RansomHouse, a ransomware-as-a-service (RaaS) operation managed by the threat group Jolly Scorpius, has significantly enhanced its encryption capabilities, marking a critical escalation in the threat landscape.
Recent analysis of RansomHouse binaries reveals a sophisticated upgrade from basic linear encryption to a complex multi-layered encryption methodology, demonstrating how ransomware operators continue to evolve their technical sophistication to evade detection and increase extortion effectiveness.
The RansomHouse operation employs a double-extortion strategy that combines data theft with encryption, thereby maximizing pressure on victims.
This approach involves stealing sensitive information before encrypting it, then threatening public disclosure to coerce ransom payments.
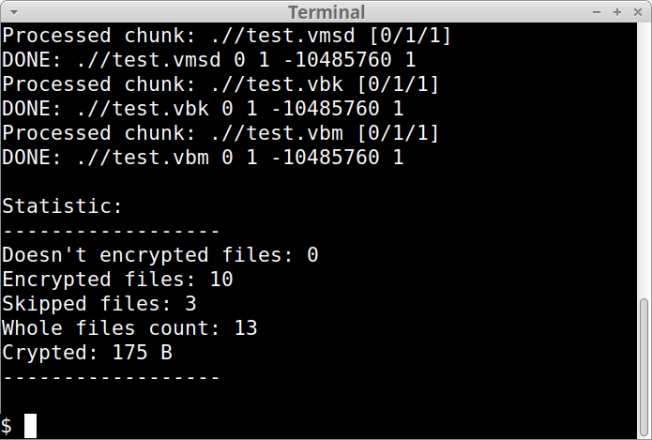
The scale of operations is substantial, with at least 123 victims documented on the RansomHouse data leak site since December 2021.
The group has disrupted critical sectors including healthcare, finance, transportation, and government, causing significant financial losses and severe data breaches that have eroded public trust in affected organizations.
Jolly Scorpius operates RansomHouse through a structured business model involving three distinct roles: operators who maintain the RaaS infrastructure, affiliates who conduct intrusions, and victims.
This organizational framework enables the group to scale operations efficiently. Attackers typically gain initial access through spear-phishing emails or exploitation of vulnerable systems, then use reconnaissance tools to map victim networks, escalate privileges, and identify valuable data for exfiltration.
RansomHouse Enhances Attack Strategy
The group has earned notoriety for targeting VMware ESXi infrastructure, enabling attackers to simultaneously encrypt dozens or hundreds of virtual machines, thereby maximizing operational disruption.
The RansomHouse attack chain consists of four distinct phases: development, infiltration, exfiltration and deployment, and extortion.
The operational infrastructure relies on two primary components: MrAgent, a management tool that automates ransomware deployment across ESXi hypervisors, and Mario, the encryption engine.
MrAgent establishes persistent command-and-control connections, turns off firewalls, and executes remote commands, while Mario performs file encryption targeting virtualization-specific file formats including VMDK, OVF, VBK, and snapshot-related extensions.
The most significant recent development involves Mario’s encryption upgrade. The original version employed straightforward single-pass encryption with fixed-size chunk processing.
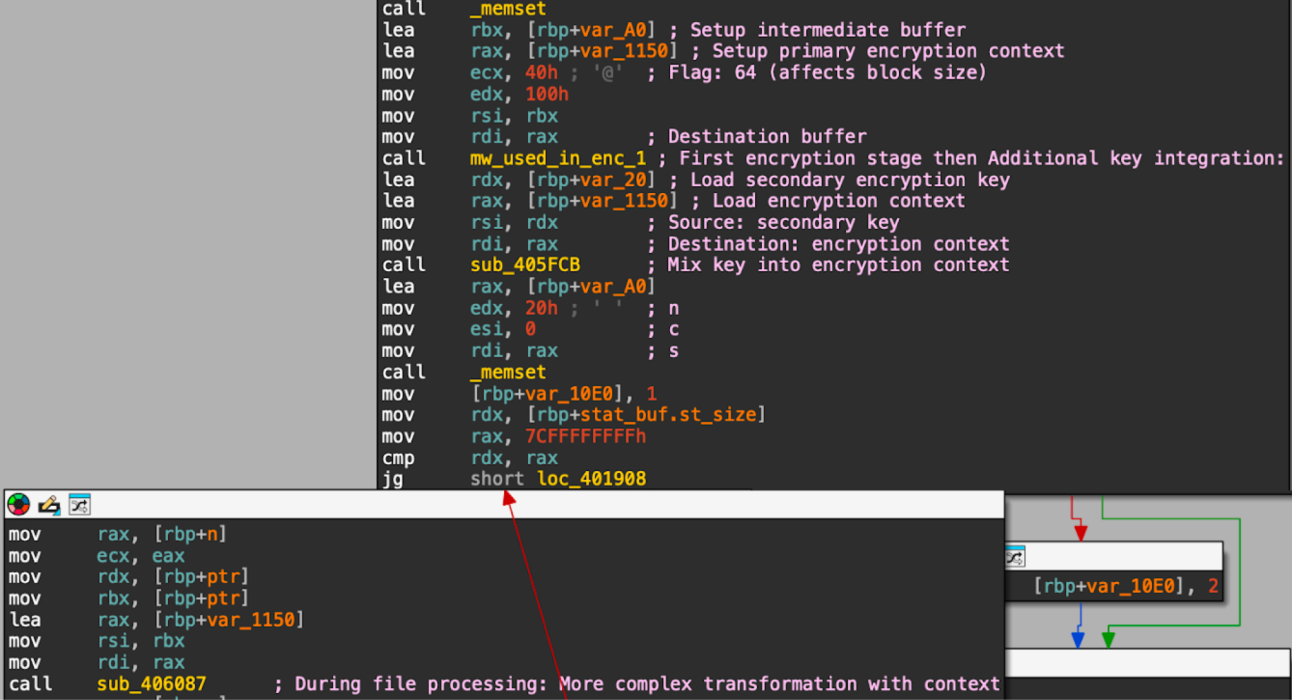
The upgraded version implements a sophisticated two-factor encryption scheme utilizing both primary and secondary encryption keys, substantially increasing decryption difficulty.
This enhancement includes variable segment lengths with 8GB size thresholds, dynamic chunk sizing with complex mathematical formulas determining processing order, and sparse encryption targeting specific file offsets rather than sequential processing.
The upgraded version also employs sophisticated buffer management and enhanced file processing logic that makes static analysis considerably more challenging.
These technical improvements demonstrate how threat actors are deliberately enhancing evasion capabilities. The chunked processing with non-linear file handling and the two-factor encryption scheme represent significant defensive barriers.
Landscape for Cybersecurity
The sophistication of this evolution suggests that RansomHouse operators view these enhancements as proven methodologies likely to influence other ransomware variants.
Mario uses random values to generate a 32-byte primary encryption key and an 8-byte secondary encryption key.
Organizations face escalating threats as ransomware groups adopt these advanced techniques. The combination of double extortion pressure, infrastructure-targeted attacks, and enhanced encryption creates a hazardous threat profile.
Defenders must implement comprehensive strategies including network segmentation, ESXi hardening, advanced threat detection, and robust backup strategies maintained offline.
The RansomHouse upgrade underscores the urgent need for dynamic, adaptive security strategies capable of countering next-generation ransomware threats that continue to evolve rapidly and sophisticatedly.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
