A new malware campaign has been identified targeting Android users in India. This sophisticated attack distributes malicious APK packages to…
Cybersecurity researchers at vx-underground have reported that over 70 million records from an unspecified division of telecommunications giant AT&T have…
Quicmap is a fast, open-source QUIC service scanner that streamlines the process by eliminating multiple tool requirements. It effectively identifies…
Mar 18, 2024NewsroomCyber Warfare / Malware The Russia-linked threat actor known as APT28 has been linked to multiple ongoing phishing…
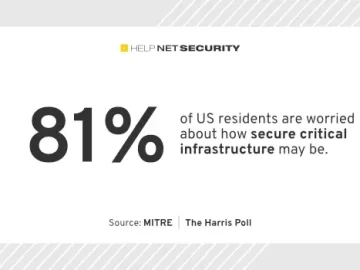
With temporary failures of critical infrastructure on the rise in the recent years, 81% of US residents are worried about…
DarkGPT, your next-level OSINT (Open Source Intelligence) assistant. In this digital era, the ability to sift through vast amounts of…
AT&T says a massive trove of data impacting 71 million people did not originate from its systems after a hacker…
Telstra and Optus could be delayed in shutting down their 3G networks over concerns that the closure could cut off…
Australian broadcaster SBS has detailed the benefits of a two-and-a-half-year content management system (CMS) transformation, combined with its use of…
Queensland Rail is in the process of replacing its chief information and digital officer (CIDO) following the departure of Boon…
The 2024 Cybersecurity Risk Report Provides CISOs Insights into the Likelihood and Financial Impact of Top Cyber Risks. By Luke…
Illuminating the individual beyond the black and white By Darrin Straff, Senior Staffing Consultant, NinjaJobs A Deeper Dive In my…