An ongoing wave of phishing campaigns exploiting fake meeting invites from popular video conferencing platforms, including Zoom, Microsoft Teams, and Google Meet.
The attacks use social engineering to lure corporate users into downloading malicious “software updates,” which are, in reality, digitally signed remote monitoring and management (RMM) tools that grant attackers full remote access to victims’ systems.
These phishing operations rely on trusted collaboration platforms that have become indispensable in hybrid and remote work environments.
The attackers impersonate corporate communication channels by distributing convincing email invites that mimic legitimate meeting notifications.
Recipients are prompted to join a meeting or verify an invite through deceptive links hosted on typo-squatted domains such as zoom-meet.us or teams-updates.net, which closely resemble legitimate corporate services.
Upon clicking the fake link, victims are redirected to a highly convincing phishing page resembling the authentic login or meeting screen of platforms like Google Meet, Microsoft Teams, or Zoom.
To increase credibility, the phishing pages closely mimic legitimate pages, often displaying lists of participants who have “joined” the call.
To reinforce legitimacy, these pages may display simulated participant lists and active meeting interfaces, creating a sense of urgency to “join immediately.”
Netskope researchers observed that these interactive decoys encourage victims to act quickly without verifying the authenticity of the page.
The Hook: The “Mandatory Update” Trap
As users attempt to join the fake meeting, they are prompted with a warning that their conferencing application is out of date or incompatible.
A pop-up instructs them to download and install a “critical update” before joining. This fake update is the attack vector an executable masquerading as a legitimate software patch.
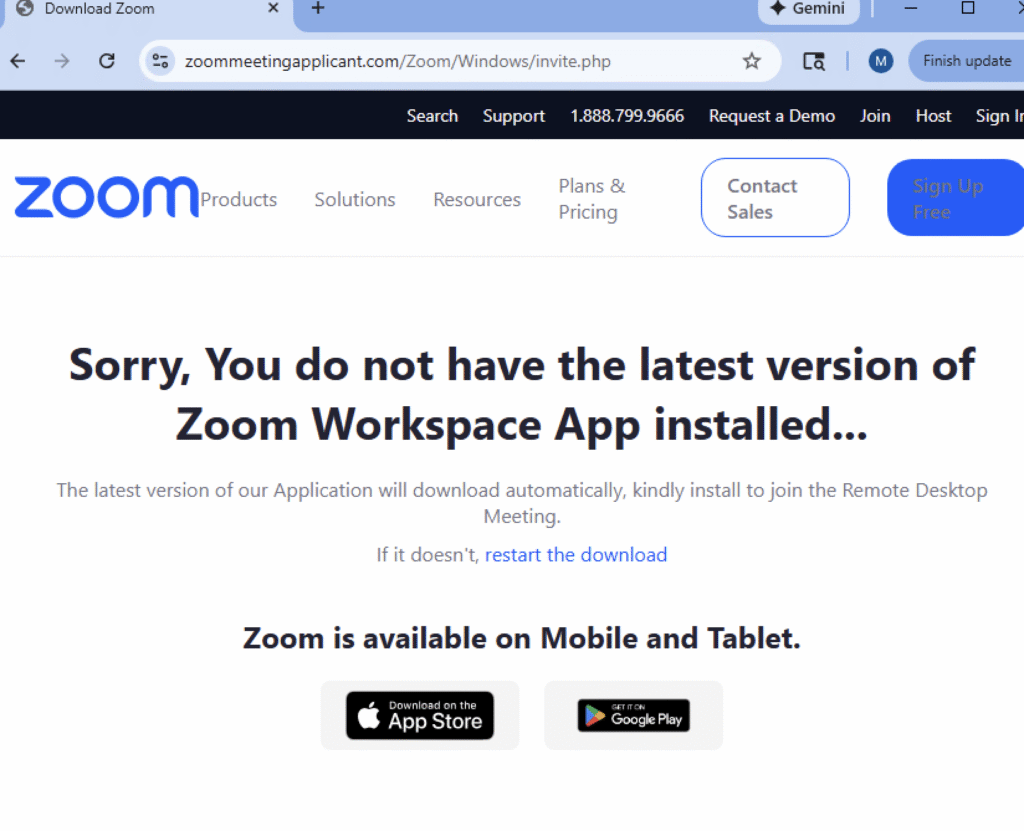
The attackers exploit business urgency and fear of missing important meetings, leading users to bypass typical security caution.
In some cases, the phishing sites even include on-screen installation instructions or progress bars to maintain credibility, guiding victims through the setup process of the fake update in a manner consistent with legitimate conferencing tools.
Once executed, the downloaded file installs a legitimate RMM agent such as Datto RMM, LogMeIn, or ScreenConnect. Some phishing sites even provide steps on how to “install” the software update.
These tools, often pre-approved in enterprise environments, allow remote control, file access, and system management. Because they are digitally signed and legitimate, they can easily evade antivirus detections and endpoint security controls.
Ongoing Threat and Defense Measures
RMM platforms to remotely access compromised systems, steal corporate data, move laterally, and in severe cases, deploy additional payloads such as ransomware.
The use of legitimate, trusted software minimizes the chance of detection and provides persistent administrative access without triggering traditional threat detection mechanisms.
Netskope Threat Labs warns that these campaigns highlight how attackers continue to exploit trust in collaboration tools and remote access software.
Organizations are advised to monitor the use of RMM tools across their networks, restrict administrative privileges, and educate employees about fake update prompts.
IT teams should validate that video conferencing updates come only from official vendor domains and are distributed via secure internal channels.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.


