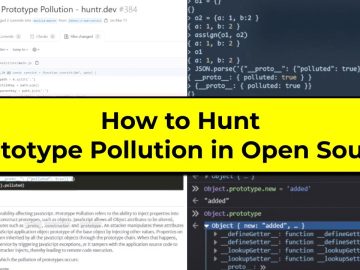
How to Hunt for Prototype Pollution Vulnerabilities in Open Source Bug Bounty | #methodology Source link
#NahamCon2022EU: Managing a Bug Bounty Program From a Hacker’s Perspective by @0xlupin Source link
Hack the Box: How does linux work? Source link
A new Emotet phishing campaign is targeting U.S. taxpayers by impersonating W-9 tax forms allegedly sent by the Internal Revenue…
The primary targets of this phishing campaign are located in the Ukrainian regions of Crimea, Donetsk, and Lugansk, which were…
Stream 00 : How to Bypass WAF for your XSS ! (OSINT Bonus) 🔥 Source link
Assuming democracy remains intact in the years to come, Levitsky thinks the GOP will have to eventually moderate its stance…
Velocity Exploit on Paper? Source link
For every one of these companies, however, I saw just as many (if not more) that employed crypto while trying…
My blog runs on Ghost. For some time it has a members feature. Last week I decided to enable it…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: These 15 European startups are…
Cyble Research and Intelligence Labs (CRIL) detected a newfound Malware-as-a-Service (MaaS) “Cinoshi” that allows criminals to launch cyberattacks without technical…