Researchers have identified a new kind of theft where hackers break into a company’s AI and sell its power to others. According to an investigation by Pillar Security Research, a major campaign named Operation Bizarre Bazaar was active between December 2025 and January 2026.
During this two-month window, around 35,000 attack sessions were recorded, suggesting that hackers were hunting for exposed AI systems roughly 972 times every single day.
The team at Pillar Security Research traced the operation back to an individual using the alias Hecker, also known as Sakuya or LiveGamer101. It is worth noting that this is the first time anyone has documented a professional, commercial setup dedicated entirely to stealing AI access for resale.
Understanding LLMjacking
As we know it, most AI tools like chatbots run on Large Language Models (LLMs). These systems are incredibly expensive to maintain because of the massive amount of computer power they require. This is where LLMjacking comes in; it’s when a criminal sneaks into these systems to use that power for free. Think of it like someone secretly tapping into a neighbour’s water supply to run a commercial car wash. In this case, the hackers use this stolen access to:
- Run their own tasks without paying for server or electricity costs.
- Sell access to others at a massive discount via black-market shops.
- Access private conversation histories or sensitive company secrets.
Researchers found that the stolen access was being sold on a site called silver.inc, which acted as “The Unified LLM API Gateway” (like a supermarket for hackers), and offered access to over 30 different AI providers at 40% to 60% off the official price, even accepting PayPal and cryptocurrency.
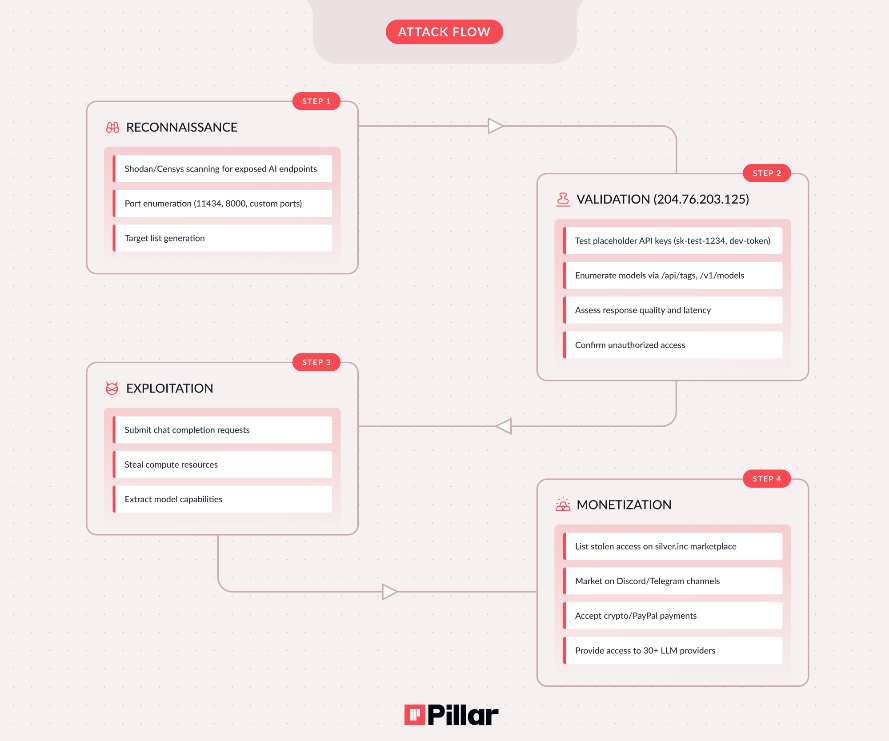
How Hackers Find Their Targets
In its research shared with Hackread.com, Pillar Security’s experts noted that these hackers aren’t always using high-tech tricks, as they sometimes just look for AI setups that have been left online without a password. Such as, many companies use a tool called Model Context Protocol (MCP) to link their AI to internal files. If this is left open, a hacker can walk straight into a company’s private database. Researchers identified that by late January, 60% of all attacks were specifically looking for these MCP gaps.
They further assessed that once an open system is found online, the hackers usually strike within hours. The threat remains active, and the attack infrastructure is still online. To stay safe, the report suggests that companies must “enable authentication on all LLM endpoints” and block the 204.76.203.0/24 internet range, which is directly linked to the silver.inc operation.
(Photo by Aerps on Unsplash)
