The open-source AI assistant OpenClaw experienced explosive growth, expanding from approximately 1,000 active instances to over 21,000 in just seven days.
Created by Austrian developer Peter Steinberger, the personal AI assistant integrates with email, calendars, smart-home systems, and food-delivery services, enabling it to perform actions far beyond those of traditional chatbots.
The project’s rapid evolution included multiple identity changes. It initially launched as Clawdbot, a lobster-themed reference to Anthropic’s Claude AI.
Following trademark concerns from Anthropic, the project was rebranded to Moltbot on January 27, 2026, and subsequently renamed OpenClaw by week’s end.
The ecosystem expanded further with Moltbook, a Reddit-like social platform where AI agents communicate autonomously.
However, the platform quickly exhibited dysfunction similar to human social networks, including toxic roleplay, anti-human rhetoric, and agent manipulation attempts.
Security Exposure Concerns
OpenClaw is designed to run locally on TCP port 18789, accessible through a browser interface.
The project documentation recommends using SSH tunnels for remote access rather than exposing the Internet directly. However, numerous operators deployed instances directly on the public Internet without these protective mechanisms.
Censys identified 21,639 publicly exposed OpenClaw instances using HTML title queries for both “Moltbot Control” and “clawdbot Control” pages.
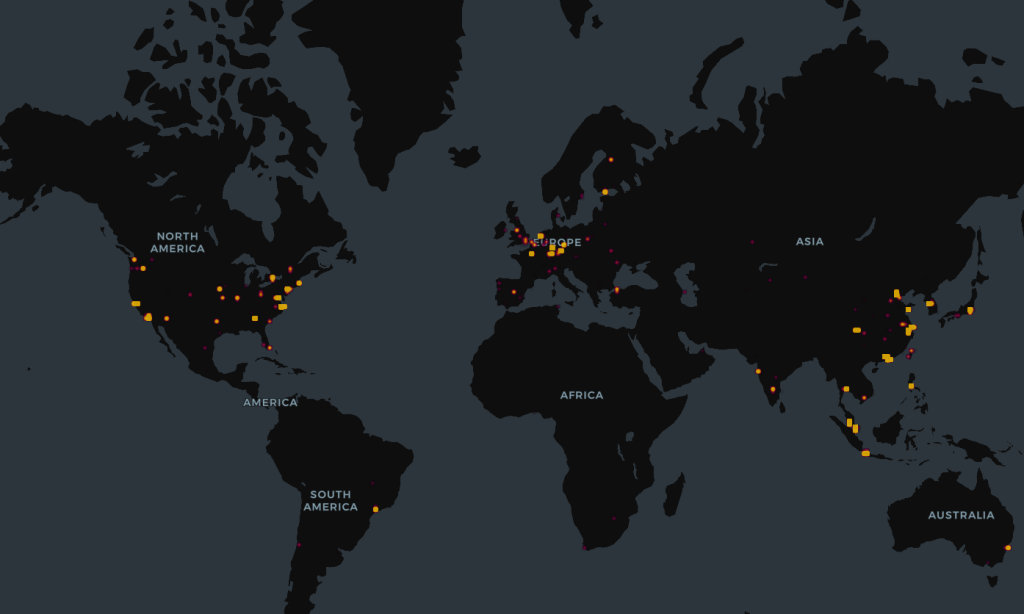
While most instances require authentication tokens for access, the sheer number of exposed deployments raises significant security concerns.
Geographic analysis reveals that the United States hosts the largest concentration of visible instances, followed by China and Singapore.
At least 30% of identified instances run on Alibaba Cloud infrastructure, though visibility bias may influence this distribution.
Many operators reportedly use Cloudflare Tunnels for remote access, reducing direct exposure, though exact figures remain unavailable.
The rapid deployment of OpenClaw instances without adequate security configuration demonstrates a critical vulnerability pattern.
Since these AI assistants access highly sensitive personal information, email credentials, calendar data, and smart-home controls, their Internet-facing exposure presents substantial privacy and security risks.
The concentration of instances across major cloud providers and multiple geographic regions underscores the scale of potential exposure.
Organizations and individual users deploying OpenClaw must prioritize careful configuration, implement proper access controls, and conduct comprehensive security reviews before enabling remote access.
This incident highlights the growing challenge of securing emerging AI systems deployed at unprecedented speed across the Internet, emphasizing the need for security awareness early in application lifecycle management.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.