Security researchers have unveiled a critical series of vulnerabilities in the .NET Framework’s HTTP client proxy architecture, dubbed “SOAPwn,” that enables remote code execution across multiple enterprise-grade platforms.
Presented at Black Hat Europe 2025 by Piotr Bazydlo, the research reveals a fundamental design flaw in the framework’s handling of SOAP client proxies and WSDL imports.
The vulnerability stems from an invalid cast in the HttpWebClientProtocol class, which fails to correctly validate URLs passed to SOAP proxy methods.
This allows attackers to redirect requests to file system handlers instead of HTTP endpoints, enabling arbitrary file writes and code execution.
The flaw persists despite multiple reports to Microsoft, which declined to patch the underlying framework issue.
Vulnerable Products Identified
The research confirmed exploitation against several enterprise solutions.
Barracuda Service Center RMM (CVE-2025-34392) exposed a pre-authentication SOAP API method allowing unauthenticated attackers to invoke arbitrary WSDL methods and achieve RCE without credentials.
Ivanti Endpoint Manager (CVE-2025-13659) presents post-authentication exploitation risks for users with form-editing permissions.
Additional affected platforms include Umbraco 8 CMS, Microsoft PowerShell, and SQL Server Integration Services.
The exploitation leverages ServiceDescriptionImporter, a standard .NET Framework class used to generate SOAP client proxies from WSDL definitions.
According to WatchTowr, researchers demonstrated that malicious WSDL files can grant complete control over the generated proxy code, including method names, arguments, and target URLs.
By specifying file:// protocol URLs, attackers force SOAP requests to write directly to the filesystem, effectively creating arbitrary file write primitives.
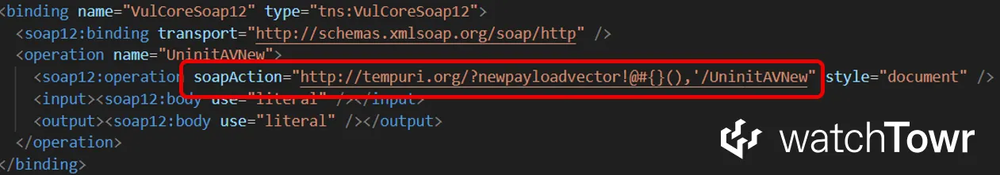
Attackers can deploy ASPX webshells or CSHTML payloads using multiple techniques, including XML serialization and namespace injection.
The absence of URL scheme validation in ServiceDescriptionImporter enables this exploitation at the framework level, affecting all dependent applications.
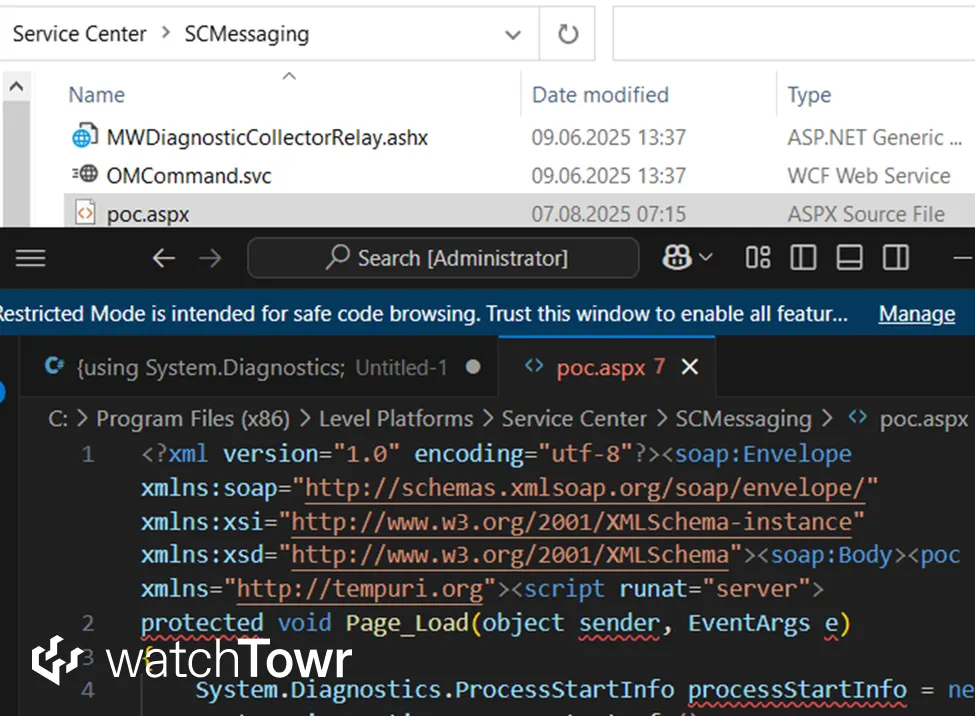
Microsoft declined to treat this as a framework vulnerability, attributing responsibility for input validation to application developers.
Barracuda released hotfix 2025.1.1, while Ivanti and other vendors deployed patches independently.
Security teams should prioritize updates for affected appliances and review WSDL-consuming applications for similar risks.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
