Researchers have uncovered a sophisticated phishing campaign originating in Russia that deploys the Phantom information-stealing malware via malicious ISO files.
The attack, dubbed “Operation MoneyMount-ISO,” targets finance and accounting departments explicitly using fake payment confirmation emails to trick victims into executing the payload.
The campaign primarily focuses on finance, accounting, treasury, and payment departments in Russia, with secondary targets including procurement, legal, HR/payroll teams, executive assistants, and Russian-speaking small and medium enterprises.
The attack poses significant risks, including credential theft, invoice and payment fraud, unauthorized fund transfers, and lateral movement into IT systems.
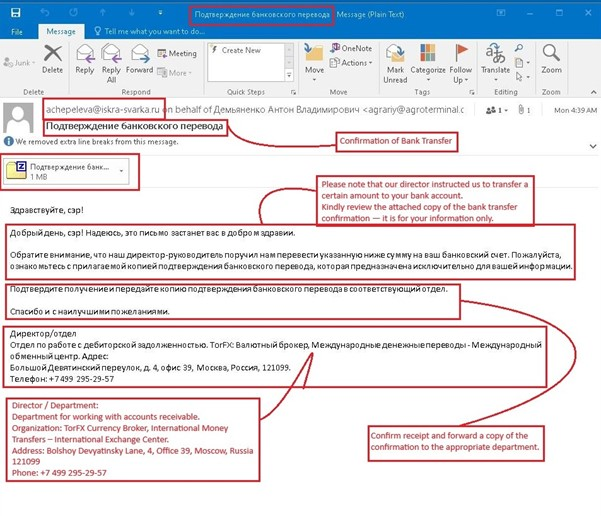
The infection begins with a Russian-language phishing email titled “Подтверждение банковского перевода” (Confirmation of Bank Transfer) sent from compromised domains.
The message impersonates TorFX Currency Broker and contains a ZIP attachment approximately 1 MB in size. When victims open the ZIP file, they find a malicious ISO file disguised as a legitimate bank transfer confirmation document.
Upon execution, the ISO file auto-mounts as a virtual CD drive, revealing an executable file that appears legitimate. The executable loads additional payloads into memory, including a DLL named CreativeAI.dll containing encrypted code.
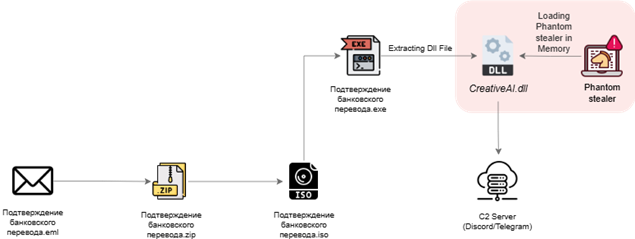
This DLL decrypts and injects the final version of the Phantom Stealer malware into the system.
Phantom Stealer Capabilities
Phantom Stealer is a comprehensive data theft tool with extensive capabilities. The malware features anti-analysis techniques that detect virtualized environments and security tools, automatically self-destructing if discovered.
According to Seqrite, it harvests cryptocurrency wallet data from both browser extensions and desktop applications, targeting dozens of known crypto wallets.
The stealer extracts Discord authentication tokens from browser databases and native Discord installations, validates them through Discord’s API, and collects user information, including usernames, emails, and Nitro subscription status.
It also deploys a continuous clipboard monitor that captures clipboard contents every second, logging timestamped entries for exfiltration.
Additional capabilities include a global keystroke logger using low-level Windows hooks, recovery of saved passwords and credit card data from Chromium-based browsers via SQLite database parsing, and targeted file collection based on predefined criteria.
Once stolen data is collected, Phantom Stealer packages it into a ZIP archive that includes system metadata, public IP addresses, and configuration toggles.
The malware employs multiple exfiltration channels, including Telegram bot APIs, Discord webhooks, and FTP servers with optional SSL support, ensuring attackers receive the stolen information through redundant communication methods.
Organizations should implement continuous filtering of containerized attachments, deploy memory-behavior monitoring solutions, and harden email security workflows for finance-facing departments to defend against these evolving threats.
IOCs
| 27bc3c4eed4e70ff5a438815b1694f83150c36d351ae1095c2811c962591e1bf | |
| 4b16604768565571f692d3fa84bda41ad8e244f95fbe6ab37b62291c5f9b3599 | Подтверждение банковского перевода.zip |
| 60994115258335b1e380002c7efcbb47682f644cb6a41585a1737b136e7544f9 | Подтверждение банковского перевода.iso |
| 78826700c53185405a0a3897848ca8474920804a01172f987a18bd3ef9a4fc77 | HvNC.exe |
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
