A relatively new malware called Latrodectus is believed to be an evolution of the IcedID loader, seen in malicious email campaigns since November 2023.
The malware was spotted by researchers at Proofpoint and Team Cymru, who worked together to document its capabilities, which are still unstable and experimental.
IcedID is a malware family first identified in 2017 that was originally classified as a modular banking trojan designed to steal financial information from infected computers. Over time, it became more sophisticated, adding evasion and command execution capabilities.
In recent years, it has acted as a loader that can deliver other types of malware, including ransomware, onto infected systems.
Starting in 2022, several IcedID campaigns demonstrated diversified delivery tactics, but the primary distribution method remained malicious emails. In late 2022, new variants of the malware were used in attacks, which experimented with various evasion tricks and new attack sets.
In February 2024, one of the leaders behind the IcedID operation pleaded guilty in the United States, facing 40 years of imprisonment.
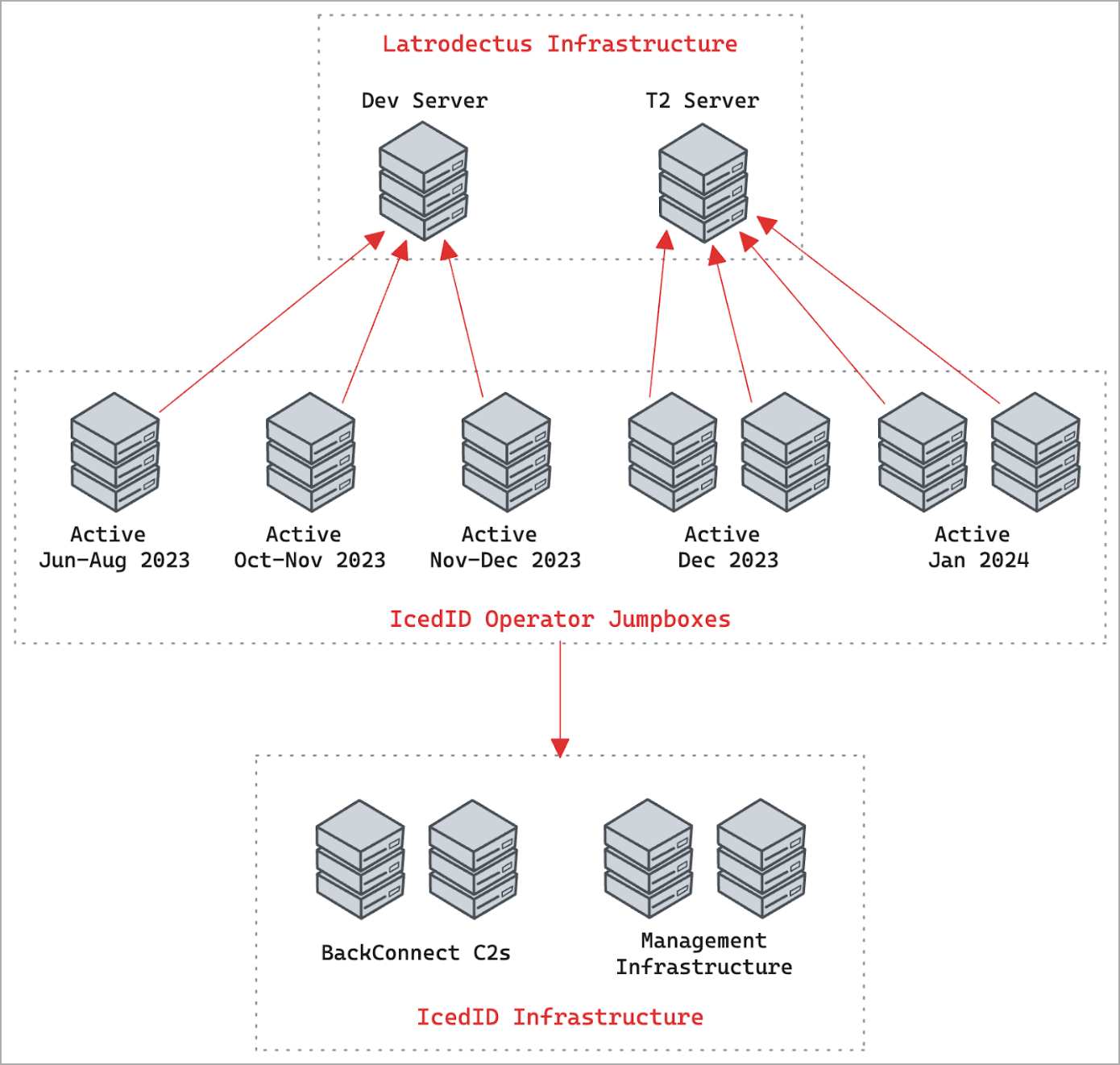
Researchers from Proofpoint and Team Cymru now believe that the developers of IcedID created Latrodectus after noting they shared infrastructure and operational overlaps.
Whether Latrodectus will ultimately replace IcedID is too soon to tell. However, the researchers say that initial access brokers (TA577 and TA578) who previously distributed IcedID have now begun to increasingly distribute Latrodectus in phishing campaigns.
New Latrodectus malware
Latrodectus was spotted in November 2023, used by threat actors tracked as TA577 and TA578, with a notable increase in observed deployments in February and March 2024.
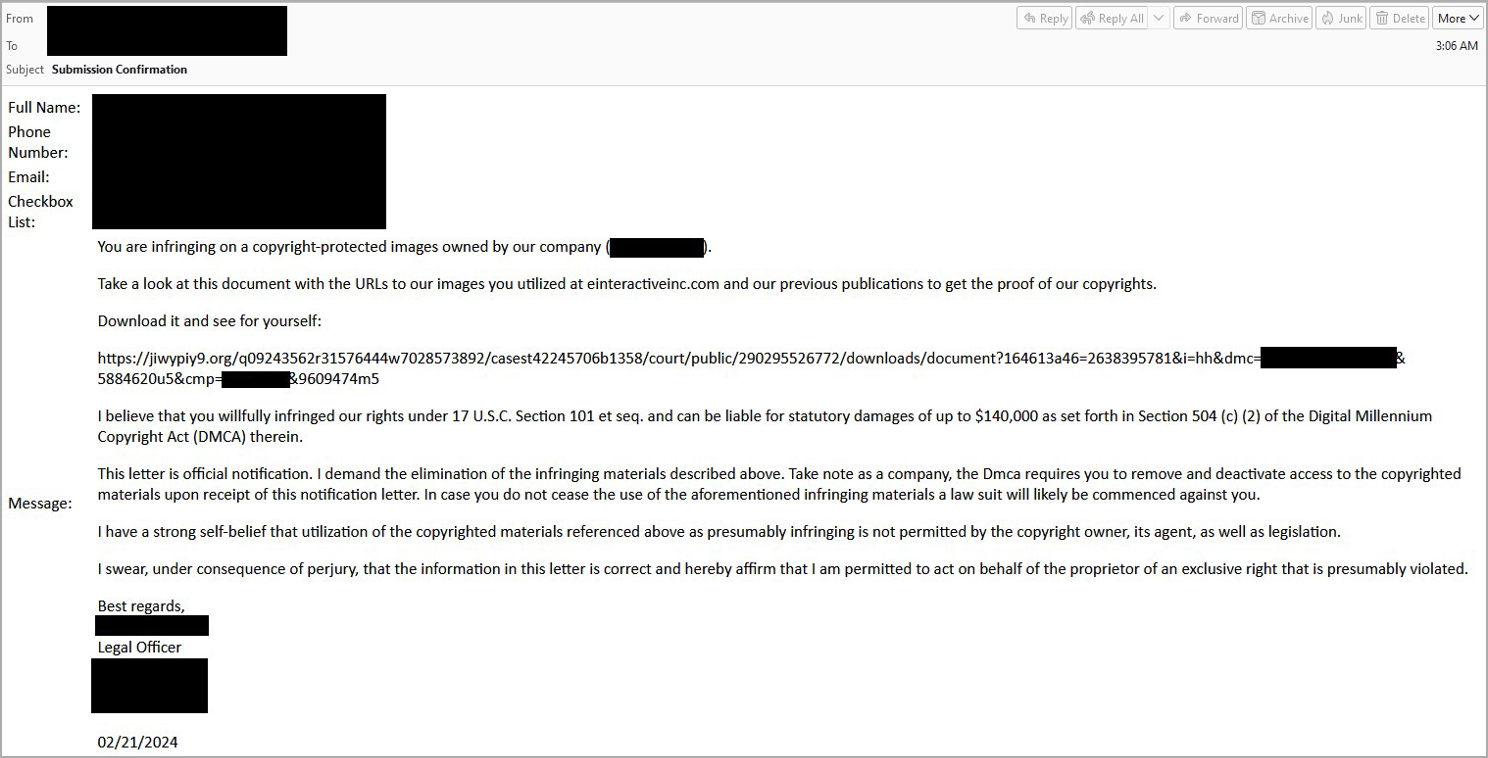
The threat actor initiates the attack by filling out online contact forms to send fake copyright infringement notices to the targeted organizations.
BleepingComputer previously reported on similar campaigns in the past, and for site owners unfamiliar with this phishing attack, they can be stressful to receive and may scare recipients into clicking on embedded links.
The link in the latest campaigns takes the victim to a Google Firebase URL that drops a JavaScript file. When executed, the JS file uses Windows installer (MSIEXEC) to run an MSI file from a WebDAV share, which contains the Latrodecturs DLL payload.
Unlike its predecessor, IcedID, Latrodectus performs various sandbox evasion checks before running on the device to avoid detection and analysis by security researchers.
The checks include:
- If Windows 10 or newer, have at least 75 running processes
- If earlier than Windows 10, have at least 50 running processes
- Ensure the 64-bit application is running on a 64-bit host
- Ensure the host has a valid MAC address
After the required environment and mutex checks, the malware initializes by sending a victim registration report to its operators.
Latrodectus is a downloader capable of retrieving further malicious payloads based on instructions received from a command and control (C2) server.
The commands Latrodectus supports are the following:
- Get the filenames of files on the desktop
- Get the list of running processes
- Send additional system information
- Execute an executable file
- Execute a DLL with a given export
- Pass a string to cmd and execute it
- Update the bot and trigger a restart
- Shutdown the running process
- Download “bp.dat” and execute it
- Set a flag to reset the timing of the communications
- Reset the counter variable used in communications
The malware’s infrastructure is separated into two distinct tiers that follow a dynamic operation approach regarding campaign involvement and lifespan, with most new C2 coming online towards the end of the week before the attacks.
Proofpoint concludes with a warning about Latrodectus, estimating a high probability of the malware being used in the future by multiple threat actors who previously distributed IcedID.
