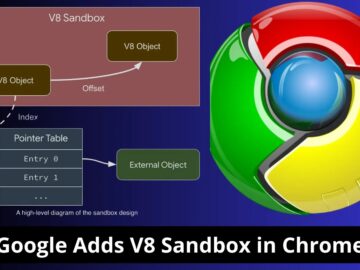
In a significant move to bolster the security of its widely-used V8 JavaScript engine, Google has unveiled the V8 Sandbox,…
Attackers are adept at identifying and exploiting the most cost-effective methods of compromise, highlighting the critical need for organizations to…
In the dynamic and ever-evolving landscape of cyber security defenses, enterprise-grade penetration testing is one of the most crucial practices…
In this Help Net Security interview, Charlotte Wylie, SVP and Deputy CSO at Okta, discusses the challenges of managing user…
The choice to operate on a private cloud or public cloud is far from binary, with financial services illion expecting…
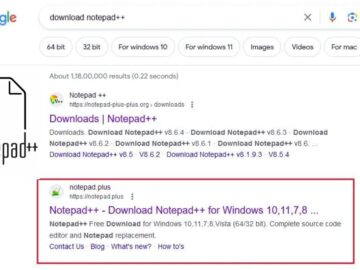
The developers of Notepad++, a widely used text and source code editor, have recently issued a call to action to…
More than a million phones could be impacted by 3G network shutdowns later this year, a telecommunications working group set…
Laptop and tablet accessories maker Targus disclosed that it suffered a cyberattack disrupting operations after a threat actor gained access…
ASX-listed motorcycle distributor MotorCycle Holdings has disclosed a data breach affecting customers of two of its brands. The company announced…
A common misconfiguration in popular web servers that support HTTP2 exposes them to low-effort denial-of-service attacks, according to security researcher…
Image: Midjourney Attackers are now actively targeting over 92,000 end-of-life D-Link Network Attached Storage (NAS) devices exposed online and unpatched…
Two key US lawmakers have struck a deal on draft bipartisan data privacy legislation that would restrict consumer data that…