New research has uncovered a sophisticated phishing campaign that abuses DocuSign’s brand to deliver Vidar malware and infect Windows systems.
The operation uses a realistic phishing site, a fake signed installer, access-code checks, and timebased execution barriers to evade both users and automated analysis.
DocuSign-themed phishing setup
The attack starts with a targeted phishing email that pretends to come from DocuSign and urges the recipient to review a document.
The message links to a lookalike domain, docu[.]sign-platform[.]app, instead of the legitimate DocuSign site, increasing the chance that victims will trust the page and proceed with the download.
Once on the fraudulent portal, users are prompted to download DocuSign_PackageInstaller.exe, which is presented as a legitimate DocuSign package.
Fake signed installer and gated execution
The downloaded file is a singlefile .NET bundle signed with a valid codesigning certificate issued to a company in China, a choice likely intended to bypass reputation checks and lower suspicion on Windows systems.
Inside, the main logic is protected behind an access code gate: when run, the program verifies a code and signature and sends the provided code to a command and control server.
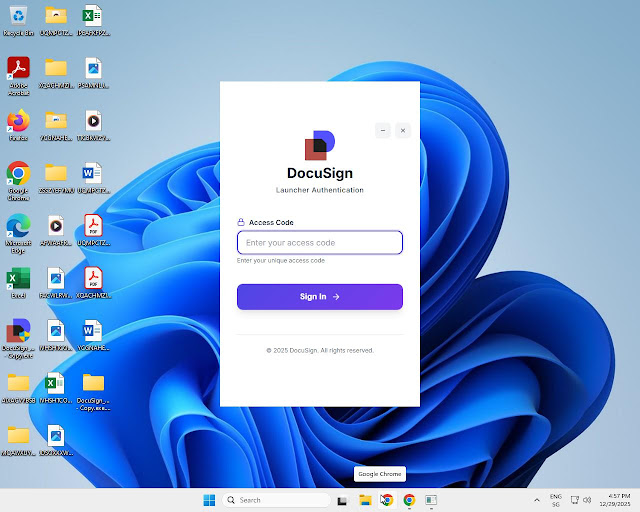
Only if the server validates the code does the malware continue and retrieve the next stage, effectively limiting automated sandboxes and casual analysis from reaching the payload.
Static analysis of the binary shows that it embeds a URL and second stage loader, allowing analysts to recover the next stage even without a working access code.
This approach lets defenders reconstruct the full delivery chain despite interactive barriers.
The secondstage payload is a native Windows binary that includes a time bomb check based on an online time source rather than the local system clock, defeating simple clock tampering on analysis systems.
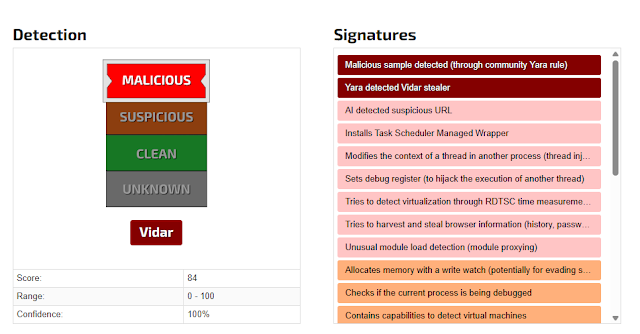
The sample also uses packing and layered obfuscation to frustrate reverse engineering and delay behavioral detection.
When executed under the right conditions, this packed second stage ultimately drops and runs Vidar, a wellknown informationstealing malware.
Vidar typically targets browser data, credentials, crypto wallets, and other sensitive information, giving attackers broad visibility into the victim’s digital life.
This DocuSignthemed scheme shows how threat actors now blend:
- Trusted brands and highly convincing phishing pages
- Legitimate codesigning certificates
- Accesscode–gated C2 logic
- Online time checks and packing
According to the JoeSecurity, these techniques make the chain resilient against automated sandboxes and quick triage, increasing the odds that Windows users are compromised before defenders can react.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
