Attackers are having a field day with software defects in security devices, according to a new report released Wednesday by…
The Reserve Bank of India (RBI) has issued a directive requiring all banking institutions in the country to migrate their…
A whistleblower at the National Labor Relations Board (NLRB) alleged last week that denizens of Elon Musk’s Department of Government…
Google contemplated deals with Android phone makers such as Samsung that would provide exclusivity for not only its search app,…
Source link
Lattica, an FHE-based platform enabling secure and private use of AI in the cloud, has emerged from stealth with $3.25…
The demand for highly performant networks has risen exponentially as organizations seek to empower employees with fast, anywhere access to…
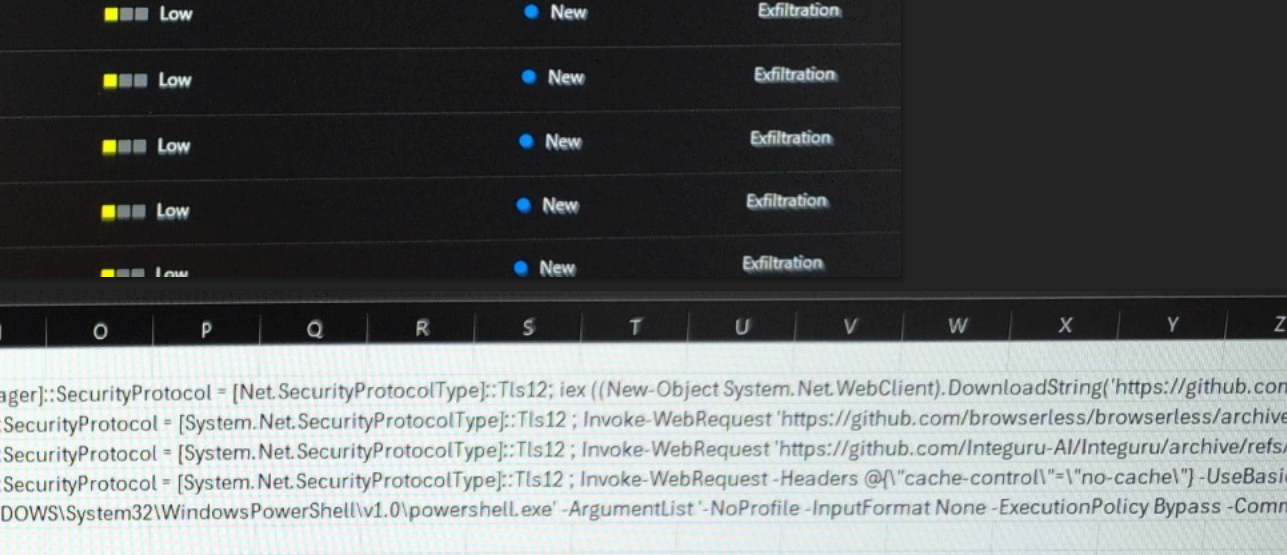
A significant vulnerability in the FireEye Endpoint Detection and Response (EDR) agent that could allow attackers to inject malicious code…
Developing an engineering project is a challenge by itself. In the practice, dealing with some product or service is very…
A new Android malware has been discovered hidden inside trojanized versions of the Alpine Quest mapping app, which is reportedly used…
Significant vulnerabilities in popular browser-based cryptocurrency wallets enable attackers to steal funds without any user interaction or approval. These critical…
Apr 23, 2025Ravie LakshmananMalware / Cryptocurrency Multiple threat activity clusters with ties to North Korea (aka Democratic People’s Republic of…