A sophisticated JScript-based command-and-control framework, PeckBirdy, since 2023, exploiting living-off-the-land binaries (LOLBins) to deliver modular backdoors across diverse execution environments.
The framework has been observed in two coordinated campaigns, SHADOW-VOID-044 and SHADOW-EARTH-045, targeting Chinese gambling industries, Asian government entities, and private organizations with advanced malware, including HOLODONUT and MKDOOR backdoors.
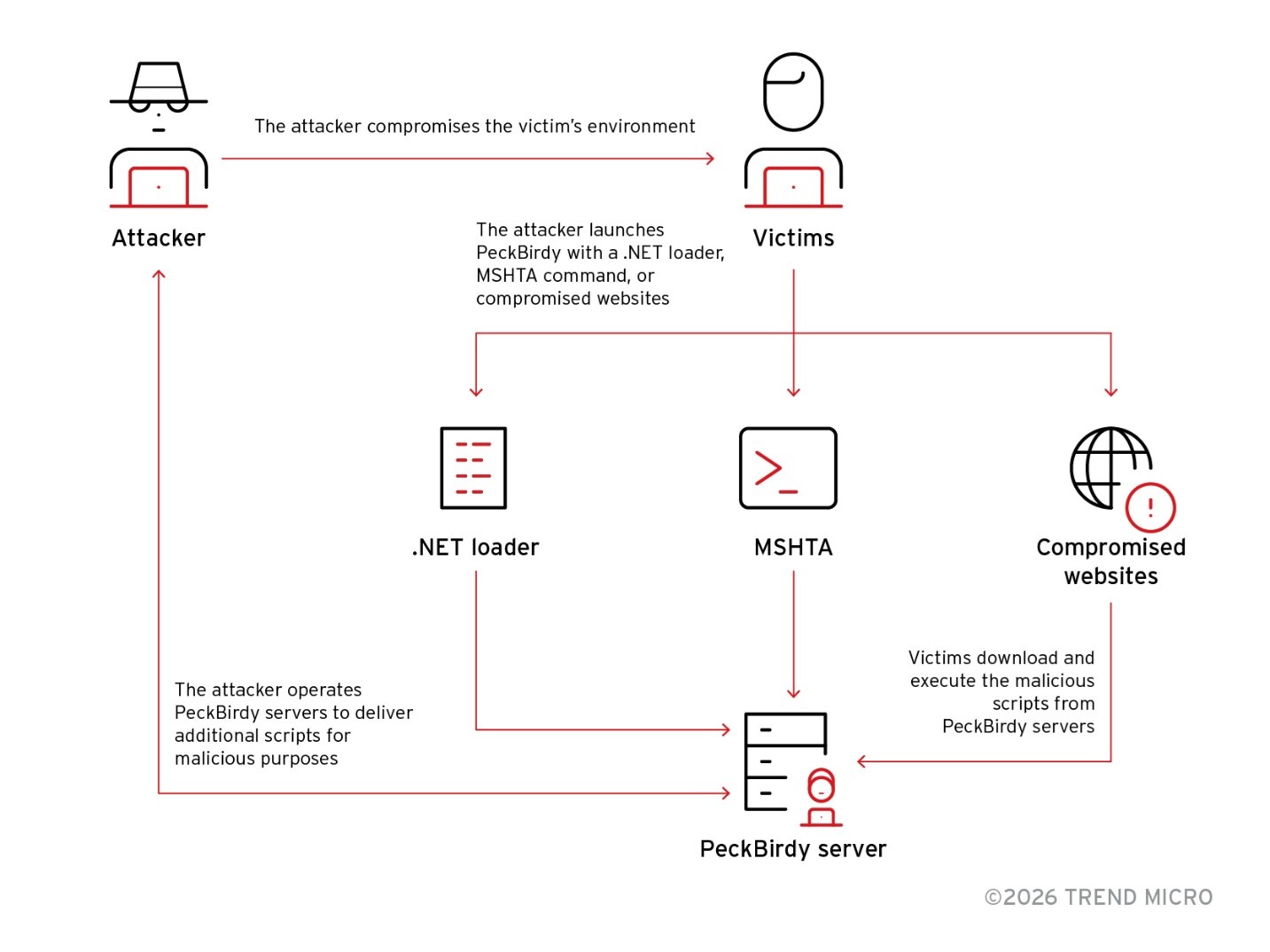
PeckBirdy distinguishes itself through its ability to execute across multiple environments, including browsers, MSHTA, WScript, Classic ASP, Node.js, and .NET ScriptControl.
This cross-platform capability enables threat actors to deploy the framework at various stages of the attack chain, from initial compromise through watering-hole servers to lateral movement and persistent backdoor operations.
The framework implements JScript (ECMAScript 3) to ensure compatibility with legacy systems while supporting modern environments.
Upon execution, PeckBirdy identifies the host environment by detecting unique objects such as the window object in browsers or the process object in Node.js environments.
This environmental awareness allows the framework to adapt its communication protocols and capabilities dynamically.
PeckBirdy supports multiple communication methods, prioritizing WebSocket for modern environments while falling back to Flash ActiveX TCP sockets or Comet/LocalComet protocols based on HTTP and AJAX for broader compatibility.
All communications are encrypted using AES with Base64 encoding, where the encryption key corresponds to a predefined 32-character ATTACK_ID value embedded in the configuration.
Coordinated Campaign Activity
SHADOW-VOID-044, first identified in 2023, compromised Chinese gambling websites through script injection, redirecting victims to fake Google Chrome update pages that delivered malicious backdoors.
Infrastructure analysis revealed connections to UNC3569, a known threat group targeting the gambling sector, with moderate-to-high confidence attribution.
SHADOW-EARTH-045, observed in July 2024, targeted Asian government entities and private organizations through injected login pages for credential harvesting.
The campaign leveraged CVE-2020-16040, a Chrome vulnerability, alongside social engineering techniques to deceive users into executing malware.
In one incident affecting a Philippine educational institution, attackers executed MSHTA commands connecting to compromised GitHub domains to launch PeckBirdy on an Internet Information Services server.
This campaign demonstrates potential links to Earth Baxia, though attribution remains low confidence.
HOLODONUT represents a .NET-based modular backdoor deployed through a custom downloader tracked as NEXLOAD.
The backdoor employs defense evasion techniques including AMSI and ETW event disabling, alongside Donut, an open-source tool for stealthy .NET assembly execution in process memory.
HOLODONUT supports plugin handlers that enable threat actors to dynamically load, execute, and unload .NET assemblies based on operational requirements.
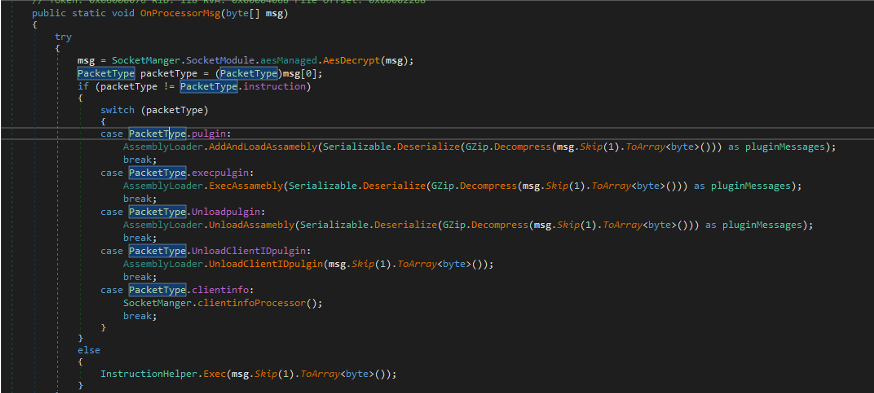
MKDOOR operates as a two-module backdoor system consisting of a downloader and backdoor component.
The downloader bypasses Microsoft Defender by adding exclusion rules and disguises network communications as legitimate Microsoft support traffic.
Command-and-control URLs mimic Windows activation pages to evade detection. The backdoor module supports commands for installing, uninstalling, executing, and managing additional modules received from C&C infrastructure.
Investigation of SHADOW-VOID-044 infrastructure uncovered the GRAYRABBIT backdoor on server 47.238.219.111, previously associated with UNC3569.
The campaign also utilized stolen code-signing certificates from a South Korean gaming company to sign Cobalt Strike payloads, certificates previously observed in BIOPASS RAT campaigns linked to Earth Lusca.
HOLODONUT samples connected to the same C&C server (mkdmcdn.com) used by TheWizard APT group, which also deployed DarkNimbus backdoor developed by Earth Minotaur.
| CVE ID | Vulnerability Type | Affected Software | CVSS Score | Exploitation Status |
|---|---|---|---|---|
| CVE-2020-16040 | Insufficient Data Validation | Google Chrome | 8.8 (High) | Actively Exploited |
Mitigations
Trend Micro Vision One detects and blocks indicators of compromise associated with PeckBirdy campaigns, providing threat hunting queries and intelligence reports.
Organizations should monitor for suspicious JScript execution via LOLBins, implement application allowlisting, scrutinize unsigned or suspiciously signed executables, and deploy network monitoring for encrypted communications to anomalous domains.
Detection of dynamically generated JavaScript frameworks remains challenging due to runtime code injection and minimal file artifacts, requiring behavioral analytics and memory-based detection capabilities.
The sophistication of PeckBirdy demonstrates the evolving threat landscape where APT actors leverage cross-platform frameworks and LOLBins to bypass traditional security controls while maintaining operational flexibility across diverse target environments.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




