The pro-Russia crowdsourced DDoS (distributed denial of service) project, ‘DDoSia,’ has seen a massive 2,400% growth in less than a year, with over ten thousand people helping conduct attacks on Western organizations.
The project was launched by a pro-Russian hacktivist group known as “NoName057(16)” last summer, quickly reaching 400 active members and 13,000 users on its Telegram channel.
In a new report released today, Sekoia analysts say that the DDoSia platform has grown significantly over the year, reaching 10,000 active members contributing firepower to the project’s DDoS attacks and 45,000 subscribers on its main Telegram channel (there are seven in total).
Besides the growth in community size, which also translates to more disruptive attacks, DDoSia has also improved its toolset and introduced binaries for all major OS platforms, increasing its reach to a broader audience.
(Sekoia)
Multi-platform payloads
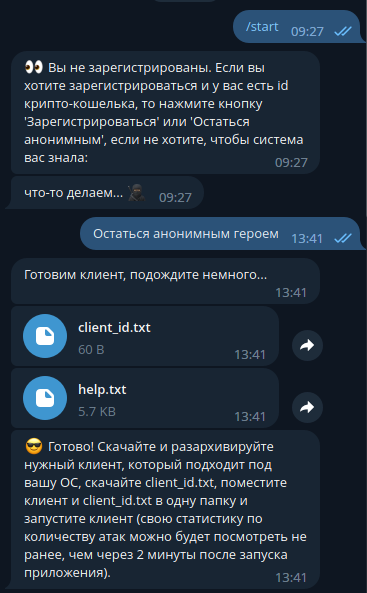
The registration of new users on the platform is fully automated thanks to a Telegram bot, which only supports Russian at the time.
New members start by providing a TON (Telegram Open Network) wallet address to receive cryptocurrency, to which the bot responds by generating a unique client ID and a help text file.
(Sekoia)
Next, the new members receive a ZIP archive that contains the attack tool. As of April 19, 2023, the ZIP included the following files:
- d_linux_amd64 – ELF 64-bit LSB executable, x86-64
- d_linux_arm – ELF 32-bit LSB executable, ARM
- d_mac_amd64 – Mach-O 64-bit x86_64 executable
- d_mac_arm64 – Mach-O 64-bit arm64 executable
- d_windows_amd64.exe – PE32+ executable (console) x86-64 for Microsoft Windows
- d_windows_arm64.exe – PE32+ executable (console) Aarch64 for Microsoft Windows
To execute these payloads, the client ID text file must be placed in the same folder as the payloads to limit unauthorized execution by security analysts or other “intruders.”
The DDoSia client launches a command line prompt that lists the targets fetched by the project’s C2 server in encrypted form and lets members contribute to generating garbage requests directed at them.
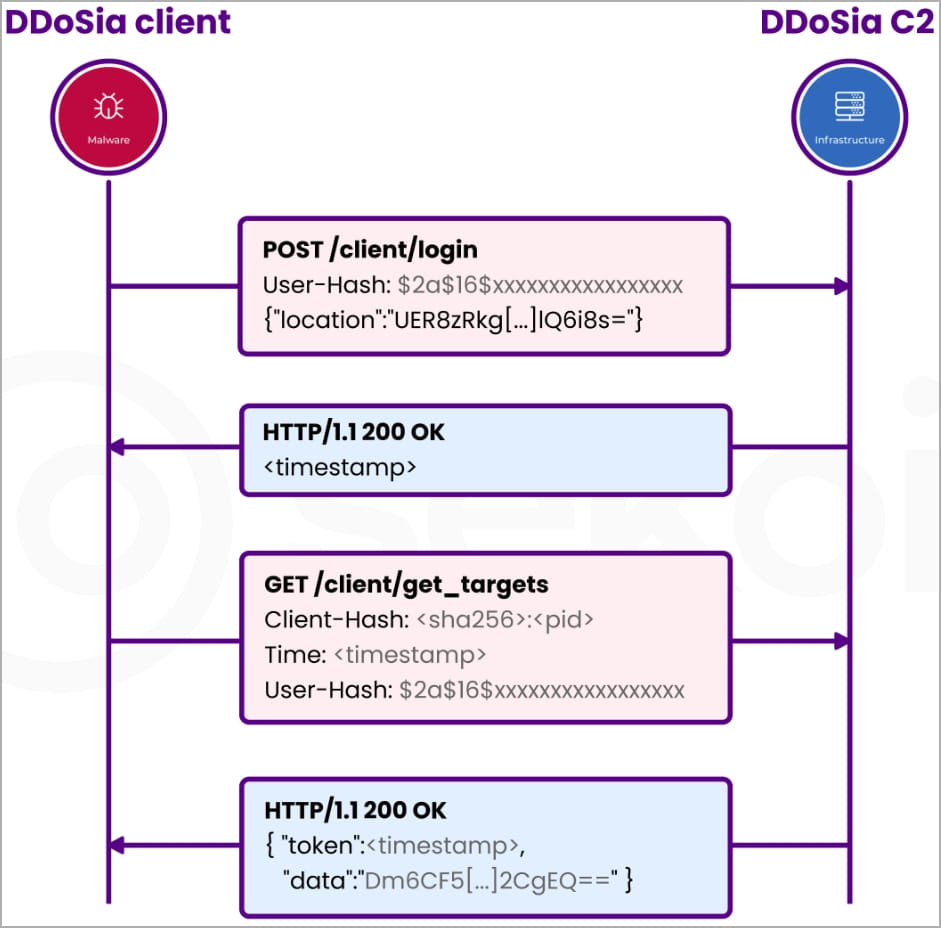
Sekoia reverse-engineered the Windows 64-bit executable and found that it’s a Go binary, using AES-GCM encryption algorithms to communicate with the C2.
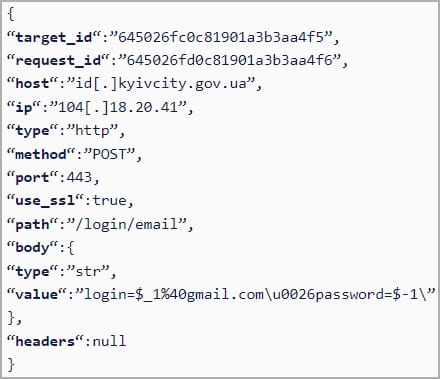
The C2 sends the target ID, host IP, request type, port, and other attack parameters in encrypted form to the DDoSia client, which is locally decrypted.
(Sekoia)
DDoSia targets
Sekoia collected data regarding some targets sent by the DDoSia C2 between May 8 and June 26, 2023, and found that those targeted were mostly Lithuanian, Ukrainian, and Polish, accounting for 39% of the project’s total activity.
This focus of attacks is tied to these countries’ public declarations against Russia, but in general, NoName057(16)’s targets appear to be NATO countries and Ukraine.
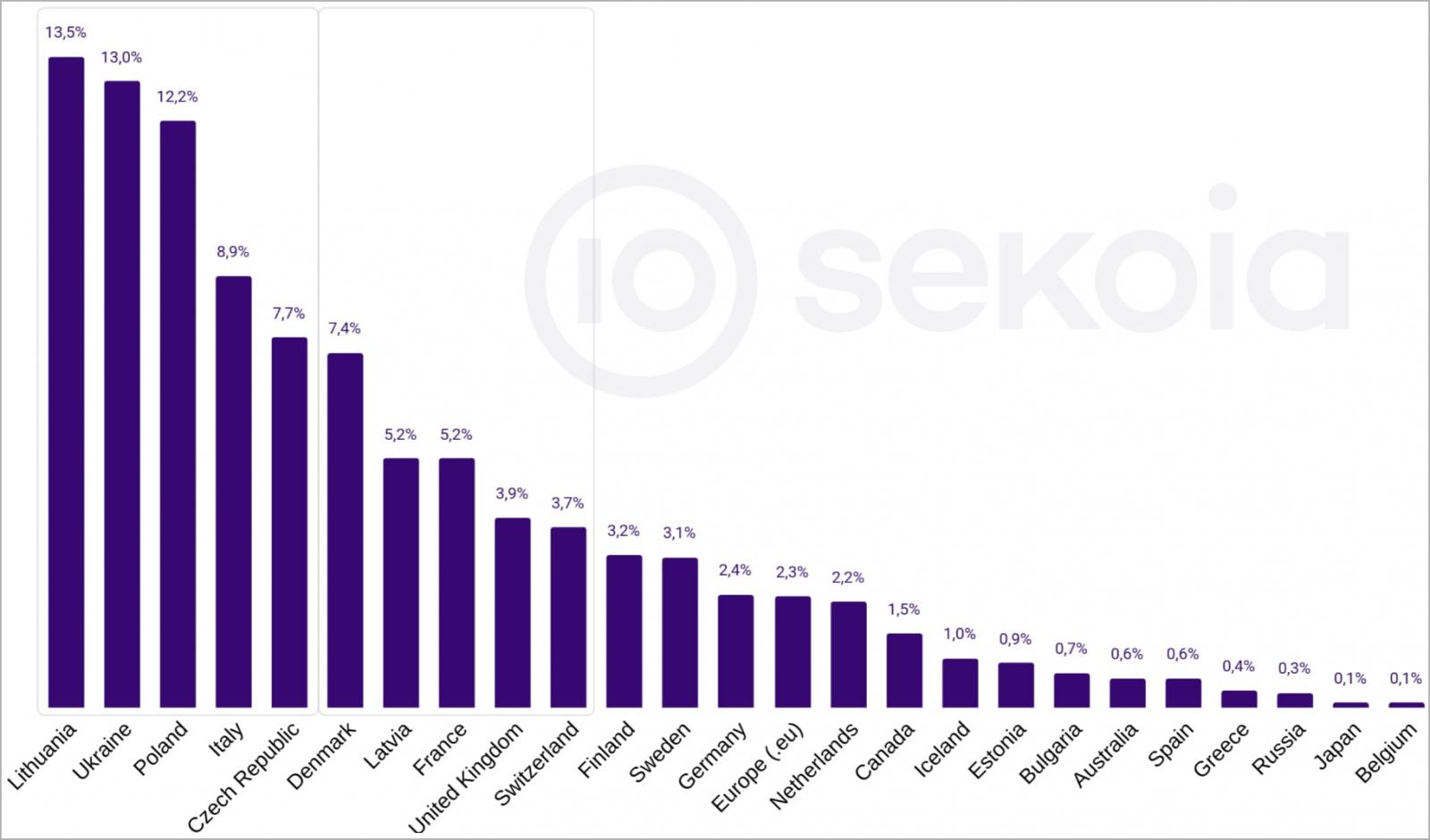
During the mentioned period, DDoSia targeted a total of 486 different websites, and those receiving most of the malicious traffic were:
- zno.testportal.com.ua – Ukrainian education site
- e-journal.iea.gov.ua – Ukraine government electronic journal
- e-schools.info – Ukrainian education support platform
- portofhanko.fi – Website of the Finish port of Hanko
- credit-agricole.com – Website of major French bank Crédit Agricole
- urok-ua.com – Ukrainian education site
- groupebpce.com – Website of major French banking entity Groupe BPCE
NoName057(16) targeted educational platforms in May and early June, likely to disrupt the ongoing exams.
It is also noteworthy that DDoSia set two Wagner sites as its targets on June 24, 2023, the day that the private paramilitary group attempted an offensive against the Russian state.
Also, although DDoSia typically sets an average of 15 daily targets, on June 24, it focused all its firepower on the Wagner sites, treating this case as urgent.
In conclusion, the DDoSia project continues to grow and has reached a large enough size to cause significant problems to its targets.
