Lattica, an FHE-based platform enabling secure and private use of AI in the cloud, has emerged from stealth. The company…
Bitdefender GravityZone Proactive Hardening and Attack Surface Reduction (PHASR) is an endpoint security solution that dynamically tailors hardening for each…
The Iran-nexus threat actor known as UNC2428 has been observed delivering a backdoor known as MURKYTOUR as part of a…
Lattica, an FHE-based platform enabling secure and private use of AI in the cloud, has emerged from stealth with $3.25…
Tel Aviv, Israel, April 23rd, 2025, CyberNewsWire Lattica, an FHE-based platform enabling secure and private use of AI in the…
As ransomware, social engineering, and AI-driven deception reshape the threat landscape, cyberinsurance brokers are under pressure to deliver more than…
MITRE has released the latest version of its ATT&CK framework, which now also includes a new section (“matrix”) to cover…
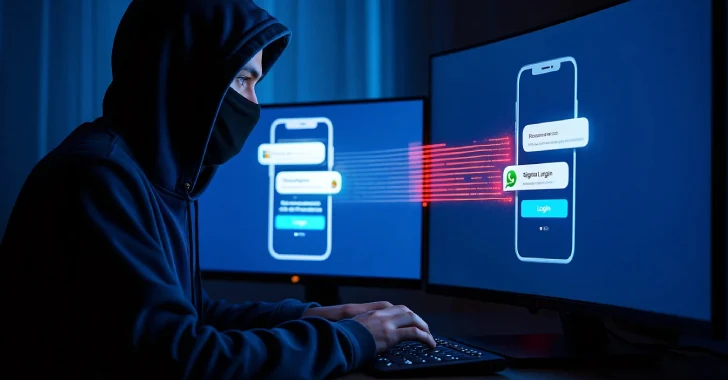
Apr 23, 2025Ravie LakshmananSpyware / Mobile Security Cybersecurity researchers have revealed that Russian military personnel are the target of a…
Researchers have disclosed a series of alarming vulnerabilities in popular browser-based cryptocurrency wallets that could allow attackers to silently drain…
AOA, DaVita, and Bell Ambulance hit by ransomware in 2025. Over 245K affected as hackers steal patient data, demand ransoms,…
The exploitation of vulnerabilities has seen another year of growth as an initial access vector for breaches, reaching 20%, according…
Multiple suspected Russia-linked threat actors are “aggressively” targeting individuals and organizations with ties to Ukraine and human rights with an…