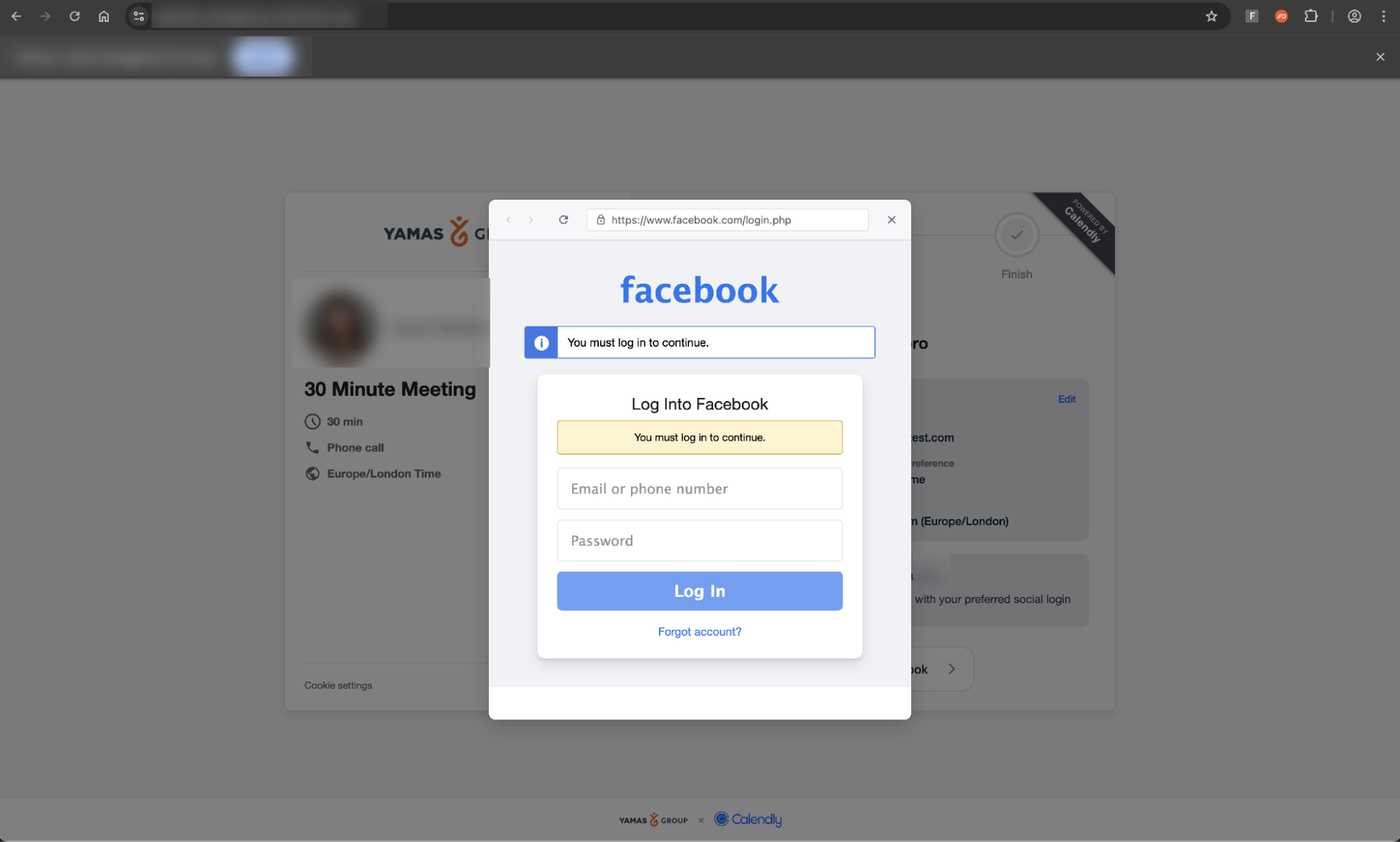
This technique masks the actual phishing server behind a fake, attacker-controlled URL bar inside the pop-up, further eroding users’ ability to distinguish real login prompts from malicious overlays.
Additional anti-analysis checks including IP-based blocking and triggers tied to accessing browser developer tools make these pages even harder for defenders to investigate.
The strategic focus on business ad management accounts aligns with broader shifts in the threat landscape.
Compromised Google Ads and Facebook Business accounts can be weaponized to run malvertising campaigns that distribute AiTM phishing, malware, and advanced “ClickFix” scams at scale, while sidestepping traditional email-based protections.
With ad platforms offering fine-grained targeting by geography, domain, and device type, attackers can blend wide-net credential harvesting with precise targeting of high-value organizations.
By starting with identity-based initial access via Google Workspace and then pivoting into ad infrastructure, the operators behind this Calendly-themed campaign are positioning themselves to both monetize and operationalize stolen access either directly, through malicious ad buys, or indirectly, by selling footholds to other criminal groups.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
