The new TicTacToe Dropper has been observed dropping additional threats onto Windows devices, including AgentTesla and LokiBot.
Fortinet’s FortiGuard Labs Threat Research Team has identified a group of malware droppers used in delivering final-stage payloads throughout 2023. The group is named ‘TicTacToe dropper’ due to a common Polish string, ‘Kolko_i_krzyzyk’, which translates to TicTacToe in English.
These droppers obfuscate final payloads during load and initial execution, including Leonem, AgentTesla, SnakeLogger, LokiBot, Remcos, RemLoader, Sabsik, Taskun, Androm and Upatre.
According to FortiGuard, the TicTacToe dropper has distributed multiple final-stage remote access tools (RATs) in the last 12 months and the final payloads feature several common characteristics, including multi-stage layered payloads, .NET executables/libraries, payload obfuscation using SmartAssembly software, DLL files nesting, and reflective loading.
In this campaign, malware executable is typically delivered via a .iso file, a technique often used to avoid detection by antivirus software and as a mark-of-the-web bypass technique. The executable contains multiple DLL file layers, which are extracted at runtime and loaded directly into memory.
TicTacToe Dropper Targets Windows
The medium severity level loader mainly affects Microsoft Windows platforms, potentially leading to compromised credentials and enabling further malicious activities, wrote Amey Gat and Mark Robson in FortiGuard’s blog post published on 14 February 2024.
Samples from early 2023 contained the strings TicTacToe, while later campaigns had different strings and different final-stage payloads. This suggests the tool is constantly developing and developers are trying to evade string-based analysis.
The first sample was a 32-bit executable called ‘ALco.exe’, which extracts and loads a.NET PE DLL file named ‘Hadval.dll’ or ‘stage2 payload’. The file is obfuscated with DeepSea version 4.1, causing unreadable function names and code flow obfuscation.
Use of de4dot tool
The de4dot tool, an open-source (GPLv3) .NET de-obfuscator and unpacker, utilized in the attack, successfully circumvents certain DeepSea obfuscation techniques, resulting in the de-obfuscation of a significant portion of the Hadval.dll file.
This file is responsible for extracting a gzip blob, which, upon decompression, unveils an additional 32-bit PE DLL file and another .NET library. The stage 3 payload, internally named ‘cruiser.dll’, is protected by SmartAssembly software.
The cruiser.dll file contained a class named ‘Munoz’ that creates a copy of the executable in the temp folder. The code from stage 3 extracts, loads, and executes the stage 4 payload from the bitmap object ‘dZAu’. Another DLL file, ‘Farinell2.dll’, is obfuscated with a custom obfuscator.
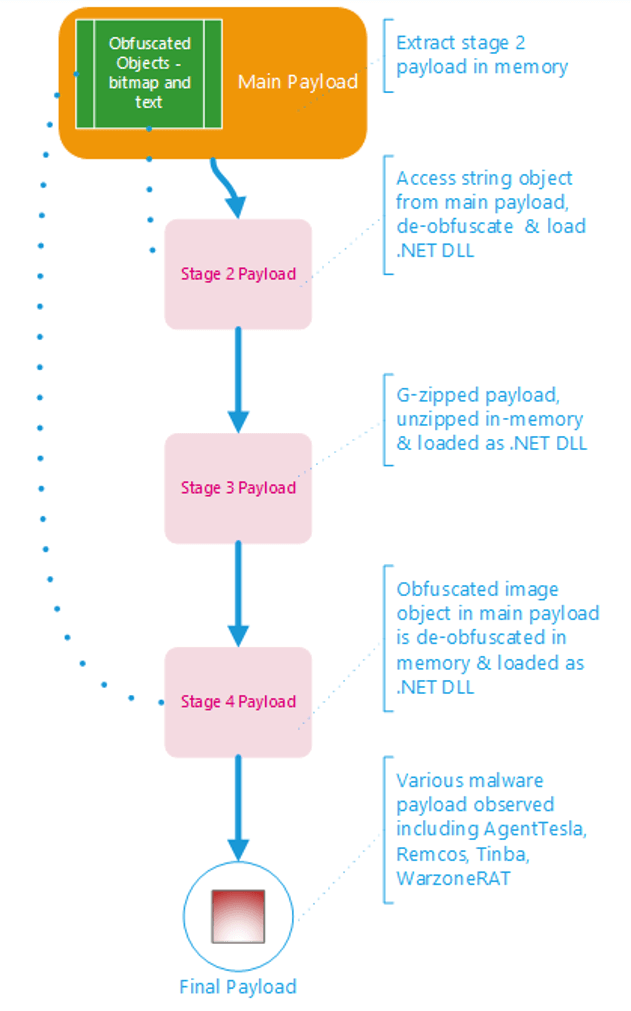
AgentTesla
A separate TicTacToe dropper sample was earlier analyzed, which dropped AgentTesla, a well-known RAT. This 32-bit.NET executable used an identical technique to load code stored in the resource element of the file.
The stage 2 payload had the internal name ‘Pendulum.dll’ and the stage 3 payload had the name ‘cruiser.dll.’ The stage 3 payload extracted the stage 4 payload from the bitmap object ‘faLa’ with the final payload being AgentTesla.
For mitigating the threat, researchers believe hash-based detections are effective for known campaigns. However, a behaviour-based endpoint security tool is required for new campaigns given the dynamic nature of this malware. EDR technology like FortiEDR can effectively detect anomalous behaviour.
RELATED TOPICS
- Konni RAT Exploiting Word Docs to Steal Data from Windows
- Crypto Stealing PyPI Malware Hits Windows and Linux Users
- New JaskaGO Malware Targets Mac and Windows for Crypto
- New Windows Infostealer ‘ExelaStealer’ Being Sold on Dark Web
- Fake Bitwarden Password Manager Website Drops Windows ZenRAT
