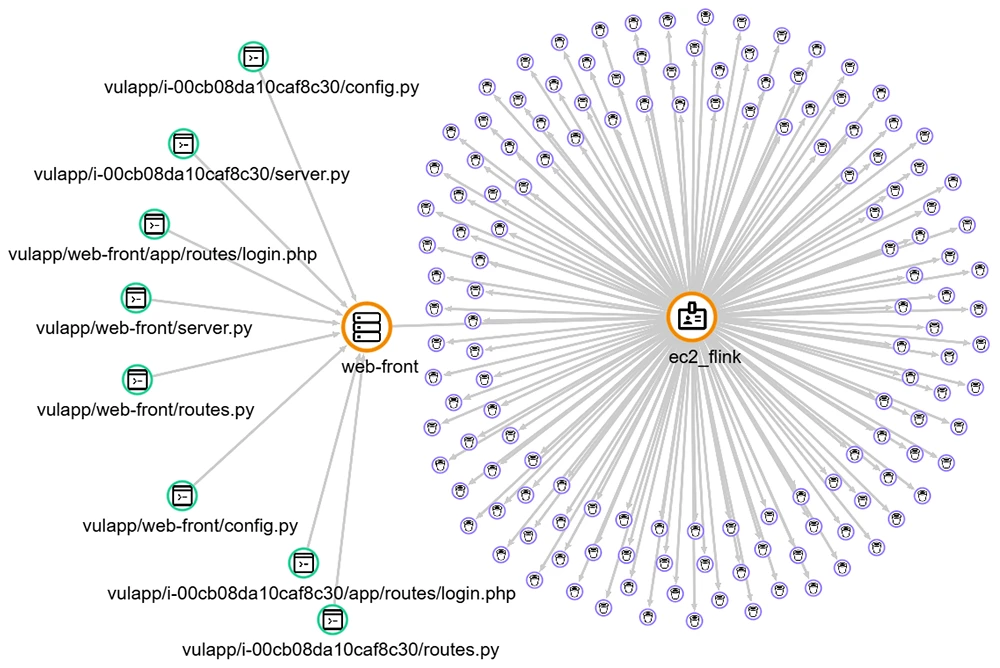
Skyhawk Security expanded its AI-powered Autonomous Purple Team to include custom cloud applications. For the first time, organizations can preemptively…
I often challenge people to describe why their lives have meaning. In most cases, the answers are deeply unsatisfying, both…
A critical privilege-escalation vulnerability in Google Cloud Platform (GCP), dubbed “ConfusedComposer,” could have allowed attackers to gain elevated permissions to…
In 2005, cell phones were banned for the first time during the conclave, the process by which the Catholic Church…
Research disclosed a now-patched high-severity vulnerability in Google Cloud Platform’s (GCP) Cloud Composer service, dubbed ConfusedComposer. It could have allowed attackers…
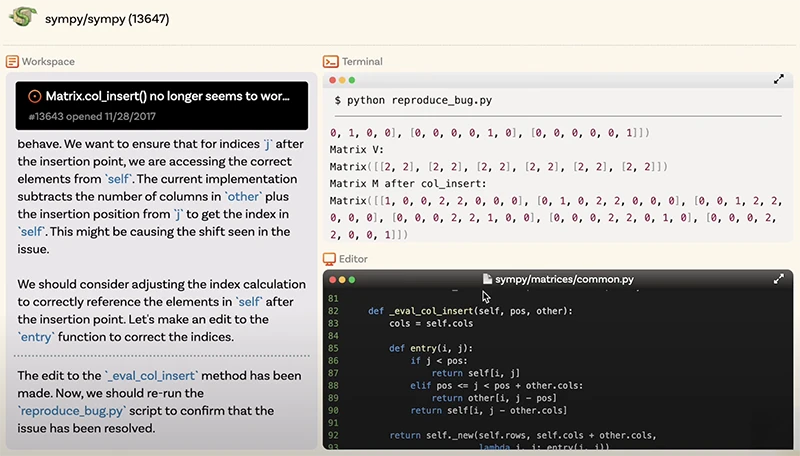
By connecting powerful language models like GPT-4o and Claude Sonnet 3.5 to real-world tools, the open-source tool SWE-agent allows them…
Apr 23, 2025Ravie LakshmananPrivacy / Artificial Intelligence Google on Tuesday revealed that it will no longer offer a standalone prompt…
A sophisticated attack technique dubbed “Cookie-Bite” enables cybercriminals to silently bypass multi-factor authentication (MFA) and maintain persistent access to cloud…
A recent security audit has uncovered critical vulnerabilities within Moodle, the widely used open-source learning management system (LMS). These vulnerabilities…
With billions of users, YouTube has become a tempting target for cybercriminals. They post malicious links in video descriptions and…
I don’t know a single truly creative mind who is a news junkie – not a writer, not a composer,…
Cybercriminals continued to shift to stealthier tactics, with lower-profile credential theft spiking, while ransomware attacks on enterprises declined, according to…