Radiant Security helps you harness the power of AI in your SOC to boost analyst productivity, detect real attacks through unlimited in-depth investigation, and rapidly respond to incidents.
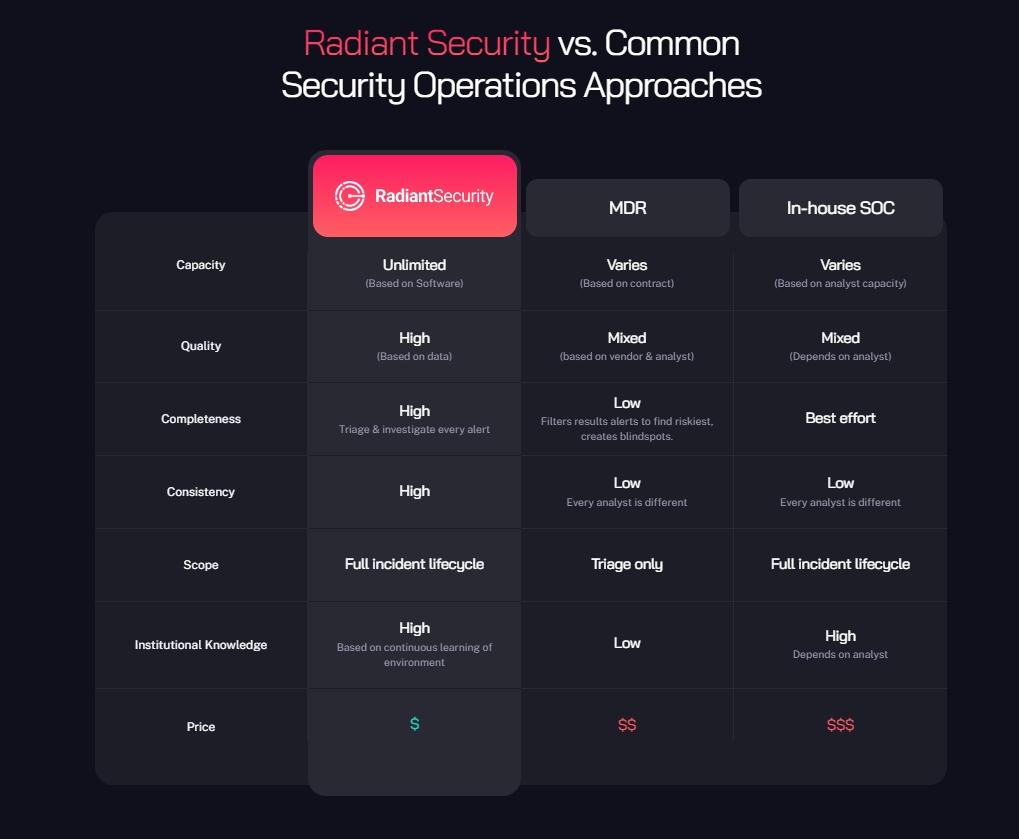
Radiant Security is a platform that enables the SOC to leverage the power of AI to streamline and automate analyst workflows, such as automating alert triage and incident investigation, generating incident specific response plans, and quickly responding to security threats. The benefit of this approach is dramatically improved SOC analyst productivity, detecting more real attacks by deeply investigating every alert, and significantly reduced response times.
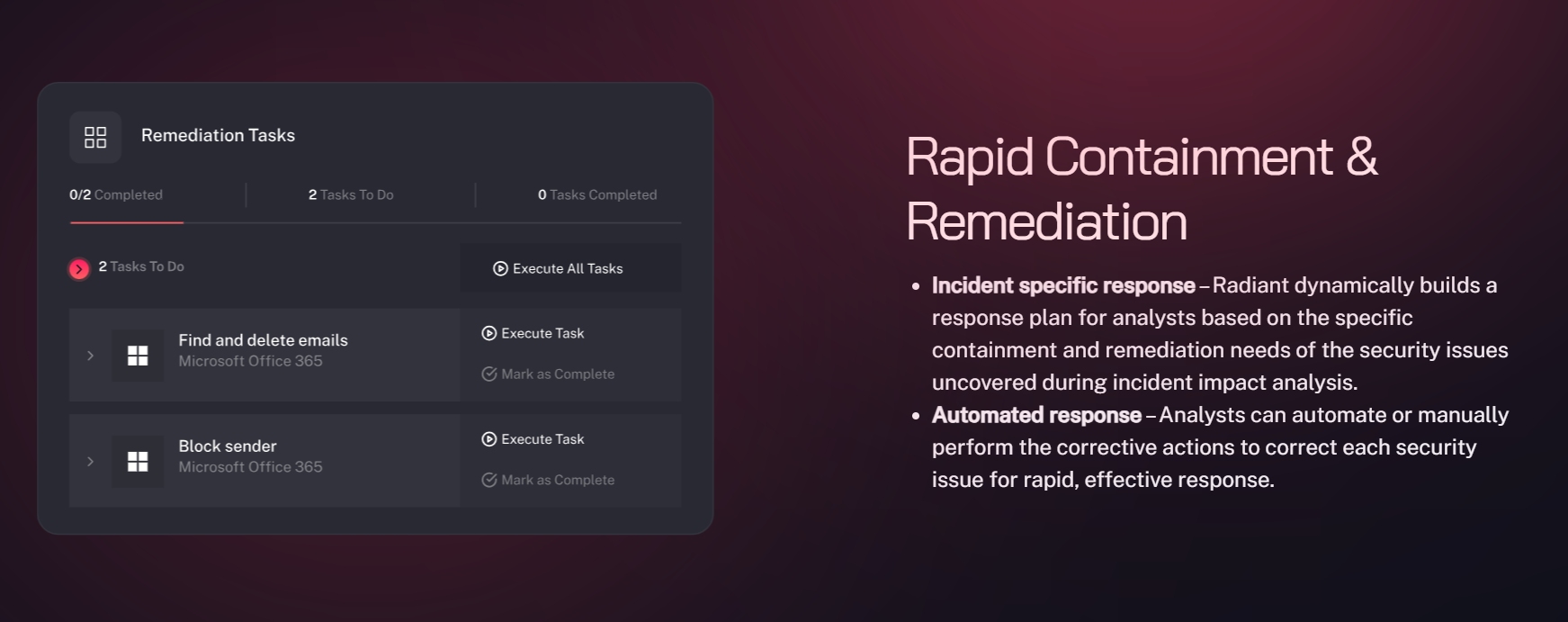
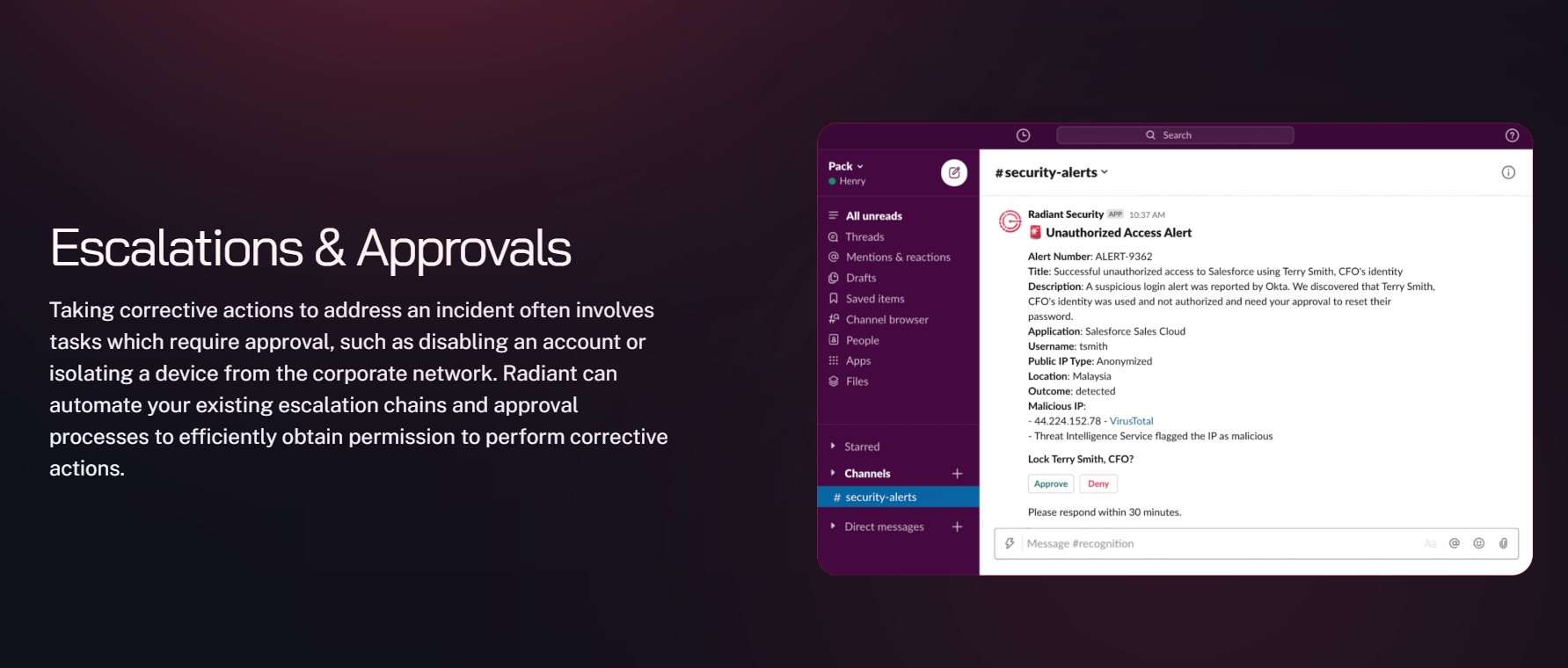
Radiant’s AI-powered co-pilot provides analysts with decision ready results such as identifying malicious alerts, conducting root cause analysis, and identifying the full scope of incidents: including affected users, hosts, applications and more. Radiant also automatically generates a response plan to address each identified security issue, which can be executed manually by analysts, using one-click response actions from Radiant, or in a fully automated mode.
“The potential for AI to revolutionize security operations is tremendous. Today’s SOCs are still largely run with manual effort. When combined with a lack of staff, this means incidents can easily slip through the cracks and develop into breaches. By embracing recent innovations in AI, SOCs have the opportunity to level the playing field with attackers,” said Orion Cassetto, Head of Marketing, Radiant Security.
How Radiant Automates Email Alert Workflows
Radiant automatically triages every email alert and user-reported email with an AI-powered co-pilot, then performs an in-depth impact analysis to determine root cause and uncover the full incident scope. Radiant then auto-remediates the incident and notifies affected users of the incident outcome and corrective steps.
“It was never feasible for SOC analysts to review every alert they received. There aren’t enough hours in the day or analysts in the SOC for this to work. Instead, alerts end up being filtered out or left unaddressed, thus creating blindspots where attacks can go undetected,” remarked Barry Shteiman, CTO and Co-founder of Radiant Security. “SOCs need a way to accurately review every security alert, with the skill of their best analyst—AI makes this possible.”
How Radiant Automates Endpoint Alert Workflows
Radiant automatically triages every endpoint alert with an AI-based engine, then performs an in-depth impact analysis to determine root cause and uncover the full incident scope. Finally, Radiant auto-remediates the incident and notifies affected users of the incident outcome and corrective steps.
“SOCs don’t have the time, and in many cases, the skill needed to perform a proper investigation of every incident,” commented Shahar Ben-Hador, CEO and Co-founder of Radiant Security. “Radiant makes it possible to do just that. And, by deeply scrutinizing every alert, SOCs can find more true threats and get more out of their existing security investments.”
How Radiant Automates Network Alert Workflows
Radiant automatically triages every network alert with an AI-based engine, then performs an in-depth impact analysis to determine root cause and uncover the full incident scope. Finally, Radiant auto-remediates the incident and notifies affected users of the incident outcome and corrective steps.
“With Radiant Security’s co-pilot, we can rest easy knowing that the repetitive and time-consuming work of triaging and investigating security alerts is being taken care of,” commented Josh Lanners, Director, IT Operations & Security at Nutcracker Therapeutics. “Thanks to the visibility provided by Radiant, I trust that any incidents have been fully vetted by the system before they reach me.”
How Radiant Automates Identity Alert Workflows
Radiant automatically triages every suspicious login alert with an AI-based engine, then performs an in-depth impact analysis to determine root cause and uncover the full incident scope. Finally, Radiant auto-remediates the incident and notifies affected users of the incident outcome and corrective steps.
“By using Radiant for triage and investigation, we were able to significantly reduce response times and improve our visibility into the scope of incidents and their affected systems,” commented Mike Butler, Director-Information Security Operations at Spellman High Voltage Electronics Corporation. “Our team no longer has to sift through countless alerts manually and can focus on more strategic initiatives.”
Under the hood Radiant’s co-pilot combines continuous learning of a customer’s normal operating environment, the problem space via data sources like CIS and MITRE ATT&CK, and the learned conclusions from previous incidents—with a decision-making engine. The decision-making engine reviews every alert by replicating the question-and-answer process that security analysts would use to determine if an alert is malicious or not. This means Radiant dynamically selects and performs tests to triage and investigate security alerts instead of relying on static, pre-programed logic or playbooks. The result is highly accurate triage and investigation that can scale indefinitely to handle any volume of alerts.
Learn more at: https://radiantsecurity.ai/
About the Publisher
 Gary Miliefsky is an internationally recognized cybersecurity expert, bestselling author and keynote speaker. He is a Founding Member of the US Department of Homeland Security, served on the National Information Security Group and served on the OVAL advisory board of MITRE responsible for the CVE Program. He founded and is the Publisher of Cyber Defense Magazine since 2012. Visit Gary online at: https://www.cyberdefensemagazine.com/
Gary Miliefsky is an internationally recognized cybersecurity expert, bestselling author and keynote speaker. He is a Founding Member of the US Department of Homeland Security, served on the National Information Security Group and served on the OVAL advisory board of MITRE responsible for the CVE Program. He founded and is the Publisher of Cyber Defense Magazine since 2012. Visit Gary online at: https://www.cyberdefensemagazine.com/
