Over 25,000 publicly accessible SonicWall SSLVPN devices are vulnerable to critical severity flaws, with 20,000 using a SonicOS/OSX firmware version that the vendor no longer supports.
These results come from an analysis conducted by cybersecurity firm Bishop Fox, which was motivated by a series of important vulnerabilities disclosed this year impacting SonicWall devices.
Vulnerabilities affecting SonicWall SSL VPN devices were recently exploited by ransomware groups, including Fog ransomware and Akira, as they are an attractive target for gaining initial access to corporate networks.
Massive attack surface
By leveraging internet scanning tools like Shodan and BinaryEdge and its proprietary fingerprinting techniques, Bishop Fox identified 430,363 publicly exposed SonicWall firewalls.
Public exposure means that the firewall’s management or SSL VPN interfaces are accessible from the internet, presenting an opportunity for attackers to probe for vulnerabilities, outdated/unpatched firmware, misconfigurations, and brute-force weak passwords.
“The management interface on a firewall should never be publicly exposed, as this presents an unnecessary risk,” explains BishopFox.
“The SSL VPN interface, although designed to provide access to external clients over the internet, should ideally be protected by source IP address restrictions.”
When looking into the firmware versions used on those devices, the researchers discovered that 6,633 use Series 4 and 5, both of which reached the end of life (EoL) years ago. Another 14,077 use no longer supported versions of the now partially supported Series 6.
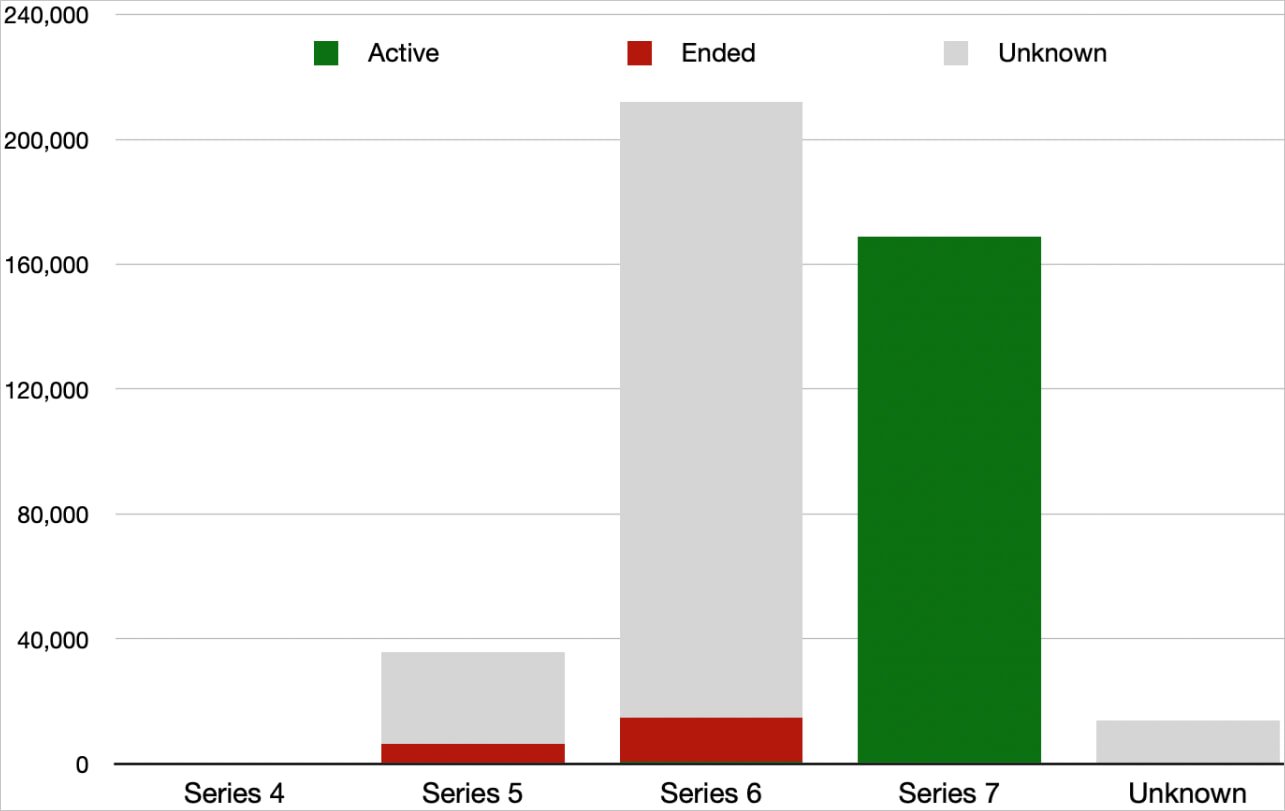
Source: BishopFox
This results in 20,710 devices running end-of-life firmware being vulnerable to many public exploits, but this figure is not representative of the accurate scale of the problem.
BishopFox also found 13,827 running unknown firmware versions, 197,099 running unsupported Series 6 firmware, but for which it was impossible to determine the exact version, and another 29,254 running an unknown version of Series 5 firmware.
When looking into the scan results using fingerprinting technology to identify the specific firmware versions and their protection against known vulnerabilities, the researchers determined that 25,485 are vulnerable to critical severity issues and 94,018 to high severity flaws.
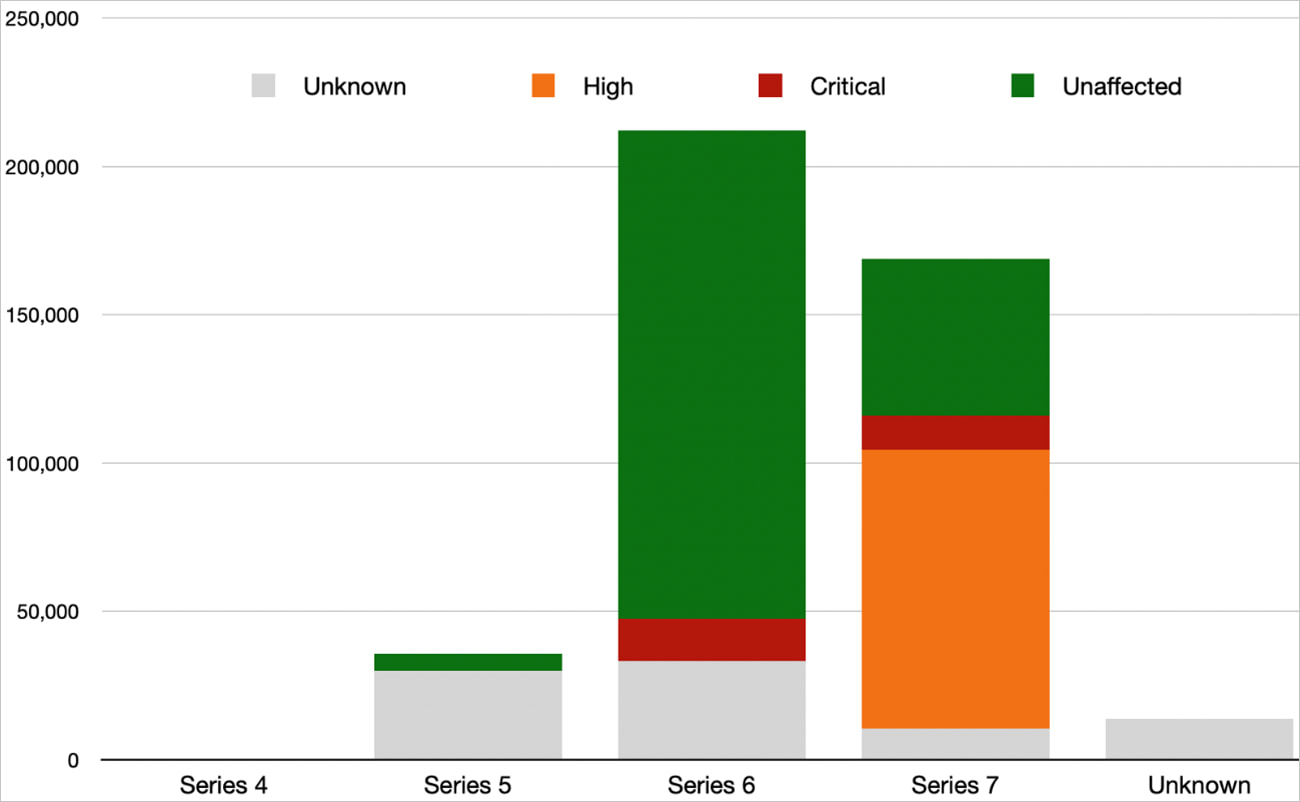
Source: BishopFox
Most of the devices confirmed to be vulnerable are on the Series 7 firmware but have not been updated to the latest version, which closes security gaps.
While the total of 119,503 vulnerable endpoints is an improvement over the 178,000 found vulnerable to DoS and RCE attacks in January 2024, it’s still indicative of slow patch adoption.
